
The Lazarus Group, also known as Hidden Cobra, may be in play again. The notorious cybercrime group is allegedly responsible for some of the most devastating attacks over the past few years, including the SWIFT network hack that stole $81 million Central Bank of Bangladesh issued and the 2014 destructive wiper attack against Sony Pictures. Some also link the WannaCry ransomware breakout to the same group.
Many of the existing reports covering the Lazarus attacks suggest links to North Korea. In fact, Hidden Cobra is the U.S. Government’s designation for malicious cyber activity conducted by the North Korean government.
On February 28, 2018, Morphisec Labs identified and prevented a suspicious document uploaded to VirusTotal that exploits the latest Flash vulnerability CVE-2018-4878. While analyzing the exploit and the downloaded payload, we immediately identified a near-perfect match to many of the techniques used during various attacks that are attributed to the Lazarus Group.
The encryption of the different strings, the network protocol, and additional indications such as the language of the resource directory were almost a one-hundred percent match for the patterns that were used during the Sony attack.
However, there was almost a complete lack of obfuscation in both the exploit and the malware payload. This seems to suggest that someone may have planted the patterns, deliberately wanting researchers to identify it as a Lazarus campaign.
My tweet about the findings of the Morphisec Labs set off a storm of debate. Is it Lazarus? Is it an imposter? The exploitation and the payload exhibited a fairly high level of sophistication, yet in some places there was no validation for input and a lack of proper evasion.
Lazarus group hits again CVE-2018-4878 (2 hours ago) including 64 bit MD5: 41b541412154d9e7ce46f952e02dec70 @morphisec labs pic.twitter.com/UMUXGpt7ZH
— Michael.Gorelik (@smgoreli) February 28, 2018
Regardless of the answer, the attack is interesting and another indication that this latest Flash vulnerability is likely to become the new favorite exploit of cybercriminals and state actors alike.
Technical Flow
Mail is sent to a target with the following Word document “AGREEMENT.docx”:

The document exploits CVE-2018-4878 (Flash exploit) to execute code on the system. This exploit has both 64 and 32 bit implementations of the exploit and shellcode as opposed to the campaign reported a week ago that used only the 32 bit variant. The exploit uses an encryption method to hide some known strings which is similar to previously used Lazarus encryption algorithms.
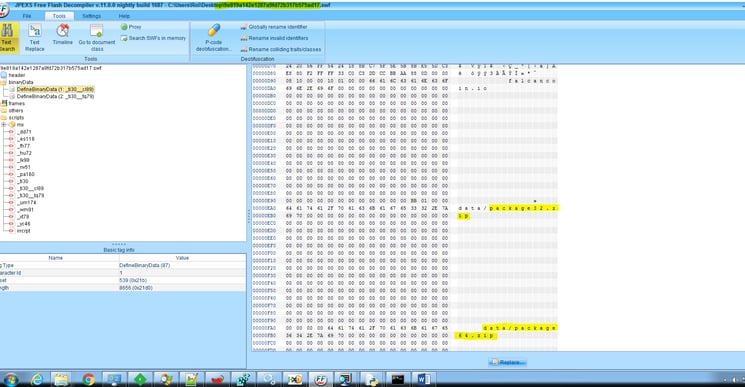
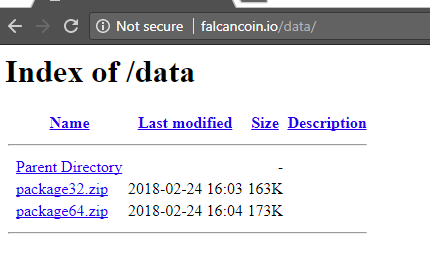
The code downloads and executes a dll from a (probably) compromised domain:
We notified about the abuse of the domain but it is still active.
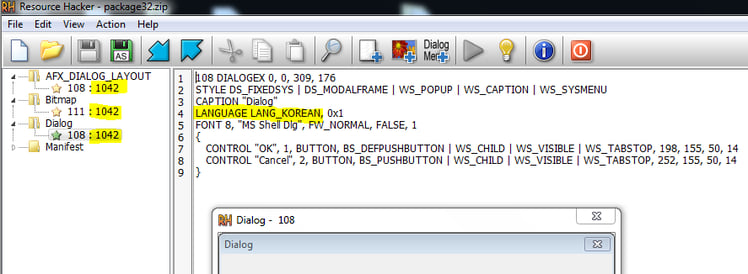
And the resource directory for the dlls references the Korean language:




.png?width=571&height=160&name=iso27001-(2).png)