Recently, Morphisec researchers discovered a vulnerability in Microsoft Outlook that can lead to remote code execution (RCE). This vulnerability, identified as CVE-2024-38021, highlights a significant security flaw within the Microsoft Outlook...
Read MoreMorphisec Labs has been monitoring increased activity associated with Sticky Werewolf, a group suspected to have geopolitical and/or hacktivist ties. While the group’s geographical origin and home base remain unclear, recent attack techniques...
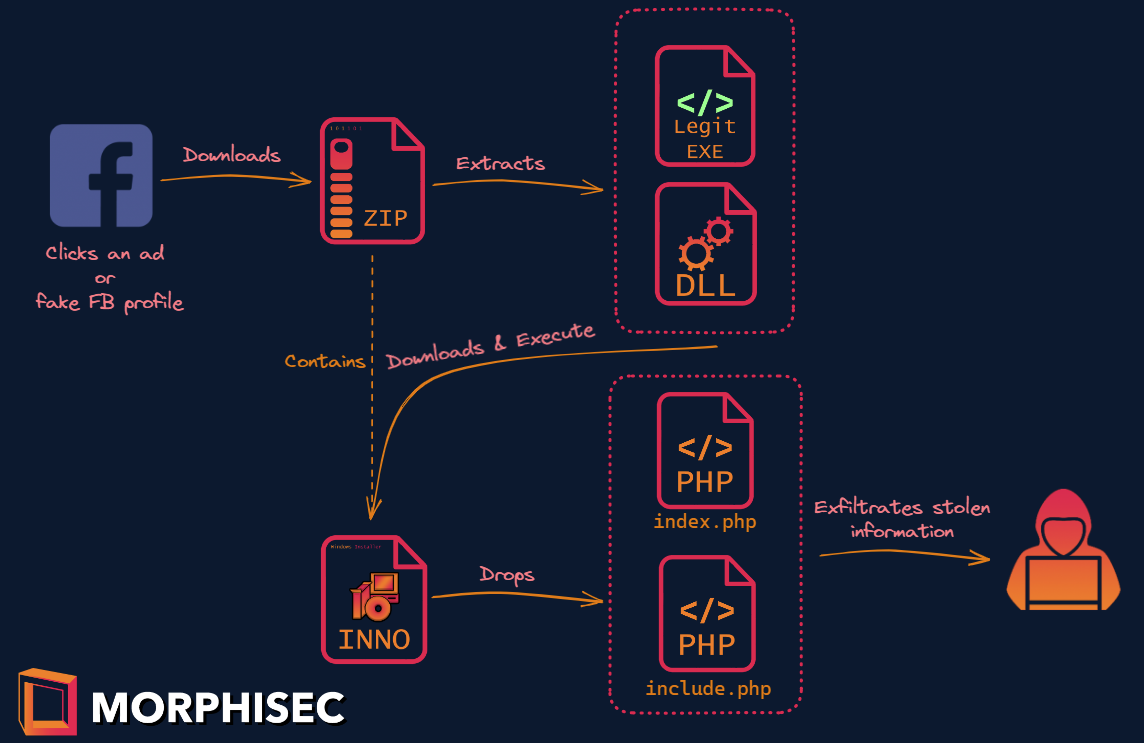
Read MoreRecently, Morphisec Labs identified a significant increase in activity linked to Mispadu (also known as URSA), a banking trojan first flagged by ESET in 2019. Initially concentrated on LATAM countries and Spanish-speaking individuals, Mispadu has...
Read MoreIn ongoing efforts to monitor and analyze emerging cyber threats, Morphisec Threat Labs has recently turned its focus to Chae$ 4.1, an update to the Chaes malware Infostealer series. This version introduces key updates, including an improved Chronod...
Read MoreStarting in November 2022, Morphisec has been tracking an advanced info stealer we have named “SYS01 stealer.” SYS01 stealer uses similar lures and loading techniques to another information stealer recently dubbed S1deload by the Bitdefender group,...
Read MoreThe Morphisec Labs team has conducted research on the new Mars infostealer. Mars is based on the older Oski Stealer and was first discovered in June 2021. The new Mars is available for sale on several underground forums and is reported to be under...
Read MoreOverview
- Morphisec Labs tracked a new MirrorBlast campaign targeting financial services organizations
- MirrorBlast is delivered via a phishing email that contains malicious links which download a weaponized Excel document
- MirrorBlast has low...
The Morphisec Labs team has been tracking an ongoing RAT delivery campaign that started in February this year. This campaign is unique in its heavy use of the AutoHotKey scripting language—a fork of the AutoIt language frequently used for testing...
Read MoreAn Infostealer is a trojan that is designed to gather and exfiltrate private and sensitive information from a target system. There is a large variety of info stealers active in the wild, some are independent and some act as a modular part of a...
Read MoreIntroduction
Morphisec Labs has tracked a massive maldoc campaign delivering the QakBot/QBot banking trojan, starting earlier this month. Qakbot leverages advanced techniques to evade detection and hamper manual analysis of the threat. In this post...
Read MoreThe Morphisec Labs team has tracked an obfuscated VBScript package in campaigns since March 2020. Initially, the malware campaign was focused on targets within Germany, but has since moved on to additional targets--excluding any IP address within...
Read MoreUrsnif/Gozi Introduction:
Morphisec has been tracking an uptick in the delivery of Ursnif/Gozi during the COVID-19 pandemic. Specifically, we have noticed a significant spike both in numbers and sophistication. The latest delivery methods will many...
Read MoreGuloader is a downloader that has been widely used from December 2019. Several security researchers have identified the downloader in the wild, signifying that it has quickly gained popularity among threat actors. When it first appeared, GuLoader...
Read MoreFollowing the increase in Parallax RAT campaigns -- the new RAT on the block, Morphisec Labs decided to release more technical details on some of the latest campaigns that the Morphisec Preemptive Cyber Defense Platform intercepted and prevented on...
Read MoreThe Trickbot trojan is one of the most advanced malware delivery vehicles currently in use. Attackers have leveraged it to deliver a wide variety of malicious code, in many different methods. Just yesterday, Bleeping Computer reported that news...
Read MoreA whopping 186.4 million Americans shopped in stores and online between Black Friday and Cyber Monday this year, according to the National Retail Federation. On average, these shoppers spent $361.90 per person over the five-day Thanksgiving weekend.
Read MoreLast week, a new strain of ransomware hit dozens of targets across Germany. The categorization as ransomware is really a misnomer as, while the attackers do demand a ransom, by that time the victim’s data has already been irreversibly wiped, even if...
Read MoreMorphisec Labs recently investigated an ongoing BitPaymer ransomware campaign that has been attacking companies across the U.S., both public and private, over the last 3 months.
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (126)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Financial Cybersecurity (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)























.png?width=571&height=160&name=iso27001-(2).png)