Fileless malware attacks are a malicious code execution technique that works completely within process memory. In a fileless attack, no files are dropped onto a hard drive. With no artifacts on the hard drive to detect, these attacks easily evade detection-based cybersecurity solutions like next generation anti-virus (NGAV), endpoint protection platforms (EPP), and endpoint detection and response (EDR, XDR, MDR).

In fact, attackers are getting more adept at using common tools to bypass endpoint detection. Earlier this year reports found that attackers started weaponizing EDRSilencer, a popular red team tool. Using such tools allows attackers to “mute” detection technology while deploying attacks.
What is a fileless malware attack?
Also known as in-memory attacks, fileless malware attacks have existed for over a decade. Initially, they posed a limited threat as they were rare and could be removed upon system reboot. This changed in 2014 with Poweliks, a click-fraud Trojan that was the first fileless malware to demonstrate persistence functionality. Today, fileless techniques are part of every cybercrime group’s arsenal and present one of the most dangerous threats to every organization.
Script-based malware is also considered a type of fileless malware as it does not drop any portable executable files (PE) on disk. It’s not 100 percent fileless, however, since it does drop script-based interpreted files such as JavaScript, HTA, VBA, PowerShell, etc. It's executed using legitimate Windows processes which make it exceedingly difficult to detect.
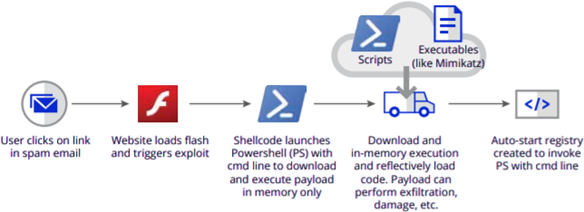
Execution chain of a fileless malware, source: Trellix
Why can’t EDRs and other endpoint security software detect fileless malware?
Detection-based security solutions like EDRs use several techniques to find and detect malicious activity.
Static analysis is used to examine files and software without actually executing them. When it works, it enables faster analysis and earlier detection without risking activating malicious code and damaging systems. Static analysis techniques usually rely on examining files, code, or binaries to identify potential threats. Since fileless malware doesn't use traditional files, there is no static content to analyze, making it extremely difficult to detect the presence of malware.
Dynamic analysis observes the behavior of software or files during execution, which generally makes it more effective at detecting fileless malware than static analysis. However, dynamic analysis still has challenges in detecting fileless malware. Dynamic analysis is resource intensive, so it's often executed within controlled environments such as sandboxes or virtual machines. This leads to sandbox-aware malware and misleading classification of threats as legitimate operations. Furthermore, dynamic analysis is designed to monitor behavior during execution. Fileless malware working directly in memory will still evade detection if an analysis tool does not specifically monitor memory-related activities, or if malware employs sophisticated techniques to hide its presence in memory. Attackers often leverage legitimate tools and processes. This makes it difficult for dynamic analysis to differentiate between legitimate and malicious activities carried out by these tools.
The liberal application of allowlisting (previously known as whitelisting) solutions does help to limit execution of legitimate tools such as interpreters by groups of users. But at the cost of limiting an organization’s operational flexibility. Moreover, we see a clear pattern of attackers inventing new patterns to bypass allowlisting solutions on a weekly basis. So why does script execution detection often fall under the category of challenges in fileless malware detection?
- Should we scan .txt files, .sct files, .xml files? These can all potentially be malicious script files, so where do we stop?
- While we have a clear understanding of executable software and its standard loading behavior, each interpreted language has its own structure and behavior. Should we build a parser/interpreter for each type of interpreted file? Anyone can decide on a new interpreted language, so where do we stop?
- Should we block any suspicious string, even a comment in a report?
This is why some security vendors limit static scanning to a specific type of interpreted file and dynamic detection to a specific set of software interpreters. Even then, they struggle to scan those files because of easily available obfuscation options.

Other Types of Fileless Techniques
Some popular techniques implemented by fileless—living-off-the-land malware include:
Windows registry manipulation: Code is usually written and executed directly from the registry by a regular Windows process. This helps to achieve goals like persistence, bypassing allowlisting, and static analysis evasion.
Memory code injection: Allows malware to exist solely within process memory while processes are running on the system. Malware distributes and re-injects itself into legitimate processes critical to normal Windows operational activity, so it can’t be allowlisted or even scanned. Security vendors need a proper justification to kill, block, or quarantine such a process, making this extremely attractive for hackers. Code injection techniques include remote thread injection, APC, atom bombing, process hollowing, local shellcode injection, reflective loading, and many others.
Script-based: As mentioned, this is not a 100 percent fileless technique, but it creates similar issues for detection solutions and is a preferred method for maintaining stealth.
Packers: Packing is a legitimate way to compress an executable. Essentially, it’s in-memory self-modifying code that alters the memory state of a process. But this technique is used by many malware families for signature re-creation and, more importantly, dynamic detection evasion. Packing can also be used as a code injection method by rewriting an existing executable and recreating its code after decryption and remapping the new functionality.
Packing is used by both file-based and fileless malware.
Nevertheless, the detonation/unpacking process is a fileless process. Malware often hides its real API and functionality by encrypting the functions and execution of a position-independent code (shellcode/loader/decryptor). This code doesn’t use much of the declared API and usually performs reflective loading of the next stage’s malicious library.
We call this technique fileless because it runs malicious code created purely in memory without writing to the disk. A lot of known malware heavily uses packing and local code injection techniques to evade static analysis, including Emotet, Revil, Qakbot, IceID, Vidar, and others.
In 2023, research found a 1,400% year-over-year increase in fileless attacks. Last year, fileless attack techniques like process injection were among the most commonly reported MITRE ATT&CK techniques.
The rise of fileless malware attack chains is something security teams need to take extremely seriously. Here's why.
Undetectable Threats Extend Dwell Times
All types of fileless malware attacks share one thing in common: they are extremely hard to detect.
As fileless attacks become more popular among cybercriminals, the time it takes security teams to detect compromise is vital to stopping threats before they can do damage. Surprisingly, research found that the average dwell time for threats decreased in the last year, falling by nearly 1 week, from 16 days in 2022 to 10 days in 2023. However, ransomware attacks spurred by fileless malware continue to increase. The median dwell time for attacks that lead to ransomware deployment or data exfiltration is now around 34 days.
Many fileless threats can linger even longer. Morphisec's incident response team has found fileless malware persisting in remote endpoints waiting for months for an opportunity for lateral movement before being detected.
Fileless Malware Attacks Do More Damage
According to a study by the Ponemon Institute, fileless attacks are ten times more likely to succeed than other attacks. Since they are more likely to succeed, they’re more potentially devastating since attackers have an opportunity to compromise greater parts of infected systems.

The 2021 attack on the Irish Health Service Executive (HSE) is a perfect example. On March 18, 2021, the Conti ransomware group used a phishing email with a malicious Excel macro attached to penetrate an endpoint in the HSE network. Then, using a compromised version of the pen-testing tool Cobalt Strike, Conti operatives moved laterally through the HSE's network before deploying ransomware on May 14—eight weeks later.
This resulted in Conti exfiltrating 700GB of unencrypted data, including protected health information (PHI), and led to ransomware infecting tens of thousands of endpoints and servers. Conti shut down an entire health service IT network serving over five million people for a week, creating massive disruption. The HSE only resolved the issue after Conti released a decryption key.
The ransomware group used a similar attack method to shut down the entire Costa Rican government and hold it to ransom.
Fileless backdoors like Cobalt Strike are increasingly accessible. And cybercriminals are using these kinds of nation-state crippling tactics in attacks against many other targets, including SMBs.
How to Reduce Fileless Malware Attack Risk
Fileless malware attacks are mostly undetectable. They’re carefully designed to bypass detection-and-response cybersecurity tools like NGAV, EPP, and EDR/XDR/MDR.
As fileless malware attacks continue to increase, organizations relying on detection-based tools are much more exposed than they may have thought. For organizations to reduce this risk requires making their network environments inhospitable to fileless threats.
For instance, it's important to segment networks and implement strict access controls to create barriers to the permissionless data flows within networks that fileless threats exploit. I.e., implement a zero-trust strategy. It also means deploying preventive technology like Automated Moving Target Defense (AMTD) that shuts down the attack pathways threats use at the application level.
AMTD is an innovative technology that stops threats without needing to detect them. It randomly morphs the runtime memory environment to create an unpredictable attack surface, and leaves decoy traps where targets were. Trusted applications are updated with the changed memory environment, while any code that tries to execute against a decoy triggers that process to be terminated and trapped for forensic analysis. Because of its deterministic, preventive approach, AMTD is one of the only technologies that reliably stops fileless attacks and other advanced threats like supply chain attacks and that prevent ransomware.
Preventing Fileless Malware Attacks with Preemptive Cyber Defense
Preemptive cyber defense aims to anticipate and counter potential threats before they materialize. This approach focuses on staying ahead by avoiding, outsmarting, or neutralizing threats early, rather than reacting after an attack has taken place—a common limitation of reactive defenses.
The benefits of preemptive defense are compelling: stopping cyberattacks before they can inflict harm, rather than dealing with the aftermath. By adopting a proactive stance, organizations can build a flexible and comprehensive security framework that scales and adapts to evolving threats, regardless of which attack methods dominate at any given time.
As Gartner® notes: “Preemptive cyber defense technologies help organizations improve their ability to defend against AI-enabled threat actors, advanced malware, zero-day vulnerabilities, ransomware, and related threats. These threats typically cannot be fully mitigated with a traditional ‘detect-and-respond’ approach alone.”
AMTD reinforces this by introducing constant change to key system elements, creating an environment of uncertainty for attackers. By frequently altering system attributes, AMTD disrupts the reconnaissance and planning stages of an attack, making it challenging for adversaries to locate and exploit vulnerabilities.
This ongoing change forces attackers to expend more resources and time, increasing their likelihood of detection or failure before they can execute a successful attack. AMTD is especially effective against advanced threats like fileless, in-memory attacks, zero-day exploits, and advanced persistent threats (APTs), which rely on detailed knowledge of stable system environments.
 to learn more about how you can improve your organization’s threat defense with preemptive measures and emerging technology like AMTD.
to learn more about how you can improve your organization’s threat defense with preemptive measures and emerging technology like AMTD.
Gartner®, Emerging Tech: Build Preemptive Security Solutions to Improve Threat Detection (Part 1), Luis Castillo, Carl Manion, 7 October 2024
GARTNER® is a registered trademark and service mark and Hype Cycle is a registered trademark of Gartner®, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner® does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner® research publications consist of the opinions of Gartner®’s research organization and should not be construed as statements of fact. Gartner® disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.





.png?width=571&height=160&name=iso27001-(2).png)