
Guloader is a downloader that has been widely used from December 2019. Several security researchers have identified the downloader in the wild, signifying that it has quickly gained popularity among threat actors. When it first appeared, GuLoader was used to download Parallax RAT, but has been applied to other remote access trojans and info-stealers such as Netwire, FormBook, and Tesla.
Recently, the Morphisec Labs team noticed the downloader spreading in a targeted phishing email against a major bank. Although Parallax RAT was among the first malwares used with GuLoader, we noticed this particular campaign had Remcos RAT as the final payload. GuLoader is considered one of the most advanced downloaders, written in Visual Basic, and this often makes it difficult to scan for static analysis.
In this blog post, we are going to cover GuLoader’s internals. This includes its shellcode, evasion techniques, and its delivery mechanism.
Technical Analysis: (2d6720ae866875b42601951eb3c9421fa2d5b7f0)
The first stage in this campaign is an email that claims it’s a payment invoice. This email contains a ZIP file attachment; as with other phishing emails, the goal is to get the target to download the attachment and open the file. The email appears as part of a chain, which makes it more likely for the target to open the attachment when it’s received.
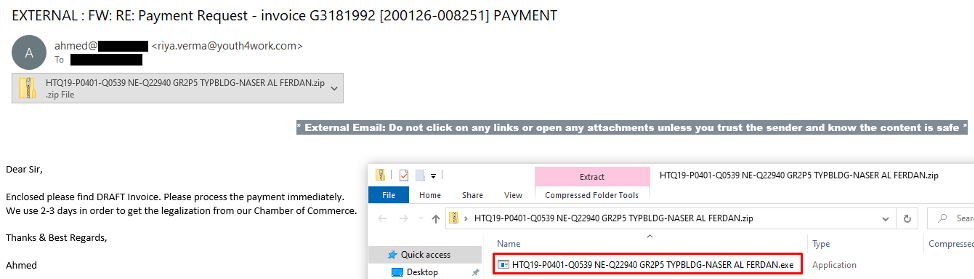
Figure 1: The email pretends to be a payment request.
The ZIP file attachment contains a VB6 executable that stores an encrypted shellcode. The shellcode is XORed with a 4 byte key and then executed. Jason Reaves (@sysopfb) wrote an unpacker for this stage, allowing us to see the URLs for GuLoader.
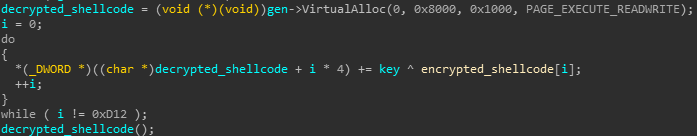
Figure 2: Decrypting and executing the shellcode.
GuLoader Shellcode
GuLoader has some strong evasive characteristics in its shellcode, with several anti-debugging tricks in order to make it harder for defensive solutions to analyze it. These include:
- Anti Attach: In order to prevent a debugger from attaching to the process, the malware’s authors hook DbgBreakPoint and DbgUiRemoteBreakin. Attackers usually hook those functions with a jump to the “ExitProcess” function. In this case though, it is just nop’s or it jumps to an invalid address to crash the program.
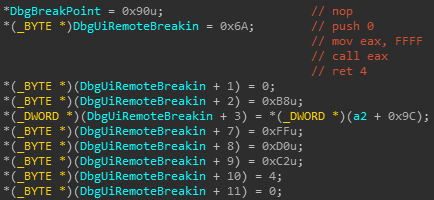
Figure 3: Ntdll function hook.
- The shellcode wraps several API calls that researchers put breakpoints on with a function that detects if soft breakpoints or hardware breakpoints have been set. It does that by checking if the DR* registers are set to a value other than 0, and checks whether bytes of the called API is 0xCC, 0x3CD or 0xB0F. If it detects hardware breakpoints or soft breakpoints it will jump to an invalid address to crash the program.
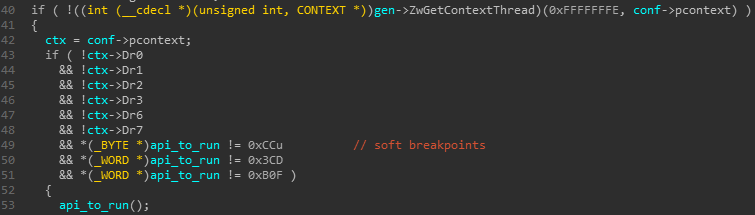
Figure 4: Check hardware breakpoints and soft breakpoints
before running an API call.
- Calls the NtSetInformationThread with the ThreadHideFromDebugger (0x11) information class.
- Anti static and dynamic analysis -- Mixed x86\x64 code. The same shellcode can be read as x64 bit and x86 bit code. Though the shellcode only works as x86 bit, this is used to hamper static and dynamic analysis by pushing junk instruction that doesn’t affect the original flow of the shellcode.
Figure 5: Same shellcode read as x64 bit and x86 bit.
GuLoader Functionality
Guloader uses the djb2 hash function in order to resolve API calls by hash. It does that to resolve GetProcAddress. Then, it will be using the same djb2 hash function to retrieve other API calls.
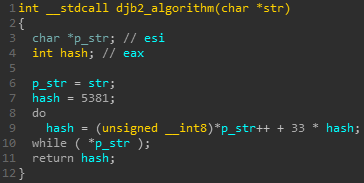
Figure 6: djb2 hash algorithm.
GuLoader uses a variation of a process hollowing injection in order to run its next stage. It spawns a new suspended process of itself (CreateProcessInternalW), and will then map “msvbvm60.dll” over the child process at 0x400000. Other variations of Guloader malware creates “RegAsm.exe” as a child process and map “mstsc.exe.” Next, it will inject the shellcode into the child process, changing the entry point to the shellcode’s entry point. The process is then resumed and the child process downloads the encrypted payload and overwrites the image at 0x400000 with the decrypted one. The decrypted payload, in our example, is Remcos RAT.
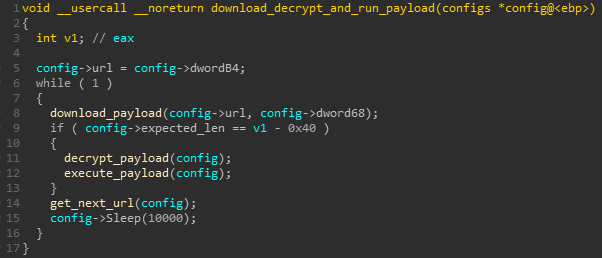
Figure 7: Function that downloads, decrypts, and runs the payload.
The loader then iterates through the URLs; there are two URLs in this sample but, at the time, one of them wasn’t active. Then, it will download the final payload in its encrypted form and will decrypt it using the XOR key (0x239 length in this sample), which is stored within the shellcode.
Next, the loader will overwrite the content loaded at 0x400000 with the decrypted code and jump to the entry point.
Conclusion
GuLoader is appearing more frequently as a malware loader in the wild. It’s one of the most advanced downloaders currently in use, and often downloads its payload from cloud hosting platforms. This campaign was a regular URL, however.
Morphisec blocks GuLoader execution, protecting its customers from this and other evasive malware to ensure that their critical infrastructure is secure. This protection extends to remote employees as well, and we encourage everyone to take advantage of our free trial to see how we protect critical systems against cyberattack.
IOCs:
Samples:
- 907b9784966bdbfc5447943747d3aed7445727d0
- 2d6720ae866875b42601951eb3c9421fa2d5b7f0
- fa601abbdeb159eccbcee527ebc6019619a9e442
- 12dd8f1cf43b51ec779363de98636c6e35fc1b4b
- 117d9701b22abb5530de2063698bcf75f2a90577
URLs:
- hxxp://arabianbrother[.]com/a/6.bin
- hxxp://arabianbrother[.]com/a/3.bin
- hxxp://ntaryan[.]com/a/6.bin
- hxxp://ntaryan[.]com/a/3.bin
- hxxps://drive.google[.]com/uc?export=download&id=12dw-X7CxidMNeST2IlWkZAaJAha5TUFG
- hxxps://drive.google[.]com/uc?export=download&id=1xz02BCj0obD4UPgs0CMtu_6GXxCEYXz
- hxxps://drive.google[.]com/uc?export=download&id=1xm_RKeKAUaH1QnWB_RZw4nMtdq7jK_PX





.png?width=571&height=160&name=iso27001-(2).png)