
They’re starting to be as reliable as clockwork. Every 3-4 weeks a new wave of Hancitor campaigns hit, with improved targeting and new tricks to evade detection. The latest variant comes via a malicious MS Word attachment to a fairly convincing email. How do we know? Our own CEO, Ronen Yehoshua, was one of the latest targets. Maybe the folks behind Hancitor liked our technical analysis (or get the original Hancitor report in PDF format) of the last attack so much that they wanted to deliver a new version for analysis personally.
As with previous variants, even with updated evasive techniques, Hancitor still can’t get past Morphisec’s Moving Target Defense technology.
This post will not be a deep technical dive into the new variant. Instead we wanted to share details of the email and malicious attachment so others know what to look for.
The email purports to be from inside the attacked organization’s accounting department and uses a legitimate sounding address (accounting@morphisec[.]com). It is constructed as if it is a reply to a previous email, giving the illusion that it is an ongoing thread and therefore less suspicious.
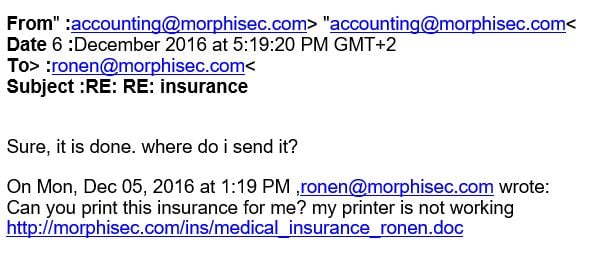
The victim’s email domain name (e.g. morphisec.com) is used another time in the email body. Note that the link in the text appears as if it goes to a file hosted on the organization’s domain. However, this hides the real link (hxxp//ruouduadaiviet[.]vn/api/get.php?id=cm9uZW5AbW9ycGhpc2VjLmNvbQ==), which is supposedly registered to Viet Solutions Services Trading Company Limited.
The document itself downloads with the legitimate sounding name insurance_ronen.doc. Upon opening, the document displays a fake message saying that it cannot be previewed because it is a protected document and gives instructions to enable macros in order to access it.
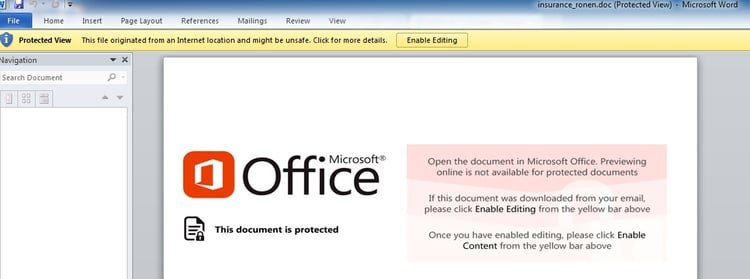
Upon enabling macros, Hancitor injects and executes shellcode, which opens up a backdoor to download and install additional Trojans, bots and other kinds of malware.
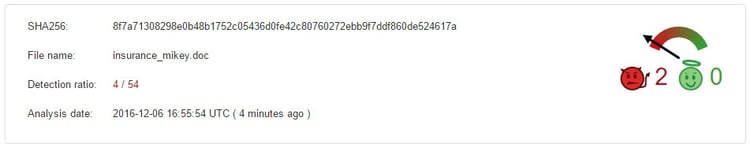
As seen with previous variants, the detection ratio for Hancitor attacks on VirusTotal (at the time of discovery by Morphisec) is very low. Via VirusTotal, we were also able to conclude that similar macro-enabled WORD documents, but with modified names, are being used in this campaign. The file naming is based on the targeted victim’s email address, following the pattern "insurance_<name>.doc."
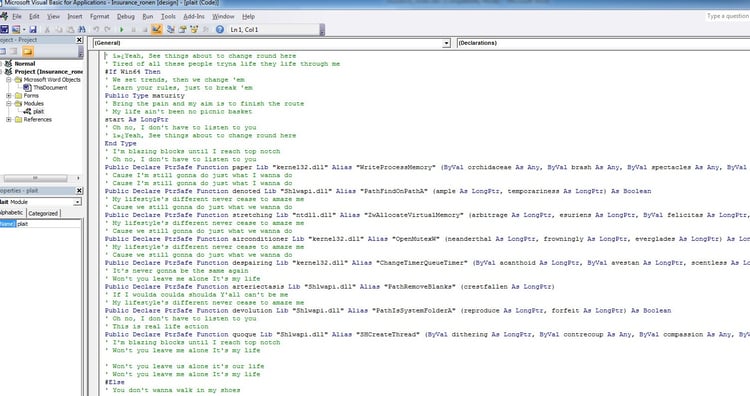
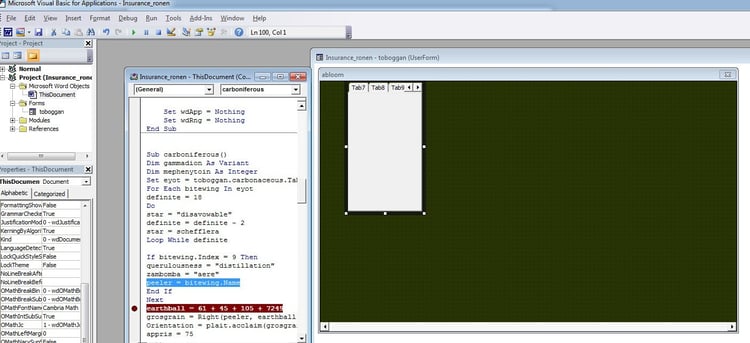
For the technically savvy reader, here are some images of the attack flow:





.png?width=571&height=160&name=iso27001-(2).png)