
Morphisec Prevents Major Malspam campaign - Again
In our report at the beginning of September about a large-scale malspam campaign discovered and stopped by Morphisec, we pointed out the central role that malware spam plays for hackers and the difficulties signature-based and behavioral security products can have in coping with them in real-time.
During October 10-12, 2016, Morphisec stopped yet another malspam campaign that again showed an extremely low detection rate on VirusTotal.
Below we analyze the campaign, focusing on this campaign’s use of MSScriptControl.ScriptControl. The use of script control is not new and has been used several times during the past two years. Although the technique is known, it remains a highly effective way to hide the script, as the script is activated directly from memory.
A good example of the effectiveness of this evasion technique is a very similar attack that is already 3-months old (579f569a70a874c496bb1e843c44d7cd6fcc71eb93a33bb2c8984a1299395e2c), which at the moment of this blog posting, still has a very low detection rate of 4/54 on VirusTotal.
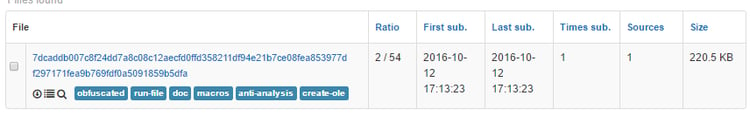
The sample under analysis was downloaded from https://www.reverse.it/sample/7dcaddb007c8f24dd7a8c08c12aecfd0ffd358211df94e21b7ce08fea853977d?environmentId=100 (2/54). (For those interested, we list additional samples that participated in the campaign at the end of this post):
Technical Analysis:
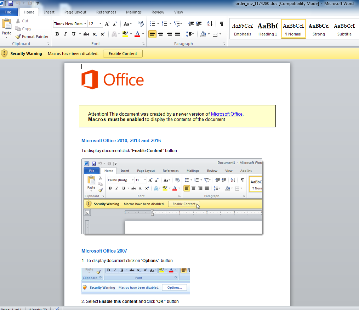
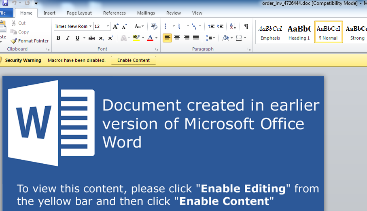
- The campaign detected by Morphisec involves a standard email with an attached Word doc of the type “order_inv_<random_number>.doc”: Recipients, as always, need to be convinced to open the macro so the VB script code will be activated:
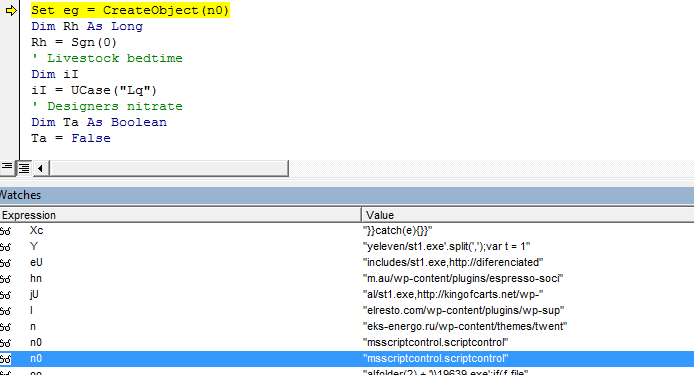
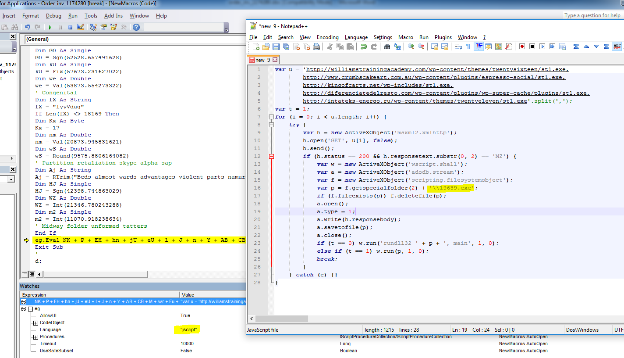
- Below we see how the MSScriptControl.ScriptControl is initiated. As a matter of fact, the outer script is not particularly obfuscated.
- The inner JavaScript, however, is much more interesting. It is activated by the script control and runs through a list of domains while trying to download an executable that is activated immediately. Note also the option (currently not active) to activate a dll using rundll32 (similar to the Zepto variant).
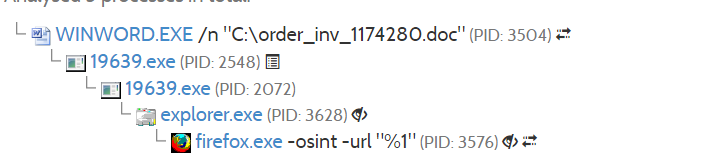
- Eventually the tree of processes that is activated by the executable – with the goal of gaining persistency by injecting into explorer.exe - is as follows:
- The info stealer executable also has a very low detection ratio at the time of writing this post: 6/54 VT (19639.exe, sha256 1c857f54f9ddf8b7cf14a886a9e758a21103095b19c2a3aaf5b176d7461a2d1c)
Additional Information:
Doc files:
6dfeac453b12b28d05cb8e97453cf909d26d71d6fe99e0b0951f23725deeac07
7dcaddb007c8f24dd7a8c08c12aecfd0ffd358211df94e21b7ce08fea853977d
aae79d53c8946aa8e9daede8c24896aad98a3348c89dd7e95953c749bbba2e5b
efe1d1d43c3b2a8e2ca606f3f64529c7e27c8536f1ea079573f119ba8c4c664e
e5319e5e9ac676f30d6aa690af90600f611a4c4272dc91bdb0a92c5e65a913ce
8374d4f20d23891aa22d26fd5548036f601dc58ba75dd5d7f7c26213f3ed32c0
Artifacts:
44070f56171b997ed4c76a5955d410b5388cf8b04f5983ef8f0e4c2ffd8d40db
1c857f54f9ddf8b7cf14a886a9e758a21103095b19c2a3aaf5b176d7461a2d1c
Domains:
hxxp://williamstrainingacademy[.]com/wp-content/themes/twentysixteen/st1[.]exe
hxxp://www.crumbscakeart[.]com.au/wp-content/plugins/espresso-social/st1[.]exe
hxxp://kingofcarts[.]net/wp-includes/st1[.]exe
hxxp://diferenciatedelresto[.]com/wp-content/plugins/wp-super-cache/plugins/st1[.]exe
hxxp://intateks-energo[.]ru/wp-content/themes/twentyeleven/st1[.]exe
hxxp://yurlog[.]ru/wp-content/themes/twentytwelve/st1[.]exe
hxxp://itsmemary[.]com/wp-content/themes/itsmemary2014/st1[.]exe
hxxp://www[.]wereorganized[.]net/blog/wp-content/themes/twentythirteen/st1[.]exe
hxxp://www[.]holisticwellnessbiz[.]com/wp-includes/st1[.]exe
hxxp://ericrobertanderson[.]com/wp-includes/st1[.]exe
hxxp://cyperritheck[.]ru





.png?width=571&height=160&name=iso27001-(2).png)