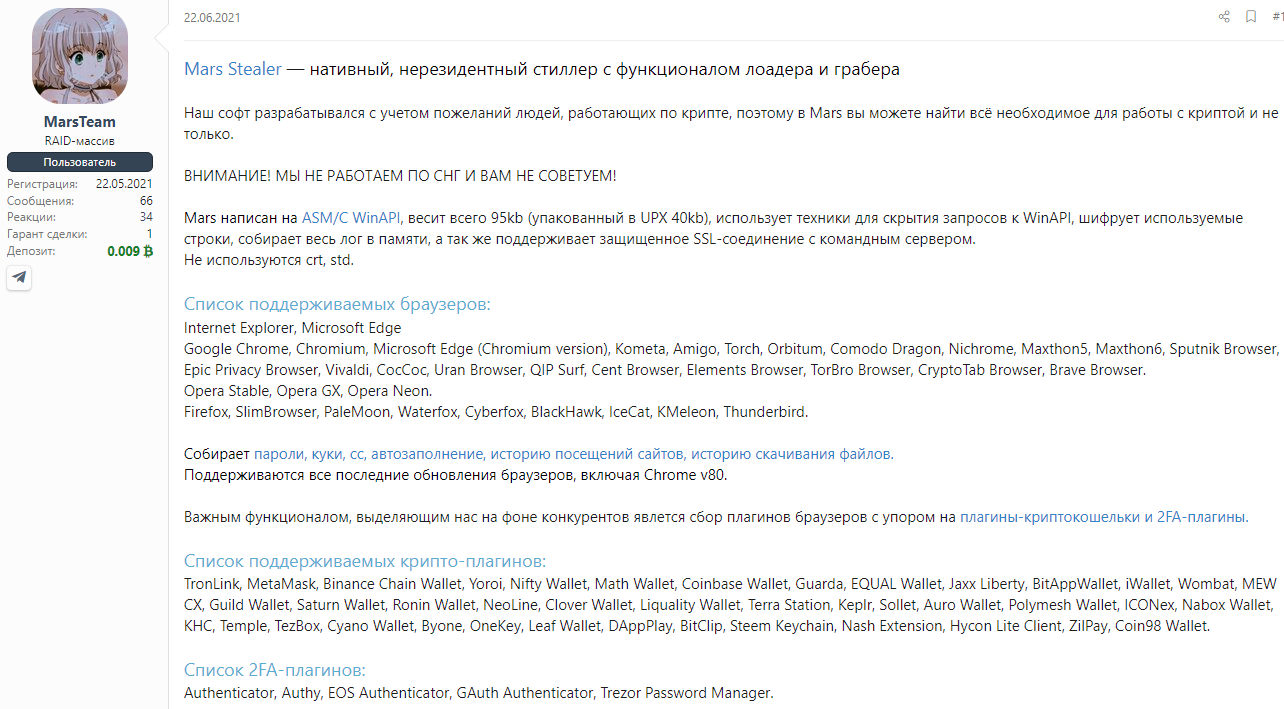
The Morphisec Labs team has conducted research on the new Mars infostealer. Mars is based on the older Oski Stealer and was first discovered in June 2021. The new Mars is available for sale on several underground forums and is reported to be under constant development. The Mars Stealer pilfers user credentials stored in various browsers, as well as many different cryptocurrency wallets. Mars Stealer is being distributed via social engineering techniques, malspam campaigns, malicious software cracks, and keygens. (For more about infostealers, read Morphisec’s coverage of the Jupyter infostealer.)
Figure 1: Mars stealer post on hacking forums.
Not long after the Mars Stealer’s release, a cracked version was released with an instruction document. This guide has some flaws. One flaw instructs users to set up full access (777) to the whole project, including the victims’ logs directory.
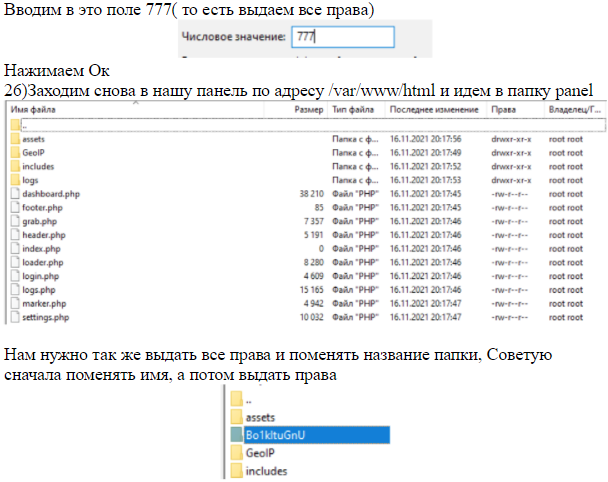
Figure 2: Cracked Mars Stealer instruction guide.
Whoever released the cracked Mars Stealer without official support has led threat actors to improperly configure their environment, exposing critical assets to the world.
Infostealers Ecosystem
As Sophos explains, information stealers are used for a wide variety of identity theft. They enable attackers to harvest personally identifiable information (PII), including login data such as stored credentials and browser cookies that control access to web-based services. These credentials are then sold on criminal marketplaces.
Infostealers offer an accessible entry point to criminal activity. For example, only $160 gets you a lifetime subscription to Mars Stealer. You can purchase infostealers on Dark Web forums without any vetting, unlike more sophisticated tools such as ransomware, which require you to have a reputation amongst other cybercriminals. Infostealers empower novice cybercriminals to build a reputation they can leverage to acquire more powerful malware from more sophisticated actors.
Mars Stealer Statistics
With cryptocurrency use rising, more people will likely possess hot wallets in an unsecured environment. The crypto wallet MetaMask is the plugin most stolen using Mars Stealer.
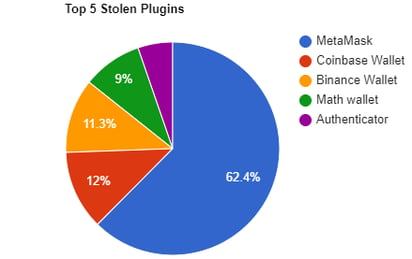 Figure 3: Top 5 stolen plugins
Figure 3: Top 5 stolen plugins
The Morphisec Labs Team compiled the below statistics while evaluating a single actor’s campaign last month. It includes targets by country, total stolen passwords, and so on. In addition, we found more than infected 50 domain users, compromising companies' domain passwords. The vast majority of victims are students, faculty members, and content makers looking for legitimate applications who end up with malicious ones instead. Aside from the listed credential types, Morphisec identified credentials which led to the full compromise of a leading healthcare infrastructure provider in Canada, and a number of high profile Canadian service companies. We have contacted and notified the companies and the authorities.
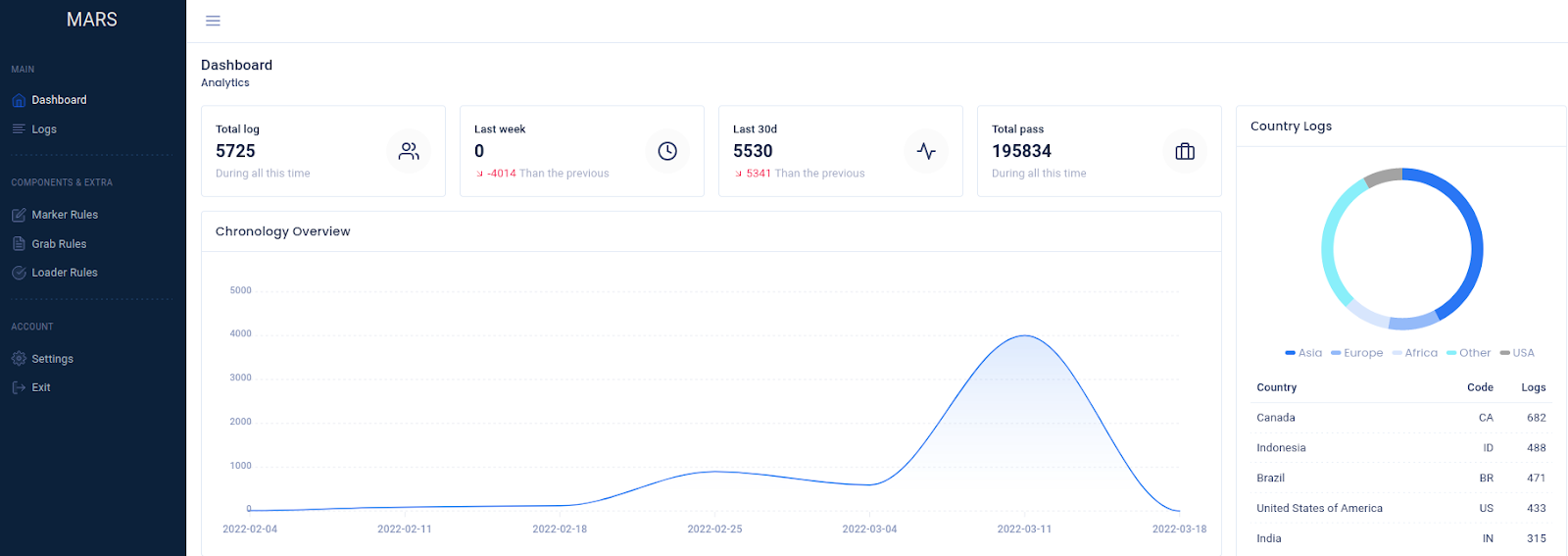
Figure 4: Mars admin panel
Operation Mars
Spam email is the most common distribution method for Mars Stealer, as a compressed executable, download link, or document payload. Creating a malicious website masquerading as pirated software is another common method for spreading this infostealer.
Initial access vector
In this campaign, the actor distributed Mars Stealer via cloned websites offering well-known software. They used the Google Ads advertising platform to trick victims searching for the original software into visiting a malicious site instead. The actor is paying for these Google Ads campaigns using stolen information (see figure 15). The example below is one of many demonstrating how the actor targets Canadians by using geographically targeted Google Ads.
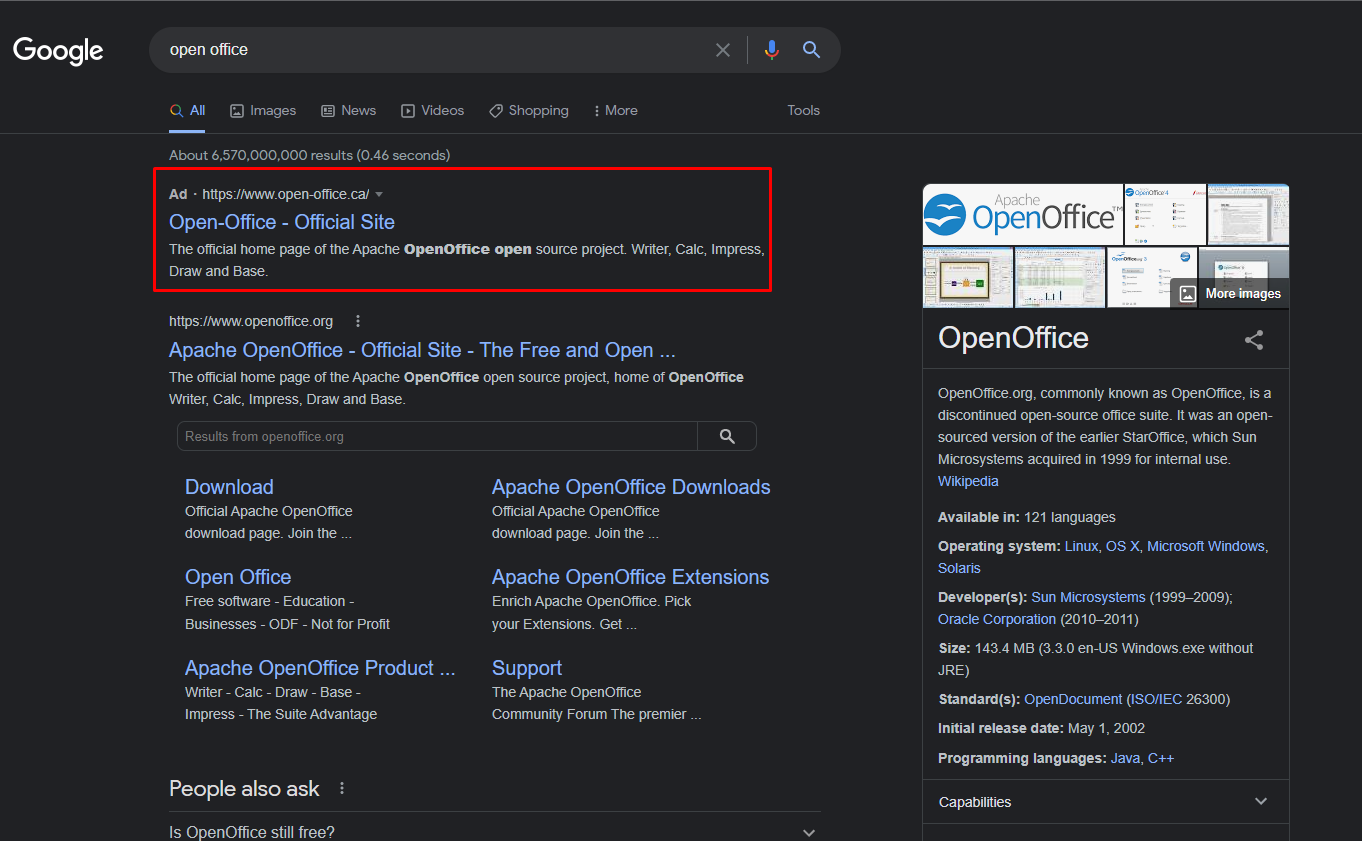 Figure 5: ‘OpenOffice’ Google search yields an actor's malicious website.
Figure 5: ‘OpenOffice’ Google search yields an actor's malicious website.
Below is a fully cloned website masquerading as the official openoffice.org website to lure victims to download the Mars Stealer.
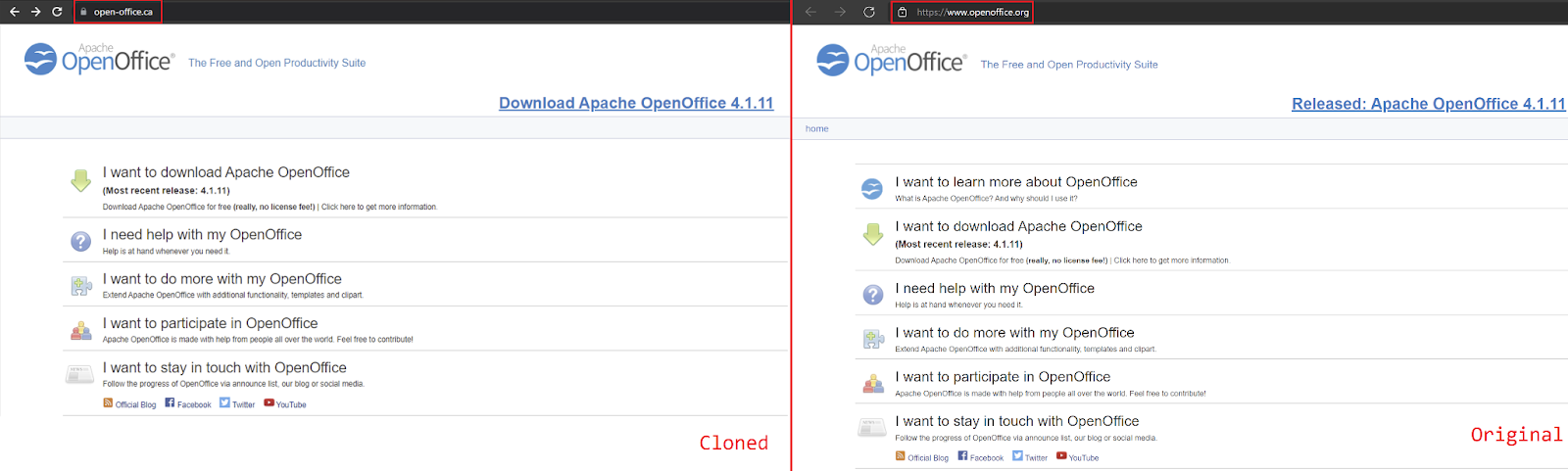
Figure 6: Cloned OpenOffice website leads to the Mars stealer.
The downloaded payload is an executable file, with a corresponding icon and name, packed with the Babadeda crypter or Autoit loader. We won’t cover the Mars Stealer’s technical details, which were thoroughly covered by 3xp0rt. During our investigation and research, we identified a C2—tommytshop[.]com—where the Mars admin panel is stored, which was still up and running at the time of publication.
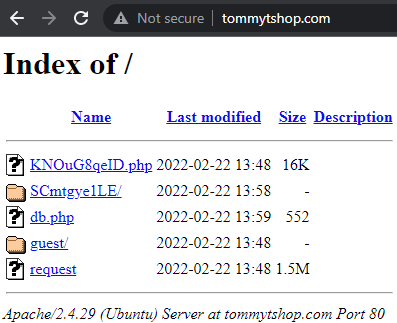
Figure 7: C2 open directory
As mentioned earlier, surprisingly, the stolen information directory was improperly configured and left open. We immediately identified that the vast majority of compromised victims are from Canada (files that start with CA_).
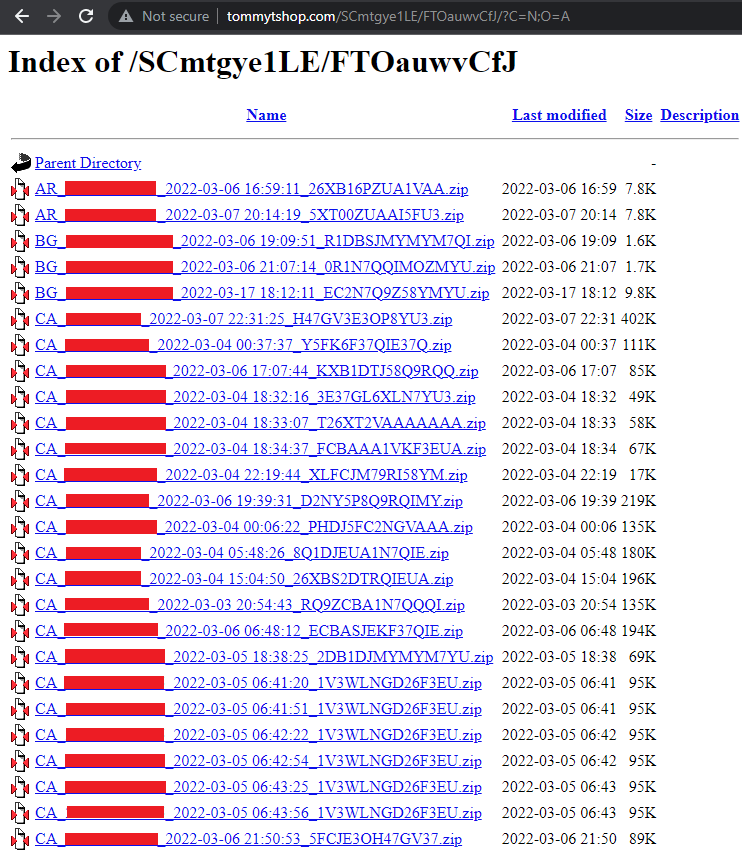
Figure 8: Stolen Information
Below is an example of stolen information extracted from one of the folders. It’s quite self-explanatory:
- Autofill - Stores browser autofill data
- CC - Stores credit card information
- Plugins - Stores browser extension data: Metamask, Coinbase wallet, Binance, etc.
- System.txt - Stores infected system information such as IP, country code, timezone, etc.
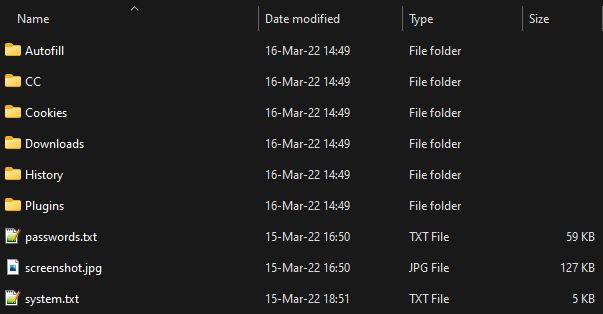
Figure 9: Stolen information content
Mapping the Attack Infrastructure
Fortunately, the actor compromised his own computer with the Mars Stealer while debugging. This allowed us a rare peek into an operation by looking at his own stolen information—screenshots, passwords, history, system information, etc. Below is an image we generated to summarize the actor’s most relevant activity details.
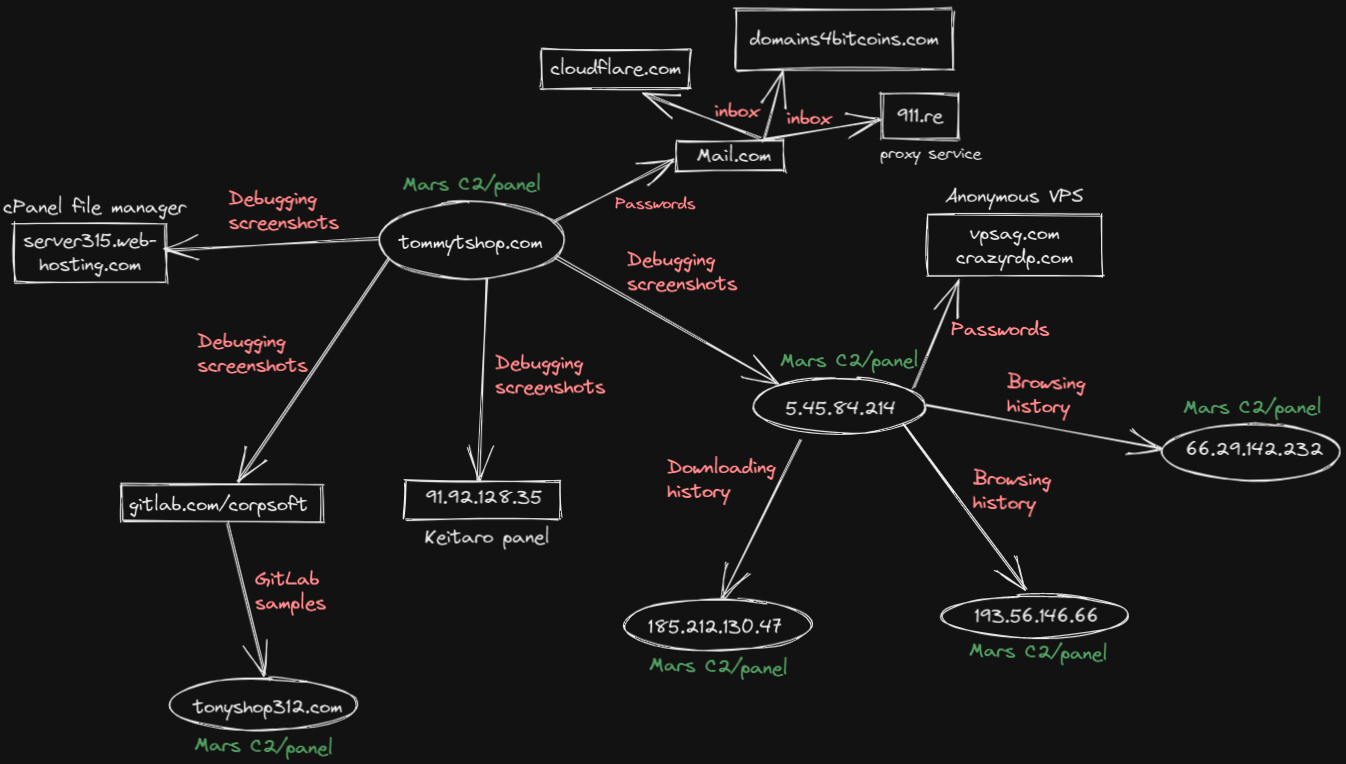 Figure 10: Recon diagram
Figure 10: Recon diagram
We looked at the actor’s screenshots and discovered they were debugging their Mars Stealer builds using HTTP Analyzer. This revealed their second Mars Stealer C2 - http://5.45.84[.]214 which was improperly configured, similar to the first C2.
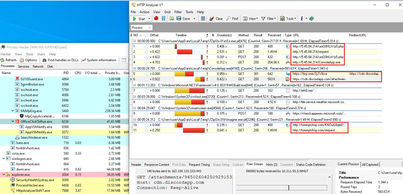
Figure 11: Actor’s screenshot revealing additional C2
An additional screenshot led us to the actor’s GitLab account, which was continuously updated with the latest Mars Stealer builds under the name of “Tony Mont,” which has been active since late November 2021. We are assuming they do this for automation purposes.

Figure 12: Actor’s GitLab account
Another interesting screenshot revealed this actor stores their passwords in a plain text document for almost every service they’re using.
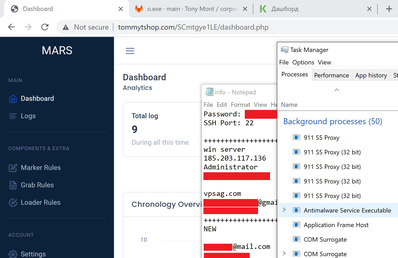
Figure 13: Actor’s plain text passwords
The actor is also using Keitaro, a universal tracker for affiliate marketing. And the images below show the actor is a Russian speaker.
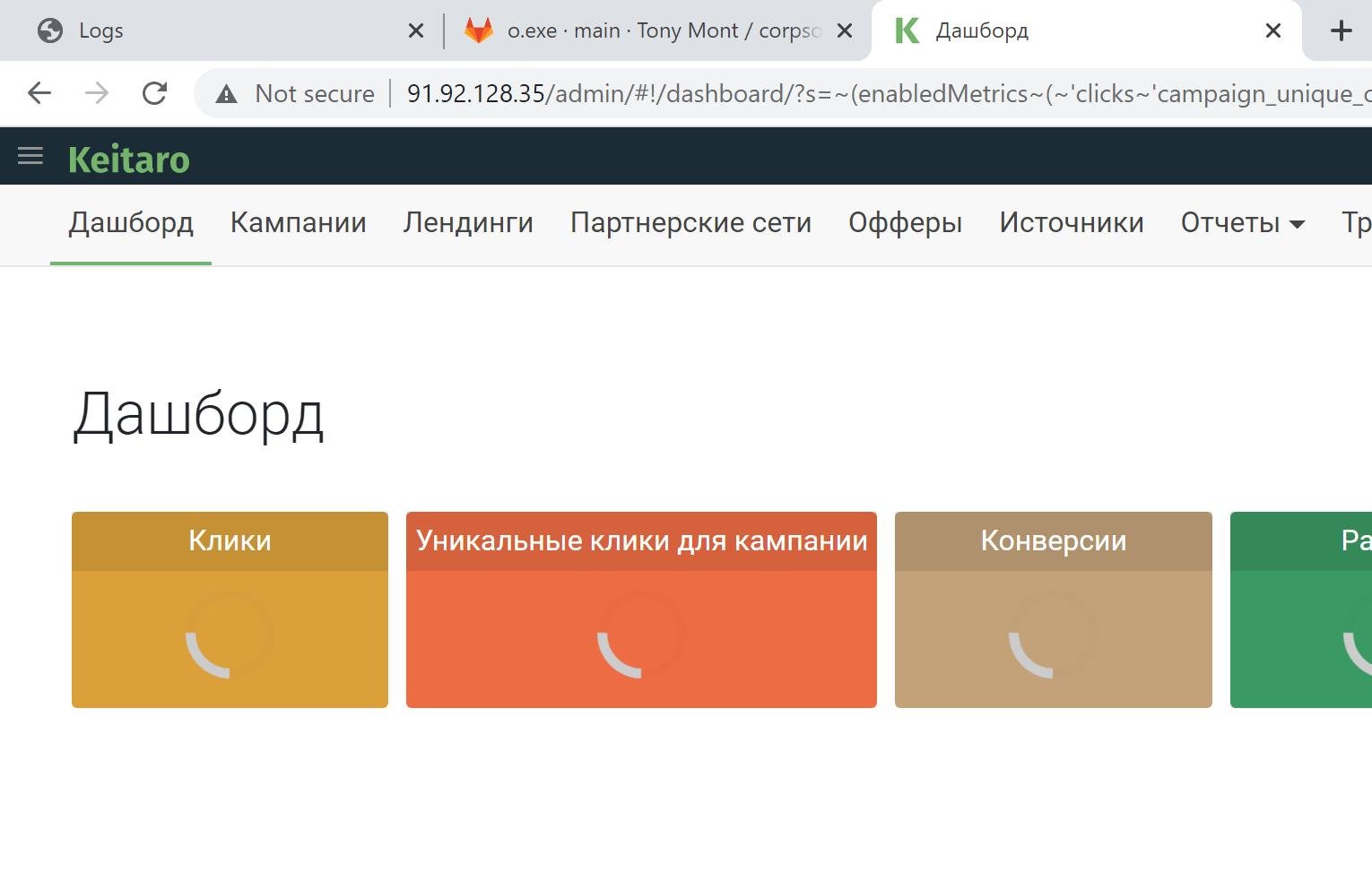
Figure 14: Keitaro panel
The actor’s Google Ads platform page, paid for with stolen credentials.
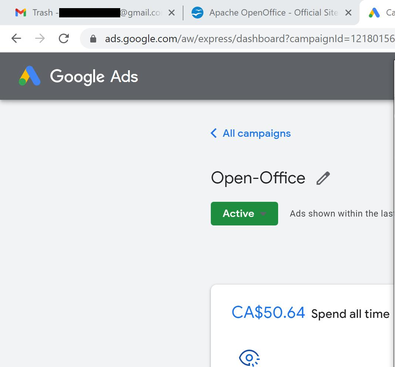
Figure 15: Actor’s Google Ads campaign
Attribution
We can safely attribute this actor as a Russian national by looking at the screenshots and keyboard details from the extracted system.txt.
Protect Yourself From Infostealers like Mars Stealer
Morphisec Labs will keep monitoring the Mars Stealer and provide updates when appropriate. Infostealers are used by a wide variety of cybercriminals, from novices to state-sponsored actors. They’re easy to acquire—and they work. Mars is currently being promoted in over 47 different underground forums, Darknet onion sites, and Telegram channels, and even has an official Telegram channel for purchasing through.
Morphisec protects against advanced attack chains such as those used in the Mars stealer. We do this with our patented Moving Target Defense (MTD) technology, which blocks advanced and zero-day attacks. MTD uses system polymorphism to hide application assets, operating system assets, and other critical assets from adversaries. This leads to unpredictable and dramatically reduced attack surfaces.
Gartner analysts call Moving Target Defense a “game-changer.” Learn more about Moving Target Defense and why Gartner cited this technology in its report: Emerging Trends and Technologies Impact Radar for Security.
Indicators of Compromise (IOCs)
Services
| IP/URL | Service |
| 91.92.128[.]35 | Keitaro panel |
| https://gitlab.com/corpsoft | GitLab account |
| server315.web-hosting.com:2083 | cPanel file manager |
Mars C2
|
tommytshop[.]com |
Samples (SHA256)
|
c48e5a61fd89ac5e950a37e1d81d2f733c16983d369dbedbb3a0c3e8c97f7b14 |



%20Attacks%20-%20Morphisec%20Labs.png?width=1200&name=Mars%20(Stealer)%20Attacks%20-%20Morphisec%20Labs.png)
.jpg?width=1920&name=Gartner%20Ad%201.91_1%20(1).jpg)

.png?width=571&height=160&name=iso27001-(2).png)