As the threat landscape evolves, it presents ever-increasing risks and costs driven by progressive factors like financial incentives for threat actors, the availability of malware, expanding attack surfaces, and the sophisticated capabilities of generative AI. Of the latter, enterprises adopting AI solutions are doing so rapidly, and often without full awareness or consideration of the risks involved.
AI is exposing an attack surface layer that previously hadn’t been considered. The availability of generative AI systems and large language models (LLM) like ChatGPT in enterprise environments presents many risks. Perhaps the most dangerous example is indirect and direct prompt injection attacks, which can be used to override LLM controls to generate malware and fuel sophisticated social engineering attacks. Additionally, adversaries can leverage AI technologies to accelerate the development and scale of increasingly sophisticated attacks capable of evading security tool detection, including fileless and in-memory attacks.
Alongside these increasingly sophisticated threats a rudimentary technique continues to drive many modern-day attacks. According to the 2023 Verizon Data Breach Investigations Report, vulnerability exploitation remains one of the top three techniques attackers use to gain access to an organization. That’s concerning, especially as the number of common IT security vulnerabilities and exposures (CVEs) worldwide is expected to rise by 25% this year, reaching 34,888 vulnerabilities, or approximately 2,900 per month.
Increasing vulnerability volumes are compounded by telemetry noise and limited resources; research indicates that organizations typically have the capacity to address only about one out of every 10 vulnerabilities in their environment within a given month. This perpetuates a reactive approach that significantly increases an organization’s risk of breach, system downtime and costly damages.
Vulnerability exploitation isn’t new, yet current exposure management tools and technologies lack the proactive and preventative capabilities that teams need to prioritize vulnerability remediation effectively and efficiently. Recognizing this, organizations are turning their attention to Continuous Threat Exposure Management (CTEM) to contain the attack surface.
CTEM is a systematic approach and program used to identify, assess, and mitigate attack vectors and security risks linked to digital assets.
However, pinpointing and prioritizing vulnerable digital assets with accuracy poses a challenge for IT and security teams juggling resource limitations, process inefficiencies, and an overwhelming influx of telemetry data.
The current situation is unsustainable both from the perspective of business continuity, and larger risk management.
Reducing the attack surface with CTEM
CTEM is a top cybersecurity priority this year.
Gartner® shares that: "By 2026, Organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach."1

In recent years, enterprise teams have focused on implementing CTEM by enhancing vulnerability management, particularly by increasing the speed and quantity of patching, and improving the efficiency of breach detection and response. But despite these efforts cyber risk and cyber-attacks continue to climb.
According to Gartner: “Enterprises fail to reduce their patchable and unpatchable exposures to threats, yet keep implementing siloed and narrow remediation processes. IT leaders must implement continuous and repeatable exposure management processes, optimizing short-term response and longer-term security posture.”2
It’s a juncture that has most cybersecurity practitioners asking three critical questions:
- Are my systems vulnerable?
- Are my security controls working properly?
- What actions should I prioritize first?
Gartner recommends that: “Security and risk management teams progressively add notions of the CTEM framework to their existing practices.”2
Per Gartner, “CTEM is a systemic approach to continuously refine cybersecurity optimization priorities. Its objective is to design actionable security exposure remediation and improvement plans that business executives can understand, and that architecture teams can act on.”2
A full CTEM cycle defines five key stages:
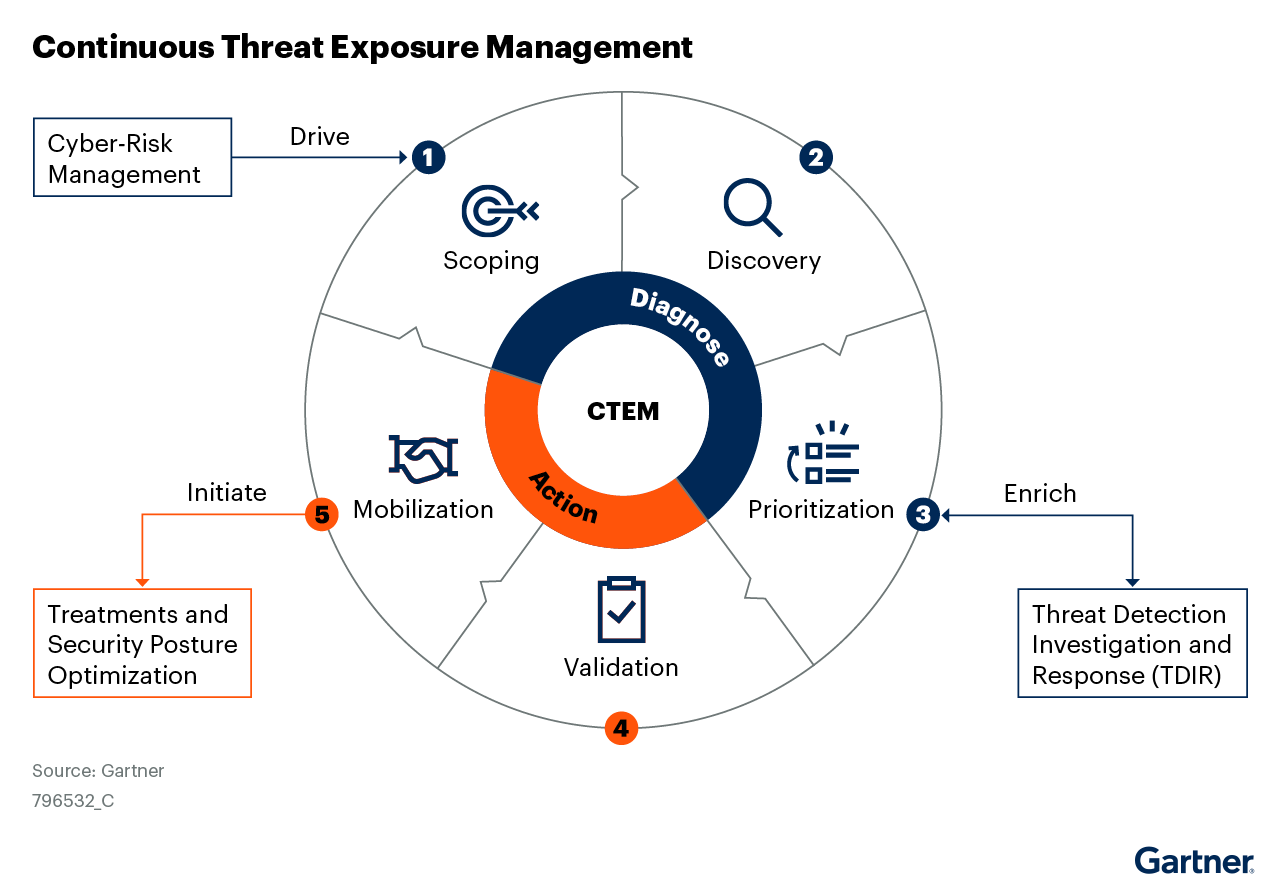
Image source: Gartner2
- Scoping — Aligning assessments to key business priorities and risk.
- Discovery —Identifying various elements within and beyond the business infrastructure that could pose risks in a comprehensive way.
- Prioritization — Identifying threats with the highest likelihood of exploitation and flagging which could have the most significant impact on the organization.
- Validation — Validating how potential attackers could exploit identified vulnerabilities or exposures.
- Mobilization — Ensuring all stakeholders are informed and aligned toward risk remediation and measurement goals.
Gartner says: “Continuous threat exposure management (CTEM) is an umbrella program for forward-looking and sustainable approaches to exposure reduction. Implementing CTEM enables closer alignment to business needs and risk impact. CTEM involves business leadership in identifying key assets and processes to defend against cyberattacks/business disruption.”2
Applying Adaptive Exposure Management to strengthen CTEM programs
While many of the solutions available today may align with the CTEM framework, there's an assumption that technologies and strategies will seamlessly work together and remain constant. However, the reality is quite different, especially when it comes to cyber warfare.
In today's cybersecurity landscape, critical use cases such as the expanding attack surface, security control gaps, and sophisticated threats like ransomware underscore the dynamic nature of enterprise security. Each action — like downloading unauthorized software, using AI and LLM tools, adding a new device, or an unintentional misconfiguration — has a ripple effect, constantly reshaping the attack surface and an organization’s security posture in unpredictable ways.
Rudimentary attack techniques and imminent and future AI-driven attack methods alike must rely on adaptive defense strategies that include AMTD as a core component of Adaptive Exposure Management solutions. Adaptability is key to ensuring cyber resilience.
For example, the concept of "self-healing endpoints," demonstrates adaptable capabilities and components working in unison, and in real-time. This concept involves an endpoint's capability not just to identify when it's compromised but also to autonomously act. This action includes isolating the threat, eliminating it, and restoring any impacted systems to their pre-attack condition. At its core, self-healing relies on the endpoint's ongoing ability to adjust its exposure. This is facilitated through Automated Moving Target Defense (AMTD), which continually shifts and morphs the attack surface to thwart exploitation.
By optimizing CTEM with an adaptive approach, teams can effectively respond to ever-evolving challenges in real-time. This preventative stance empowers organizations to stay ahead of the curve, addressing threats proactively, rather than reactively managing damage control.
How Morphisec can help
Developed in alignment with CTEM framework, Adaptive Exposure Management is a component of Morphisec’s Anti-Ransomware Assurance Suite.
Adaptive Exposure Management represents a significant advancement in the field of cybersecurity, evolving beyond traditional exposure management approaches by introducing a dynamic and proactive strategy. Unlike linear models which often operate on static assessments and periodic updates, Adaptive Exposure Management continuously adjusts to the rapidly changing threat landscape.
This approach is particularly crucial in today's environment where threat actors employ advanced, sophisticated, and evasive techniques that can bypass conventional security measures. By incorporating continuous real-time monitoring and the application of technologies like Automated Moving Target Defense (AMTD), Adaptive Exposure Management can anticipate changes and vulnerabilities in an organization's digital infrastructure. This capability allows it to respond instantly to new threats and anomalous behaviors, thereby preventing potential breaches before they materialize.
Essentially, Adaptive Exposure Management empowers organizations to stay one step ahead, ensuring cyber resilience by adapting to threats and changes as they occur, and not merely reacting to them after the fact. This constant state of vigilance and adaptation aligns closely with the needs of modern enterprises facing diverse and unpredictable cyber threats.
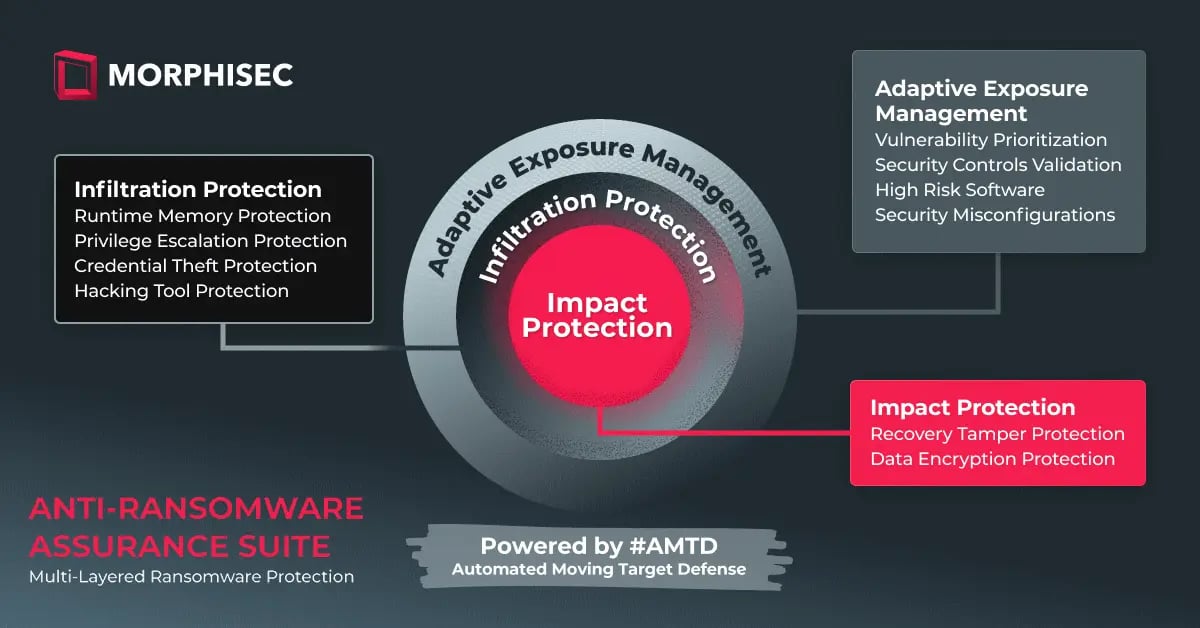
Powered by Morphisec’s pioneering Automated Moving Target Defense (AMTD) technology, Adaptive Exposure Management zeroes in on security weaknesses and continuously adjusts to address new threats. Key benefits include:
- Assurance: Protection, even when other safeguards fail, ensuring uninterrupted cyber defense. Morphisec provides a piece of mind that your systems are safe.
- Total Cost of Ownership (TCO): By preventing threats as early as possible and classifying them accurately, Morphisec significantly reduces the time and costs for tech resources as well as the financial impact.
- Enhanced Visibility: Morphisec sheds light on shadow IT, misconfigurations, and high-risk software, revealing critical issues that may have gone undetected, thus mitigating potential impacts on your organization.
- Defense-in-Depth: The implementation of AMTD provides a multilayered defensive approach that enhances cyber-resilience against unknown evasive threats.
- Improved Cybersecurity Posture: Morphisec boosts audit scores and helps in achieving compliance, which can contribute to reduced cyber insurance premiums, thus enhancing the overall cybersecurity posture.
- Operational Readiness: Morphisec enhances team efficiency and effectiveness by eliminating attack dwell time and recovery efforts through proactive prevention. System hardening and virtual patching free up resources, allowing teams to concentrate on critical tasks instead of routine patching.
Adaptive Exposure Management from Morphisec optimizes CTEM programs, delivering a single source of truth for exposure and cyber risk discovery, prioritized actions to optimize resources on the most critical exposures, and compensatory controls, including virtual patching and ransomware prevention and other advanced attacks with AMTD.
Book a demo to see how Adaptive Exposure Management from Morphisec can support your CTEM strategy.
1Gartner: Implement a Continuous Threat Exposure Management (CTEM) Program, Published 11 October 2023, Jeremy D'Hoinne, Pete Shoard, Mitchell Schneider
2Gartner: Top Strategic Technology Trends for 2024: Continuous Threat Exposure Management, Published 16 October 2023, Jeremy D’Hoinne, Pete Shoard
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.





.png?width=571&height=160&name=iso27001-(2).png)