
A whopping 186.4 million Americans shopped in stores and online between Black Friday and Cyber Monday this year, according to the National Retail Federation. On average, these shoppers spent $361.90 per person over the five-day Thanksgiving weekend.
The sheer amount of money changing hands during this timeframe is a hugely attractive target for scammers and other cybercriminals. Consumers are often stressed during this period and make purchases that deviate from their normal routine. If a phishing email that seems legitimate enough arrives in such a consumer’s inbox, it’s more likely that the target will take action they shouldn’t.
In essence, the scammers behind these phishing emails are taking advantage of the holiday shopping chaos to the net as many victims as possible. Black Friday and Cyber Monday may have resulted in a nearly $1 trillion payday for legitimate businesses, but it’s highly likely that cybercriminals also took home some personal data and other information they could sell for a profit.
We noticed this strategy most recently with the Trickbot trojan banker. Between December 3 and December 5, a new Trickbot campaign targeted eCommerce shoppers with a phishing email that included a message about an order being shipped, as in the chain below:
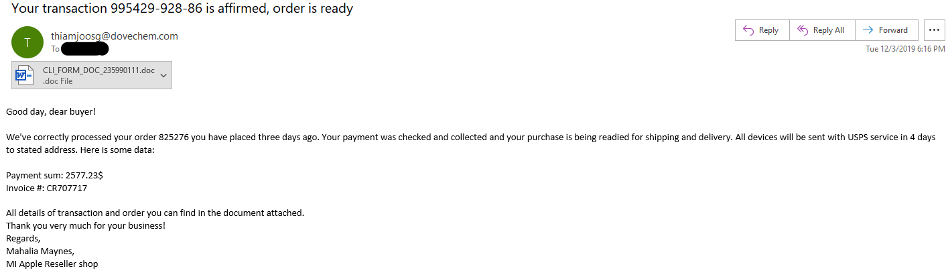
Figure 1 Phishing email pretends to be order details
Each of these phishing emails contains a Microsoft Word document as an attachment. The attacker tries to lure the victim to click ‘Enable Editing’ by a commonly used technique.
Trickbot TROJAN Macro Analysis
At first glance, it looks like the document that opens is empty, but the word count at the bottom of the screen suggests otherwise.
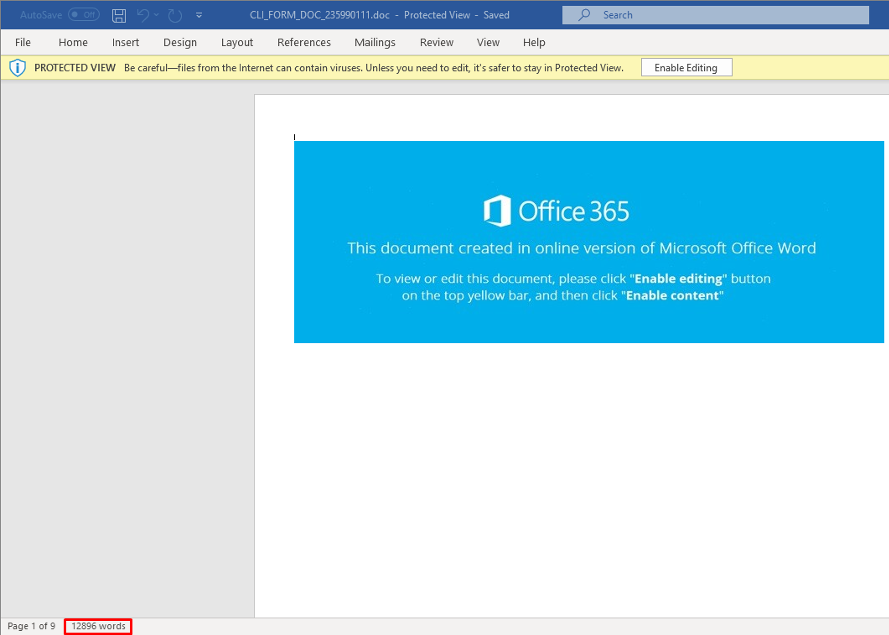
Figure 2 Attached word document allegedly empty
The high word count comes about because the attacker ‘hides’ a plaintext JavaScript code known as an Ostap downloader in the document body by setting the text color to white. This allows the test to be there, but not be human-readable.
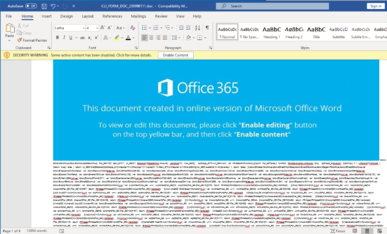
Figure 3 Plaintext JavaScript code
When the victim enables the included macros, a fake error message will pop up. Meanwhile, in the background, it will save the plaintext JavaScript to ‘Users.jse’ under %appdata%\Microsoft\Massfol. Then the JavaScript is executed via a ‘Wscript.Shell’ Object.
Trend Micro recently did a detailed analysis on the JavaScript dropper.
There are many high-volume campaigns distributing this infection chain since the beginning of December. For example, a few days ago (December 13 to 15), we found a similar campaign to the one from earlier this month delivering Trickbot. The infection chain is very similar between them all, with slight modifications, this time the phishing email is allegedly received from “HelloFax Services.”
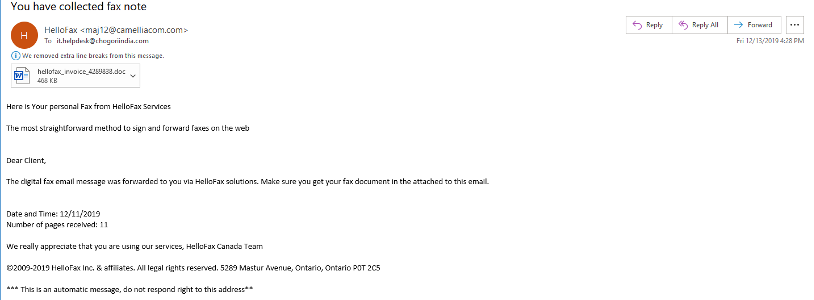
Figure 4 New Phishing email
It looks like the attacker used a modified version of the Ostap (Jscript) downloader because:
- It downloads the payload as base64, htm and exe.
- The user-agent header is deferent between different campaigns. (chrome version) probably to avoid network-based signatures
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77Safari/537.36
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.3538.66Safari/537.36
- Anti-Sandbox / Anti-VM – Extending the length of the list of running processes.
Final Thoughts
The holiday season involves a lot of money changing hands. The threat actors behind the latest Trickbot campaigns understand this fact, and they have taken advantage of the stress of the holidays to make money. With so many consumers making purchases, the phishing emails used in this campaign have a strong possibility of success.
Morphisec customers are protected from the Trickbot trojan banker through the power of our moving target defense platform. With a strong prevention methodology, Morphisec’s solution enables businesses large and small to be protected from any exploits.
IOC:
Docs:
- d07ad6fdcfeabead5a5dd3de07966194d6974c6b
- 8cc3e77f8bca5a995aa4a593b5a8d10173bf828a
- 73afe21f7594478d443f0b4498c8e4bf1324f7fa
- 781B751BF727D4E3C5BE443B38B9C8155ECAC4A3
- 12E3E85DA0B66306004F400EAB4C6BC4BB810608
- B0431F6B605AF8B4790E9E17AB884F4C9D60B08A
- 1A167A587F6E2707CD27EFABEFCBEFF1DE0A7EEE
- 5FFD6F249DE0B6866147627086A08A7ED0F46B8A
- D31F1948308E756904B9153005C768F5D0CA464D
- B019A864F91AF4741AC09FDA36A602435151D1C0
- 46C2E5EBCC2EAB80E5DABA637150F44D27883162
Email:
- c1bb3aef04cb24ed1cfc9a3a0c6f54bfdc3796ed
- cdc2c506102df075e39f31fafd1360512403cfd0
Trickbot:
- 83786b35997c07475b0a7f3afbd44fc09ce9793f
- 64161dd9da68bdcd6b6ffe414265d86a4185694f
- 1874998e8263447497d03afbbf0f7689c86835e0
- be4d16b76429b280a6cbb6d67db645509f70861c
Trickbot C2:
- 234.73.119
- 244.213.237
- 196.207.202
- 14.30.176
- 159.82.140




.png?width=571&height=160&name=iso27001-(2).png)