In the last few years, organizations in every sector have witnessed a clear shift in the threat landscape. Although the number and frequency of all kinds of cyberattacks increased, ransomware in particular has undergone extremely rapid evolution. Less than five years ago, ransomware was a relatively remote concern for most organizations. Today, a ransomware attack happens several times a minute. Few executives today take the threat this malware poses to their organization lightly. But evidently, not many know how to prevent ransomware.
The factors fueling the recent rise in ransomware are essentially economic, including easier monetization of network access via cryptocurrencies. However, the growth of ransomware as a criminal business activity has also catalyzed a profound technological shift.
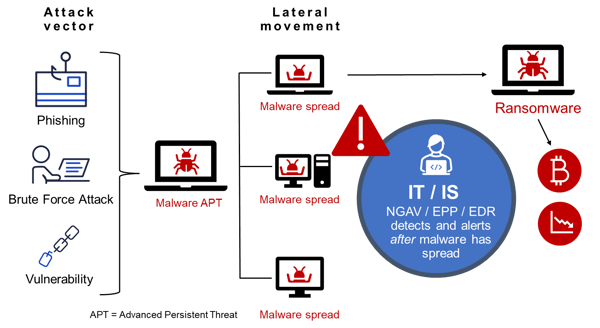
A typical ransomware attack
One notable aspect of this transformation is how today's third-generation ransomware has become a multi-level threat where extortion is coupled with access denial. Another is the continued ability of skilled malware developers to refine ransomware delivery and deployment methods. As a result, ransomware is becoming more dangerous, frequently sidestepping security controls altogether.
Perhaps the most worrisome recent development has been the shift from file-based deployment of ransomware. Now a payload delivery attack chain often starts and ends inside device memory at runtime—an extremely vulnerable attack vector for most organizations.
To respond to this profound change in attack deployment requires reassessing whether an organization’s defenses are working.
How to Prevent Ransomware: Block In-Memory Attacks
When defending against ransomware, security professionals typically rely on threat intelligence feeds to correlate and analyze information, assess security defenses, and prioritize actions to reduce risk.
Unfortunately, there’s a critical gap between the environments threat intelligence feeds monitor, and the places where attacks happen. The static indicators of compromise (IOC) these feeds provide often result in security teams being a step behind their attackers. This is because scanning solutions typically focus on static files and network behavior. Which means the vast majority of organizations are leaving a critical threat vector undefended—device memory at runtime.
Most cybersecurity solutions struggle to cover this vulnerability for good reason: scanning memory and processes during runtime slows everything down. Continuously scanning device memory is rarely compatible with real-world device and server use. To mitigate this challenge, most security solutions scan devices only when operations start and end. They rely on threats leaving detectable signatures which they are trained to recognize. However, modern ransomware uses in-memory attack chains which ruthlessly exploit the weakness of this methodology, making ransomware prevention all the more difficult.
Exploring the In-Memory Attack Chain
In a typical in-memory attack, the first stage consists of a dropper being downloaded onto a victim's device. At this point, any threat intelligence feeds based on static IOCs are already redundant. For example, whether a dropper is installed via something like a malicious Excel macro or filelessly through remote code execution, highly obfuscated attacks won’t show up in a threat intelligence feed until the attack is known and classified.
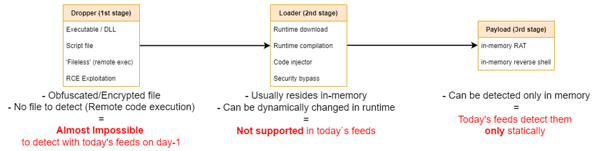
Ransomware attack chain
During the second stage of attack—loader deployment—a threat gains access to device runtime memory via a process like runtime downloading or code injection. By now, the attack is completely off the radar.
The final stage of this part of an attack, payload deployment—which could be something like a RAT or in-memory reverse shell, also happens in device runtime memory. This means the attack is again invisible and can only be detected statically after damage is done. From here, threats can move laterally across networks, switch off controls, and deploy ransomware. By the time a ransomware attack comes to a defender’s attention, it's already game over.
Moving Target Defense Protects Memory
Morphisec has witnessed and stopped thousands of attack chains like the one described above. We’ve noticed in-memory attack chains tend to involve malware like Cobalt Strike deployed as a predecessor to ransomware or in-memory ransomware strains like Conti. During attacks like these, a shellcode is typically allocated to dynamic spaces in device memory before using API calls to download malicious .dll files.
These kinds of threats are highly evasive and exist primarily in device memory, so no level of NGAV or best-of-breed EDR can reliably detect and stop them. The cybersecurity community must respond to these kinds of attacks by upgrading threat intelligence feeds to focus on memory detection.
Morphisec's Moving Target Defense (MTD) technology is an industry-leading solution to advanced attacks. It provides a low-impact, highly effective defensive response for every organization facing in-memory attacks.
Morphisec Stops In-Memory Attacks
By morphing device memory during runtime, Morphisec’s MTD augments an organization's existing security stack to stop and attribute fileless attacks that are otherwise impossible to detect.
Uniquely in the security industry, Morphisec leverages polymorphism to hide application and operating system targets from adversaries in an unpredictable manner. This leads to a dramatically reduced attack surface that makes targets impossible to find. It presents decoys to fool and trap threats without impacting usability. MTD blocks and exposes attackers relying on the invisibility of dynamic execution in-memory. Morphisec customers typically augment their existing solutions, including AV and EDR, to create Defense-in-Depth.
The answer to how to prevent ransomware is by using MTD, which delivers proactive, lightweight protection against zero-day and in-memory attacks. To learn more, read the white paper—The Ultimate Ransomware Strategy: Zero Trust + Moving Target Defense.






.png?width=571&height=160&name=iso27001-(2).png)