The ransomware attack that hit MGM Resorts International on September 10th captured headlines due to the company’s name recognition, reputational and customer impact, and the overall magnitude of business disruption the attack caused.
Three days earlier, another prominent resort, Caesars Entertainment, was hit by a cyber-attack. In response, Caesars reportedly paid an estimated $15 to $30 USD million ransom.
In the case of the MGM Resorts attack, current estimates peg business impact at:
- Approximately $80 million in lost revenue due to operational disruptions
- More than 36 hours of IT downtime
- Significant customer service impact (access to rooms, elevators, kiosks, gaming consoles etc.)
The attacks on MGM and Caesar — two of the largest casino companies in the world — highlight the sophistication of today’s threat actors and corresponding ineffectiveness of current tools and processes used to defend against sophisticated and advanced cyber-attacks.
On September 19, 2023, nine days after the MGM incident made headline news, MGM Resorts officially stated on X (formerly Twitter) that business had been fully restored.
Attack Overview Details
Morphisec researchers have created a possible attack flow based upon independent investigation and available data regarding:
- The threat actor group’s previously known and historical tactics;
- Available attack information;
- And the likely path that the attackers could have taken.
Threat actor: Researchers have linked ransomware groups ALPHV/Blackcat/Scattered Spider to the attacks on both MGM and Caesars, with ALPHV/Blackcat publicly claiming responsibility.
Persistency: The group (in their blog) referenced that they had persistency in the network and had gained super administrator privileges.
Backdoors: The ransomware was deployed post MGM locking out the network, which means that attackers had gained significant visibility of the network and had implanted backdoors across the network.
Data exfiltration: The group also claimed to exfiltrate data; attackers mentioned that they were sorting through the data and if any PII data was found they would then post evidence of the same.
Possible Attack Flow
SMS Spearphishing to target an administrator --> SIM Swapping -->Social Engineering IT Helpdesk to send MFA resetcode to SIM --> access to network --> Backdoors --> Recon --> Cred stealing (memory dumps) --> Lateral movement --> Encryption of ESXi Servers
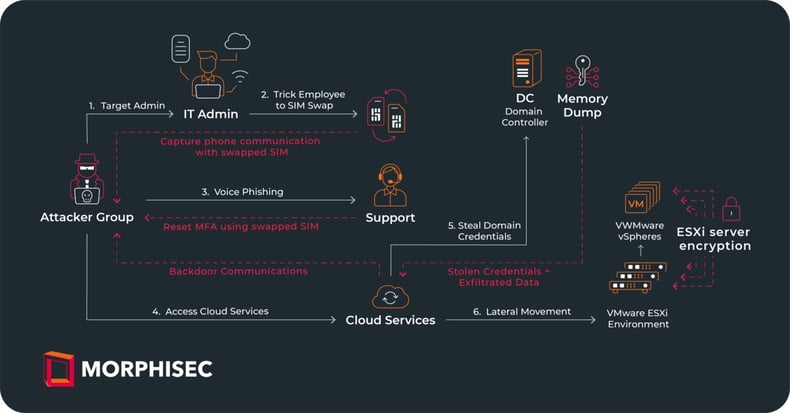
Based on details made available by the ransomware group and media agencies with visibility into the ongoing investigations, we believe the group targeted an MGM Resorts Administrator.
Morphisec's analysis suggest the attack took place over the following stages:
|
Infiltration: |
|
|
Persistency and Lateral Movement:
|
|
|
Exfiltration:
|
The adversary group in its statement mentioned: “We posted a link to download any and all exfiltrated materials up until September 12th, on September 13th in the same discussion.” “We are unable to reveal if PII information has been exfiltrated at this time. If we are unable to reach an agreement with MGM and we are able to establish that there is PII information contained in the exfiltrated data, we will take the first steps of notifying Troy Hunt from HaveIBeenPwned.com. He is free to disclose it in a responsible manner if he so chooses.” |
|
Impact Stage:
|
The group proceeded to encrypt about 100 ESXi servers once MGM decided to isolate critical assets post breach. The statement from the group stated: “After waiting a day, we successfully launched ransomware attacks against more than 100 ESXi hypervisors in their environment on September 11th after trying to get in touch but failing. This was after they brought in external firms for assistance in containing the incident.” |
Morphisec Analysis
A sophisticated group stealthily maintained its presence within the environment, and after gaining access exfiltrated sensitive data.
The attack trajectory is illustrated in the diagram below:
.jpeg?width=790&height=413&name=ezgif.com-gif-maker(21).jpeg) The highlighted stages depict where Morphisec's ransomware prevention would have provided early attack visibility by preventing the advanced in-memory backdoors, thus denying the attackers a foothold within the environment.
The highlighted stages depict where Morphisec's ransomware prevention would have provided early attack visibility by preventing the advanced in-memory backdoors, thus denying the attackers a foothold within the environment.
At the Credential Stealing stage, attackers took DC memory dumps for the purpose of obtaining domain admin rights. Here too, Morphisec AMTD Credential Stealing protection would have prevented the theft and attack, thus affording the team early visibility and rapid containment.
Internal and external resource inefficiencies were expressly indicated within the attack group’s blog. An excerpt is featured below:
“MGM implemented conditional restrictions that barred all access to their Okta (---) environment due to inadequate administrative capabilities and weak incident response playbooks.“
“After waiting a day, we successfully launched ransomware attacks against more than 100 ESXi hypervisors in their environment on September 11th after trying to get in touch but failing. This was after they brought in external firms for assistance in containing the incident.”
It appears that the MGM team were caught by surprise. In turn, MGM team efforts and responses to contain the attack led to confusion that manifested itself through a lack of incident preparedness and inadequate contingency procedures, exhibited since the attack apparently continued despite initial detection and response efforts.
For example, the rapid encryption of 100 ESXi servers and the effective downtime of more than 36 hours potentially indicates a network which was not segmented very well and lacked good backup and restoration practices.
Morphisec Threat Research and Incident Response Team General Takeaways
Morphisec recommends implementing the following best practices to prepare against this and similar future attacks:
- Contingency planning: Conduct simulation exercises for contingency planning.
- Process validation: Improve and verify backup and restoration procedures. Disciplined backup and restoration process validation is essential to incident recovery.
- Defense-in-Depth: Harden cybersecurity defenses through Automated Moving Target Defense (AMTD) as part of a robust defense-in-depth strategy. Automated Moving Target Defense (AMTD) introduces added complexity and attack cost for the threat actor, thereby providing an effective anti-ransomware solution and deterrent against attacks (read “Automated Moving Target Defense is the Future of Cyber—Gartner” for more information.)
- Improve segmentation: This Incident highlights the importance of segmenting the network architecture.
- IR framework and response alignment: IR framework and response practices must align practically with company operations and steps enacted to ensure employees are connected with such practices. This ensures a natural response to incidents where actions are planned, thoughtful and properly executed.
Interested in learning how Morphisec can secure your organization from this and similar attacks? Schedule a demo today.






.png?width=571&height=160&name=iso27001-(2).png)