As of January 10th 2023, Windows 7, Windows 8, 8.1, their Windows embedded derivatives, and Windows Server 2008 R2 will no longer receive patches from Microsoft. Millions of devices will now become "legacy" and create a suite of new legacy security...
Read MoreDuring November, Morphisec identified a brand-new variant of Babuk ransomware while investigating a customer's prevention event. Babuk was first discovered at the beginning of 2021, when it began targeting businesses to steal and encrypt data in...
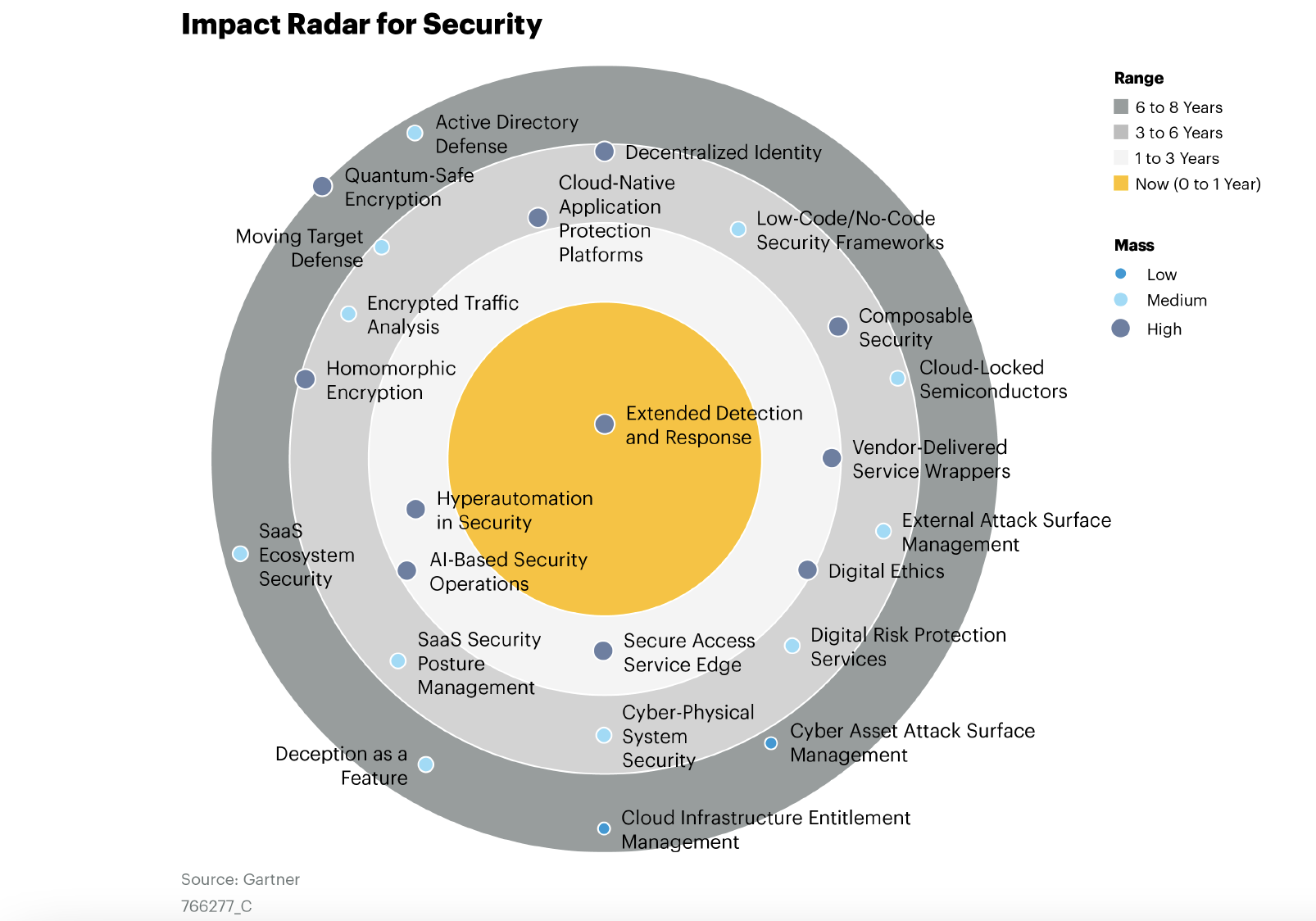
Read MoreFor the second consecutive year, Gartner has highlighted Moving Target Defense (MTD) as a featured technology, and Morphisec as a Sample Vendor for the technology in their report, Emerging Tech Impact Radar: Security. The authors define MTD as “......
Read MoreOn a scale of one to ten, how effective is the status quo approach to server security?In theory, it should be ten. The path to keeping servers protected from the outside world (segmentation, firewalls, vulnerability patching, security solutions...
Read MoreThe evidence is clear that despite expanding cybersecurity investment, sophisticated cyberthreats are increasingly successful. Household brands like Uber and Apple, essential service providers like Colonial Pipeline, and even entire nation states...
Read More“When,” not “if.” For financial cybersecurity teams, dealing with regular cyberattacks is part of the job. Almost 23 percent of all cyber attacks were aimed at financial institutions in 2021. And 63 percent of financial institutions experienced an...
Read MoreI recently came across a report about the Internet of Things (IoT) submitted to the United States President by his National Security Telecommunications Advisory Committee. It examines the challenges of securing IoT devices in depth. The report’s...
Read MoreWhat is the benefit of a Defense-in-Depth (DiD) approach? From the Punic Wars to WW2, history shows that when you have multiple layers of defense, even the most motivated and well-resourced attackers will struggle to breach the final objective....
Read MoreCyber security solutions like next generation anti-virus (NGAV), endpoint detection and response (EDR), and endpoint protection platform (EPP) face abuse, tampering, and exploitation to achieve initial access and persistence. Threat actors know it's...
Read MoreToday, threat and vulnerability management is more critical than ever, with unpatched vulnerabilities involved in 60 percent of data breaches. Vulnerability tools of all stripes abound, yet for all their features, few offer a clear path to action....
Read MoreA doctor might describe the condition of cybersecurity in healthcare 2022 as "critical." In a little over two years, healthcare IT has seen a decade's worth of changes. From a security point of view, most have been for the worse.
Read MoreThe DoNot Team (a.k.a APT-C-35) are advanced persistent threat actors who’ve been active since at least 2016. They’ve targeted many attacks against individuals and organizations in South Asia. DoNot are reported to be the main developers and users...
Read MoreIn the last couple of years, security teams in large enterprises and high-profile government organizations have increasingly experienced a new form of attack. This attack leverages the supply chain of an organization’s software ecosystem (and less...
Read MoreOn the dark web, private health information (PHI) sells for up to $1,000 per record. In response to surging healthcare cyberattacks, it's now glaringly obvious that data security in healthcare needs to go in a new direction.
Read MoreIn the last few years, organizations in every sector have witnessed a clear shift in the threat landscape. Although the number and frequency of all kinds of cyberattacks increased, ransomware in particular has undergone extremely rapid evolution....
Read MoreTo help protect the public, Morphisec Labs constantly monitors, investigates, and assesses the latest threats to help organizations avoid serious consequences. In recent months, threats involving infostealers have escalated. This report analyzes six...
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (126)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Financial Cybersecurity (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)






















.png?width=571&height=160&name=iso27001-(2).png)