Gartner released two reports this month including Gartner® Emerging Tech: Security — AMTD Transforms Endpoint Protection1 and Gartner Emerging Tech: AMTD Advances Proactive Cloud Defense 2 report, which each feature Morphisec as a sample vendor.
This inclusion provides significant validation of our Automated Moving Target Defense (AMTD) technology and its success in stopping ransomware and other advanced attacks, while introducing operational efficiency to security teams.
The Rise of AMTD
Industry standard solutions like Endpoint Detection and Response (EDR) and Endpoint Protection Platforms (EPP) rely on threats leaving detectable Indicators of Attack (IoAs), for which they’re trained to recognize. However, sophisticated attack techniques that exploit vulnerabilities and use in-memory attack techniques are growing in popularity. Moreover, these techniques increasingly bypass the current security stack including NGAV, EPP and EDR/XDRs.
The Gartner Emerging Tech: Security — AMTD Transforms Endpoint Protection report states that: “AMTD makes it harder for attackers to identify and exploit vulnerabilities by dynamically modifying system configurations, software stack or network characteristics. This proactive approach helps to improve cyber defense and mitigate the risk of successful attacks.” 1
For attacks to succeed, they must compromise a resource on a target system. Current technologies attempt to detect threats, a practice which ultimately fails. AMTD introduces a paradigm shift. If the target resource doesn’t exist or is continually being morphed (moved), the chance of targeting a system is reduced by an order of magnitude.
As described by the Department of Homeland Security, "Moving Target Defense (MTD) is the concept of controlling change across multiple system dimensions in order to increase uncertainty and apparent complexity for attackers, reduce their window of opportunity and increase the costs of their probing and attack efforts”.
AMTD dynamically alters the attack surface, which for example, disrupts the activation of frameworks used by threat actors. This abuse of attack frameworks (e.g. Cobalt Strike, Sliver) is a critical component in the attack sequences since they are often capable of evading detection. This proactive approach of AMTD closes the protection gaps in reactive cybersecurity solutions, enabling enhanced protection, such as a comprehensive anti-ransomware prevention strategy.
In simple terms - instead of attempting to detect threats, AMTD moves the target.
Crucially, AMTD’s early prevention and exact threat classification also prioritizes high-risk alerts, thereby reducing security analyst alert triage time.
Per Gartner, “Product leaders must recognize that for every attack prevented using AMTD, the downstream implications on security operations and IR personnel time, data processing, analysis, latent response, false positive volume and forensics costs can be significantly reduced.” 1
AMTD Enhances Endpoint Protection
Threat actors continually evolve their techniques and tactics to bypass endpoint protection solutions. In fact, defense evasion techniques are well documented, compromising over 30% of TTPs used by threat actors.
As noted by Gartner, “Attackers continue to focus on identity-based attacks (often collected by using exploits), malicious executables and living off the land (LOTL) software used by administrators already on endpoints. Attackers rely on a mix of obfuscation and evasion techniques as common methods of defense evasion. Endpoint attacks typically use some style of remote exploitation that involves injecting a tainted payload into executable memory, passing commands to the command line, or retrieving malicious content from trusted third parties.” 1
In this reality, AMTD critically enhances security for endpoints, applying its paradigm shift to the organization’s largest and most vulnerable attack surface. It represents the next evolution in endpoint protection, with proven effectiveness in the modern cyber battlefield, where threat actors employ increasingly evasive techniques to evade detection by reactive protection technologies. The robustness of AMTD is proven against multiple past and future waves of endpoint security threats, most recently with the rise of generative-AI attacks.
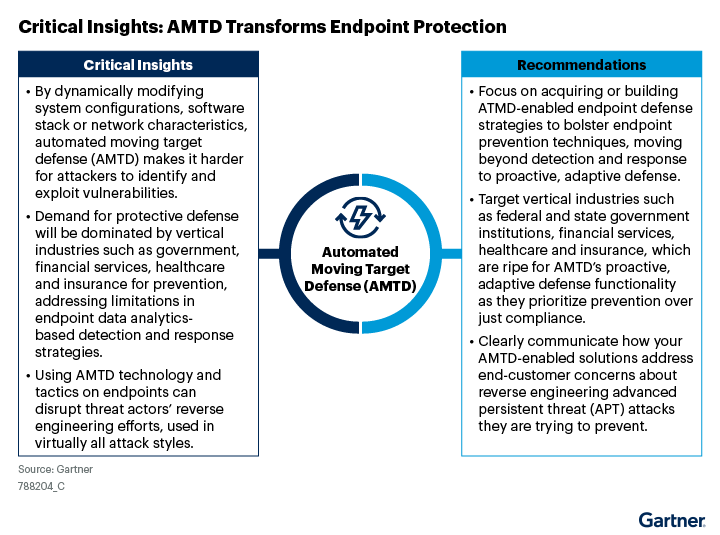
Gartner diagram, Critical Insights: AMTD Transforms Endpoint Protection 1
Gartner notes that: “Clearly, we need a new strategy of defense as organizations continue to fall prey to common exploitation methods. Government institutions, financial services, healthcare and insurance industries prioritize cybersecurity over compliance, and are logically prime candidates for adopting enhanced AMTD functionality. These vertical industries often prefer the strongest security measures and deal heavily with advanced threat actors.” 1
As regulators including the U.S. Securities and Exchange Commission (SEC) and Federal Trade Commission ramp non-compliance enforcement, enterprises must drive continuous compliance and defense strategy enhancements that ensure greater transparency.
According to the Gartner report1, benefits of AMTD include:
- “Enhanced protection against zero-day vulnerabilities and exploitation”
- “Reduced reliance on detection and response tools, processes and operations at the server level”
- “Improved defense in depth, which complements existing tools and defense mechanisms”
Morphisec’s AMTD
Morphisec’s AMTD solution protects workstations, servers and workloads with a proactive, prevention-first approach. The technology uses polymorphism to move, change and obfuscate the runtime memory environment and other resources, creating a continually changing, unpredictable attack surface. It prevents vulnerability exploitation and interrupts the progression of cyberattacks, using lightweight skeleton traps to deceive attackers and stop the ability to gain persistence in target organizations.
This proactive approach stops attacks capable of bypassing other security controls, while enhancing the operational efficiency of security teams.
Morphisec’s AMTD key capabilities include:
- Anti-ransomware – Advanced ransomware prevention leveraging dedicated AMTD mechanisms for safeguarding against ransomware attacks, from early attack stages to the impact/encryption phase.
- Credential theft protection – Advanced credential theft protection leveraging AMTD for safeguarding against Infostealer/credential stealing attacks
- Enhanced cyber-resilience: Implementing AMTD to efficiently mitigate the costs associated with recovery from advanced, previously unknown evasive threats, thereby bolstering overall cyber defense strategy.
- Prevention-first security: Prevents threats without prior knowledge: signatures, behavioral patterns, or indicators of attacks (IoAs).
- Operational efficiency: Providing simple installation with negligible performance impact and no additional staffing requirements.
- Lower IT and security costs: Significantly reducing security analyst alert triage time and costs due to early prevention, exact threat classification and prioritization of high-risk alerts.
- Risk-based vulnerability prioritization for exposure management: Empowering organizations with continuous business context and risk-driven remediation recommendations, enabling effective prioritization of patching processes and reduced exposure with patchless protection, powered by AMTD.
- Flexible deployment: Offering a SaaS-based, multi-tenant and API-driven platform.
Morphisec AMTD in Action
Many recent blogs demonstrate how Morphisec and AMTD prevent a variety of threats. Some examples include:
- Citrix Bleed: A critical security flaw that has had a significant impact across various industries in the United States, including credit unions and healthcare services. In one recent blog post we called it “one of the most critical vulnerabilities of 2023.”
- Chae$ 4.1 and Chae$ 4: New Chaes Infostealer variants that features a multi-staged infection process, the ability to steal sensitive and financial– with the newer version including a unique attribution to Morphisec researchers.
- ALPHV/Blackcat ransomware attack on MGM resorts: Includes an analysis of tactics deployed by the threat actors, and how Morphisec’s anti-ransomware can prevent the attacks.
- GuLoader: This file downloader that has been used to distribute a variety of remote administration tool (RAT) malware, including NETWIRE, Agent Tesla, NanoCore, FormBook, and Parallax RAT.
- InvalidPrinter: This is a component of Aurora Stealer that makes its delivery stealthy and dangerous and is highly evasive. Compiled with Embarcadero RAD Studio, it targets endpoint workstations using advanced anti-VM (virtual machine) technique we describe in detail in this post.
Security leaders and practitioners can learn more about AMTD and access a complimentary copy of the Gartner Emerging Tech: Security — AMTD Transforms Endpoint Protection report here.
1 Gartner Emerging Tech: Security — AMTD Transforms Endpoint Protection, Lawrence Pingree, Rustam Malik, published 15 January 2024
2 Gartner Emerging Tech: AMTD Advances Proactive Cloud Defense, Mark Wah, Lawrence Pingree, Rustam Malik, published 02 January 2024
Gartner Disclaimer
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.





.png?width=571&height=160&name=iso27001-(2).png)