Morphisec has successfully identified and prevented a new variant of IDAT loader. This loader is used to deliver a range of malware payloads based on the attacker's assessment of the victim's system. Distinguished by its modular architecture, IDAT employs unique features like code injection and execution modules, setting it apart from conventional loaders.
Morphisec customers are protected against this threat.
 Attack Name: New variant of IDAT Loader
Attack Name: New variant of IDAT Loader
Severity: Critical
Technical Analysis
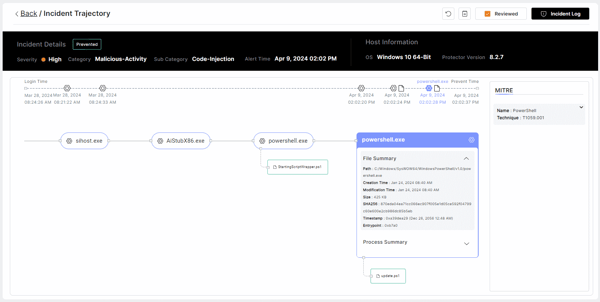
Morphisec’s analysis indicates the attack begins by downloading a setup file UpdateSetup.UpdateSetup_1.3.36.292_x86 from the Windows app store.
The application is delivered as an MSIX file - MSIX is a Windows app package format that provides a modern packaging experience to all Windows apps, delivered as a .ZIP-based container file.
The MSI was edited to include a custom action that is executed through a PowerShell signed script - StartingScriptWrapper.ps1 (a part of the PsfLauncher which is delivered by Advanced Installer). The malicious action script is named update.ps1 which delivers the IDAT Loader.
The signing of the PSFLauncher Script (StartingScriptWrapper.ps1) complicates detection and bypasses security controls such as EDRs and even application whitelisting solutions.
This signing of the file reduces the chances of detection by NGAV/EDR solutions unless there is a specific indication this file is malicious.
The update.ps1 script redirects to the first C2 https[:]//utm-msh[.]com/profile/ which loads the IDAT loader.
Execution Command
powershell.exe '-ExecutionPolicy' 'RemoteSigned' '-file' 'C:/ProgramFiles/WindowsApps UpdateSetup.UpdateSetup_1.3.36.292_x86__s3garmmmnyfa0/update.ps1
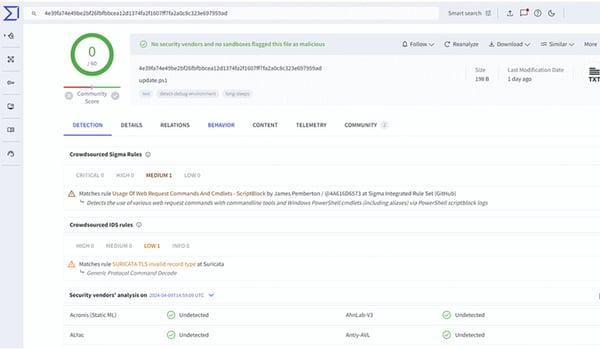
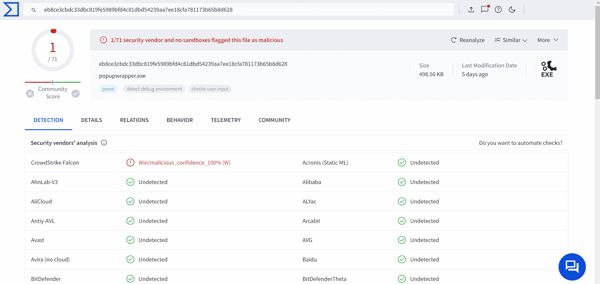
Analysis of the files on VirusTotal at the time of the attack showed zero detections for the malicious script and minimal detections for the C2 URL. At the time of writing this report, detections have gradually increased, meaning the threat is still unknown to most endpoint protection and web filtering solutions.
Morphisec Threat Prevention Trajectory
 VirusTotal query of update.ps1 at the time of the attack:
VirusTotal query of update.ps1 at the time of the attack:
VirusTotal query of UpdateSetup.UpdateSetup_1.3.36.292_x86:
VirusTotal query of https[:]//utm-msh[.]com/profile at the time of the attack:
![VirusTotal query of https[:]//utm-msh[.]com/profile at the time of the attack](https://blog.morphisec.com/hs-fs/hubfs/5of92.png?width=600&height=247&name=5of92.png)
The attack prevention by Morphisec showcases the capability of AMTD-powered solutions to prevent sophisticated and advanced attacks in the wild and augmenting the cyber-security stack and reducing attack surface exposure. In this case the attack was prevented when existing cyber-defense solutions had low detection ratio of the attack.
Morphisec Protection Mechanisms
- Anti-Tampering Prevention Mechanism
How Morphisec Prevents the Attack
Morphisec’s AMTD dynamically alters the application memory structure and disables the framework needed for an attack to succeed. The Morphisec Endpoint Anti-Tampering mechanism powered by AMTD prevented this attack at an early stage before it could impact the environment. This validates the pro-active protection power of AMTD against attacks and its hardening of the security stack by reducing attack surface exposure. Morphisec’s AMTD uses an ultra-lightweight agent with a negligible performance impact that does not require prior knowledge - signatures, behavioral patterns, or indicators of attacks (IoAs).
Mitigation Recommendations
- Ensure all critical assets are protected by Morphisec
Indicators of Compromise (IOCs)
|
IOC |
Details |
|
update.ps1 |
4e39fa74e49be2bf26fbfbbcea12d1374fa2f1607ff7fa2a0c8c323e697959ad |
|
UpdateSetup.UpdateSetup_1.3.36.292_x86 (popupwrapper.exe) |
eb8ce3cbdc33dbc819fe5989bfd4c81dbd54239aa7ee18cfa781173b65b8d628 |
|
C2 |
https[:]//utm-msh[.]com/profile/ |
Schedule a demo to learn more about how Morphisec prevents IDAT loader, ransomware and other advanced threats. Reduce Risk Now.





.png?width=571&height=160&name=iso27001-(2).png)