To help protect the public, Morphisec Labs constantly monitors, investigates, and assesses the latest threats to help organizations avoid serious consequences. In recent months, threats involving infostealers have escalated. This report analyzes six of the top infostealers used this year.
An infostealer is a piece of malware that tries to steal your information, usually to make money from it. Threat actors often try to blackmail the victim, or just sell their stolen information on dark web forums or the black market. Standard infostealers steal login info like usernames and passwords, while more advanced infostealers (called keyloggers) can record every keystroke in your system. Infostealers usually email their stolen info to another system, or send it over a network.
Infostealers are often sold on dark web forums and as Malware-as-a-Service (MaaS). Threat actors typically use browser extensions, exploited websites, malicious attachments, and Google ads to deliver infostealers to their victims. (Morphisec’s revolutionary Moving Target Defense (MTD) technology effectively prevents these types of attacks.)
2022 Information Stealer Comparison
We arranged information stealers into comparable modules according to their characteristics and capabilities. This way we can more clearly see the differences and improvements offered by each stealer. The table below summarizes our finding while researching each of the stealers:
| Family |
Raccoon V1 |
RedLine Stealer |
Mars Stealer |
Raccoon V2 |
BlackGuard |
Jester Stealer |
| First seen |
2019 |
2020 |
2021 |
2022 |
2021 |
2021 |
| Price |
$75/7 days $200/30 days |
$150/month |
$140/month |
$275/month |
$200/month |
$99/month |
| Programming Language |
C\C++ |
C# (.NET) |
C\C++ |
C\C++ |
C# (.NET) |
C# (.NET) |
| Anti-CIS (Country Whitelisting) |
Supported. Stops if victim’s machine is in a post-Soviet (CIS) state. |
Supported. Custom blacklist. |
Supported. Stops if victim’s machine is in a post-Soviet (CIS) state. |
Not Supported. Looks for “ru” but doesn’t do anything if found. |
Supported. Stops if victim’s machine is in a post-Soviet (CIS) state. |
Not Supported. |
| Mutex Creation |
Supported. Hard-coded name |
Not Supported. |
Supported. Hard-coded name |
Supported. Hard-coded name |
Not Supported. |
Supported. Based on machine properties |
| Additional DLLs |
Zip file of many DLLs |
No need for additional DLLs. |
sqlite3.dll, freebl3.dll, mozglue.dll, msvcp140.dll, nss3.dll, softokn3.dll, vcruntime140.dll |
sqlite3.dll, freebl3.dll, mozglue.dll, msvcp140.dll, nss3.dll, softokn3.dll, vcruntime140.dll and nssdbm3.dll (not found) |
SQLite.Interop.dll |
Not Supported. No need for additional DLLs. |
| C2 Communication |
Direct communication through HTTP |
Direct communication through WCF |
Direct communication through HTTP |
Direct communication through HTTP |
Communication via Telegram API |
Communication via Tor proxy or Upload to AnonFiles |
| System Information Module |
Supported. |
Supported. |
Supported. |
Supported. |
Supported. |
Supported. |
| Screenshot |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
| Browsers Data Module |
Supported. Embedded configuration. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
| Extensions Module |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
| Crypto Wallets Module |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
| Grabber Module |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Embedded configuration. |
Supported. Embedded configuration. |
| Loader Module |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Configured by the server. |
Supported. Configured by the server. |
Not Supported. |
Not Supported. |
| Applications Data Module |
Not Supported. |
Supported. Steals Telegram, Discord, and Steam data. |
Supported. Steals Telegram data. |
Supported. Steals Telegram data. |
Supported. Steals Telegram, Discord, Pidgin, and more. |
Supported. Steals Telegram, Discord, Pidgin, and more. |
| Exfiltration method |
New folder is created and zipped before exfiltration. |
Not Supported. Fileless data exfiltration. |
New folder is created and zipped before exfiltration. |
Fileless data exfiltration. |
New folder is created and zipped before exfiltration. |
New folder is created and zipped before exfiltration. |
| Self Removal |
Supported. |
Not Supported. |
Supported. |
Not Supported. |
Not Supported. |
Supported. |
Next we provide a high-level overview of each stealer along with links to more in-depth analysis.
Mars Stealer
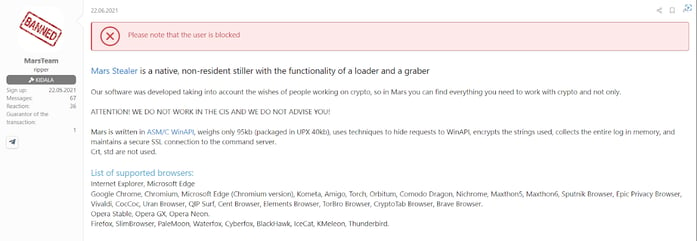 Translation of a Mars stealer post on a hacking forum
Translation of a Mars stealer post on a hacking forum
The Mars stealer first showed up for sale on hacking forums in July, 2021. It was later revealed to be derived from the Arkie stealers such as the Vidar and Oski stealers. Mars is improved over its predecessor, the Oski stealer, and continues to improve with each update. Morphisec covered the latest campaign to distribute the Mars stealer, which uses SEO techniques and fake websites that lure victims to download the malicious fake installer.
This malware can steal:
- Browser private information: profiles, auto fill information, credentials, cookies, and more
- Browser extensions including crypto wallet and 2FA extensions
- Crypto wallet software configuration information and wallet data
- Grabber functionality that steals whole files according to controlled regex
- On newer versions, data from instant messaging service Telegram
- Screenshot upon infection
This malware also has a Loader module enabling it to execute additional malware and additional commands.
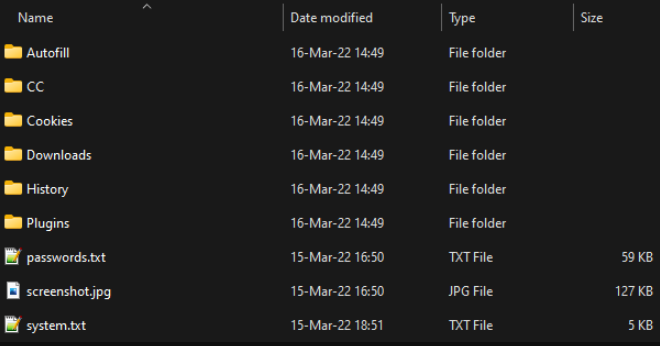 Folder containing stolen data
Folder containing stolen data
Price:
Standard version: $140/month
Extended version: $160/month
In-depth analysis of the Mars stealer can be found here and here.
Raccoon Stealer
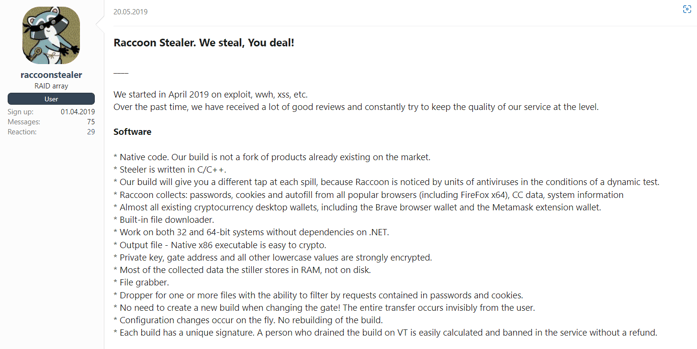
Translation of the first sale post for the Raccoon stealer
The Raccoon stealer was first observed in April 2019. Similar to Mars, Raccoon steals profiles, auto fill info, credentials, cookies, system information, browser extension data, crypto wallet data, etc.
The story of the Raccoon stealer took a turn in March 2022. After a key developer died in the Russian invasion of Ukraine, the people behind Raccoon suspended all activity.
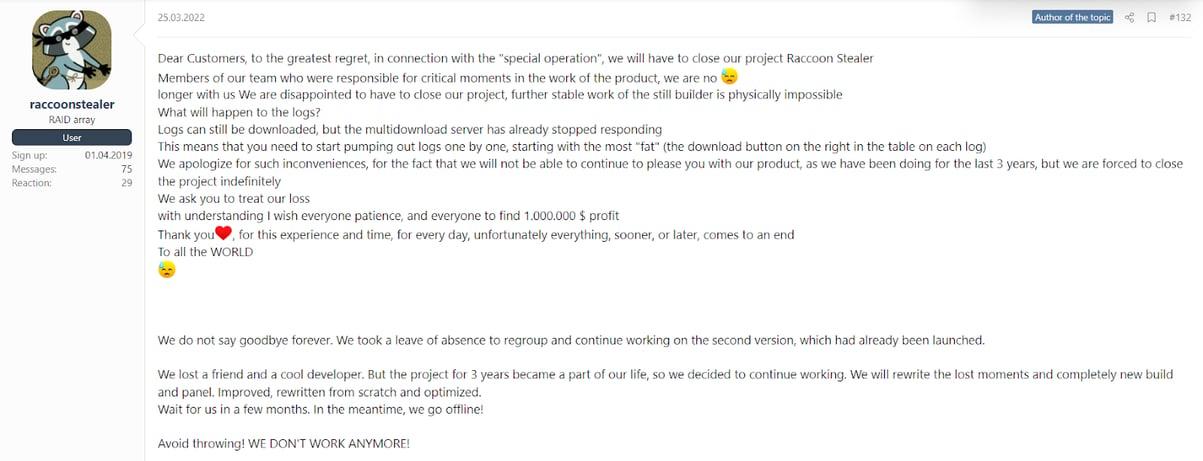 Translation of post advising all Raccoon stealer activities are suspended
Translation of post advising all Raccoon stealer activities are suspended
However, the S2W blog reported Raccoon has now developed a new version, released on June 9 2022, that offers new functionality:
- Fileless data exfiltration. The first version stored stolen data on disk before exfiltration. The new version sends the data directly after stealing it.
- Telegram data stealer support. The new version has a module that steals Telegram data.
- New configuration format
Morphisec Threat Labs found the new Raccoon stealer to be very similar in functionality to other stealers derived from the Arkie stealer, such as the Mars stealer.
The Vidar, Oski, and Mars stealers are loaded with the following additional, legitimate DLLs:
- freebl3.dll
- mozglue.dll
- msvcp140.dll
- nss3.dll
- softokn3.dll
- vcruntime140.dll
- sqlite3.dll
Each of these was downloaded from a separate link. However, the first version of Raccoon, which also required additional, legitimate DLLs, downloaded a zip file containing many more DLLs:
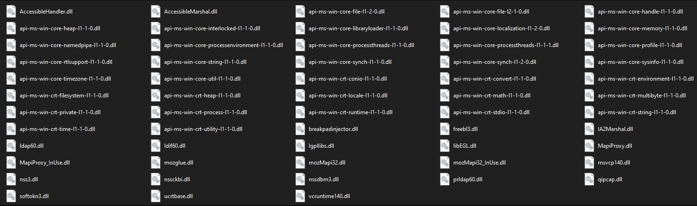 DLLs downloaded by Raccoon Stealer V1
DLLs downloaded by Raccoon Stealer V1
The Raccoon stealer V2 offers the same DLL loading as the Vidar, Oski, and Mars stealers:
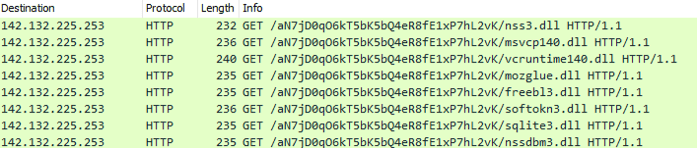 DLLs downloaded by the Raccoon stealer V2
DLLs downloaded by the Raccoon stealer V2
As mentioned, the Raccoon Stealer V2 has a new module that, like the Mars stealer, steals Telegram data.
![]() The Telegram module’s configuration
The Telegram module’s configuration
The configuration’s value is split by “|” and represents:
- A Telegram folder
- Regex for files to look for
- Regex for files to ignore
This raises the question: Are these two stealer operators connected? Perhaps sharing code bases or knowledge? The answer will likely remain unresolved.
An in-depth analysis of the Raccoon stealer can be found here and here.
RedLine Stealer
Translation of the first sale post for the RedLine Stealer
The RedLine stealer was first observed in hacking forums on February 19, 2020. Its reputation and popularity have risen considerably since then—it’s now one of the most popular and widely recommended information stealers on the market. (Threat actors have used Google PPC ads to distribute it.) RedLine stealer is written in C# and continues to be updated by its operators, with the latest version, v23.1, released on May, 9, 2022. RedLine is capability- and feature-rich, which explains why it’s so widely used. Features include:
- System information collection
- Anti-analysis techniques
- Collection of browser information and extension data such as passwords, autofills, etc.
- Collection of crypto wallet data from disk and browser extensions
- Collection of FTP and IM clients data
- Collection of files from application such as Telegram, Discord, Steam, and VPNs
- Grabber module for stealing files according to white- and black-lists
Price:
Lite version: $150/month
Pro version: $900/lifetime
An in-depth analysis of the RedLine stealer can be found here.
BlackGuard Stealer
Translation of the first sale post for the BlackGuard stealer
BlackGuard is an info stealer written in C#. It first appeared and sold on the black market in March 2021. There have been several versions since then, with the latest released in March 2022. The BlackGuard authors admitted it’s a fork of the open source information stealers StormKitty and
44CALIBER. They took parts from each project and added new functionality, resulting in the BlackGuard stealer. For example, the exfiltration module is taken from StormKitty via Telegram, rather than from 44Caliber via Discord.
The BlackGuard team doesn’t offer distribution for their malware, so buyers must choose their own method of distribution. The latest examples for delivering this stealer include: cracked software, fake Windows updates, YouTube videos, etc.
BlackGuard capabilities include:
- Collects user data from Telegram, Discord, and Steam
- Collects sensitive data from FTP and VPN applications
- Collects private browser information: passwords, auto fill information, cookies, and history
- Collects crypto wallet software configuration information and wallet data
- Grabber functionality for specific file types in specific paths
- Collects the infected machine’s information
BlackGuard stores its stolen information in a folder named ChikenDir, compresses the folder, and exfiltrates the folder via a Telegram API.
Price:
One month: $200
Lifetime subscription: $700
An in-depth analysis of the BlackGuard stealer can be found here.
Jester Stealer
The first sale post for the Jester Stealer
The Jester stealer was first introduced in July 2021 and has received several updates since then. The latest update occurred in January 2022 and features bug fixes and improvements.
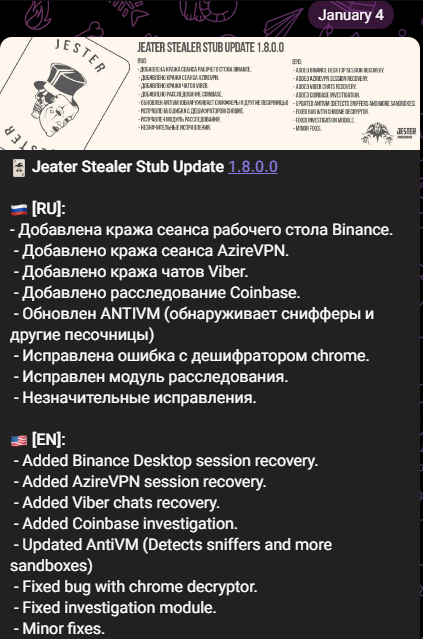
A post on the Jester Stealer’s official Telegram channel
The Jester stealer was recently used in a campaign against Ukrainian entities. It was distributed via Malspam with a “chemical attack” theme that lured victims to download an Excel document. Once the document is downloaded, opened, and the user activates a macro, the Jester Stealer is downloaded and executed.
The stealer is written in C# and, per their message, offers the following functionality:
- Collection of browser data: passwords, CC, cookies, Autofill info, history, bookmarks from 20+ browsers
- Session and sensitive files from messenger apps such as: Telegram, Discord, Pidgin, etc.
- Collects info from cryptocurrency extensions
- Collects info from gaming software sessions: Steam, Twitch, etc.
- Collects info from password managers: LastPass, KeePass, BitWarden, etc.
- Collects info from VPN and FTP clients
Price:
One month: $99
Lifetime subscription: $249
An in-depth analysis of the Jester stealer can be found here.
Don’t Let an Infostealer Compromise Your Network
Infostealer attacks are increasing and can be extremely damaging to any organization. This post examined six of the more threatening and dangerous ones. An infostealer is often used as the first step in an attack chain that can lead to ransomware and other extremely damaging threats.
Morphisec’s Moving Target Defense (MTD) technology is designed to prevent these types of attacks, stopping them before they can cause financial impacts, lawsuits, and brand damage. To learn more about Morphisec MTD for endpoints and servers, read the white paper, Zero Trust + Moving Target Defense: The Ultimate Ransomware Strategy.



.png?width=1080&name=moving-target-defence-ebook-large%20(1).png)

.png?width=571&height=160&name=iso27001-(2).png)