When it comes to endpoint security, Microsoft Defender for Endpoint stands out as a popular choice. It's the fastest-growing endpoint protection platform, boasting over 19% market share, and for good reason — Microsoft Defender for Endpoint provides...
Read MoreMorphisec announced the launch of the Anti-Ransomware Assurance Suite to help organizations pre-emptively reduce exposure to cyber risk, proactively prevent advance threats and ensure optimal anti-ransomware defense. Powered by Automated Moving...
Read MoreGlobally, ransomware is big business, with millions of attacks targeting organizations every day. Not every attack is financially successful, but with keen attention to detail, attackers have (and continue to) tune tactics, making ransomware a...
Read MoreRecently, Morphisec Labs identified a significant increase in activity linked to Mispadu (also known as URSA), a banking trojan first flagged by ESET in 2019. Initially concentrated on LATAM countries and Spanish-speaking individuals, Mispadu has...
Read More(Updated March 29th, 2024)
The National Vulnerability Database (NVD) has long been a crucial resource for organizations in managing their vulnerability lifecycle and ensuring the security of their systems. However, recent developments have...
Read MoreGartner released two reports this month including Gartner® Emerging Tech: Security — AMTD Transforms Endpoint Protection1and Gartner Emerging Tech: AMTD Advances Proactive Cloud Defense 2 report, which each feature Morphisec as a sample vendor.
Read MoreFor the first time, Automated Moving Target Defense (AMTD) has been included in the 2023 Gartner Hype Cycle for Endpoint Security as a technology in the ‘on the rise’ category. Morphisec is named as a Sample Vendor in the AMTD category. “This Hype...
Read More“If an attacker successfully hacks our workstations or trading terminals, they’d have full access to the firm’s critical infrastructure.” This quote from a Chief Information Security Officer at a leading US-based hedge fund shines a light on the...
Read MoreIn today’s threat landscape, multiple defense-in-depth layers are one of the only ways security teams can achieve peace of mind. Why? Two reasons stand out:
Read MoreCyberattacks targeting critical OT and industrial organizations rose by 87% last year—the threat level to OT is higher than ever, and threat actors are finding new ways to compromise OT environments.
Read MoreMorphisec has been recognized as a sample vendor in Gartner’s Emerging Tech: Security — Emergence Cycle for Automated Moving Target Defense Report—research covering groundbreaking security technologies that according to Gartner, “are paving the way...
Read MoreThere’s now a new ransomware attack, on average, every 10 seconds. Threat actors have become powerful and sophisticated enough to successfully hold national governments—such as Ireland and Costa Rica—to ransom.
Read MoreFew executives doubt their organizations must pay more attention to cybersecurity. Cybercrime costs were estimated at $8.4 trillion globally in 2022 alone, and could exceed $20 trillion by 2026. No organization can afford to ignore this risk.
Read MoreMorphisec has recently identified a highly evasive malware campaign delivering ProxyShellMiner to Windows endpoints.
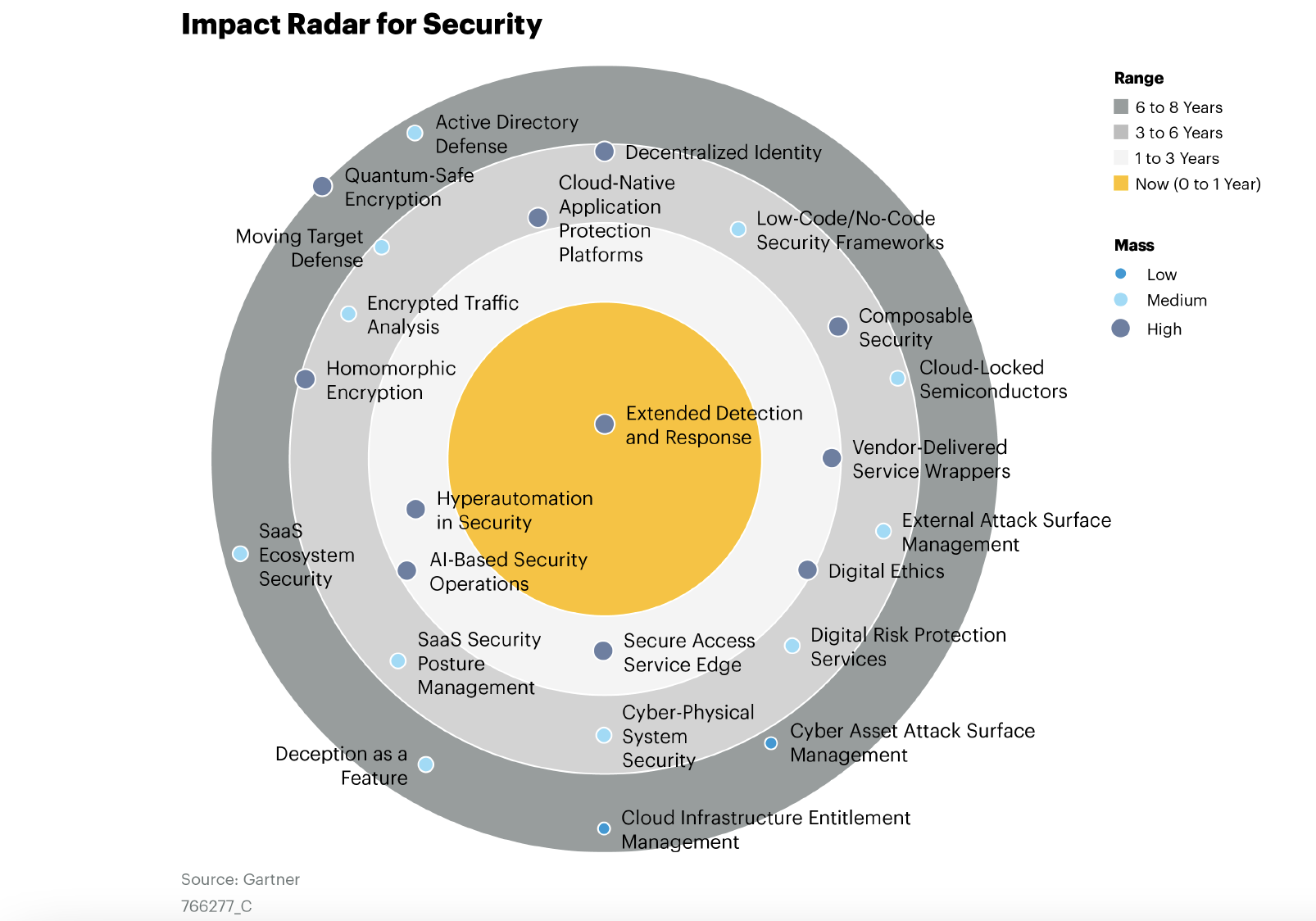
Read MoreFor the second consecutive year, Gartner has highlighted Moving Target Defense (MTD) as a featured technology, and Morphisec as a Sample Vendor for the technology in their report, Emerging Tech Impact Radar: Security. The authors define MTD as “......
Read MoreOn a scale of one to ten, how effective is the status quo approach to server security?In theory, it should be ten. The path to keeping servers protected from the outside world (segmentation, firewalls, vulnerability patching, security solutions...
Read MoreThe evidence is clear that despite expanding cybersecurity investment, sophisticated cyberthreats are increasingly successful. Household brands like Uber and Apple, essential service providers like Colonial Pipeline, and even entire nation states...
Read MoreSearch Our Site
Recent Posts
Posts by Tag
- Automated Moving Target Defense (157)
- Threat Research (135)
- Cyber Security News (132)
- Morphisec Labs (124)
- Morphisec News (54)
- Adaptive Exposure Management (14)
- Defense-in-Depth (13)
- Ransomware (12)
- Preemptive Security (11)
- Gartner (10)
- Continuous Threat Exposure Management (CTEM) (9)
- Microsoft (8)
- In-Memory Attacks (7)
- Healthcare Cybersecurity (6)
- Advanced Threat Defense (5)
- Legacy Security (5)
- Artificial Intelligence (4)
- Financial Cybersecurity (4)
- Linux Cybersecurity (4)
- Fileless Malware (3)
- Threat and Vulnerability Management (2)
- Managed Service Providers (1)






















.png?width=571&height=160&name=iso27001-(2).png)