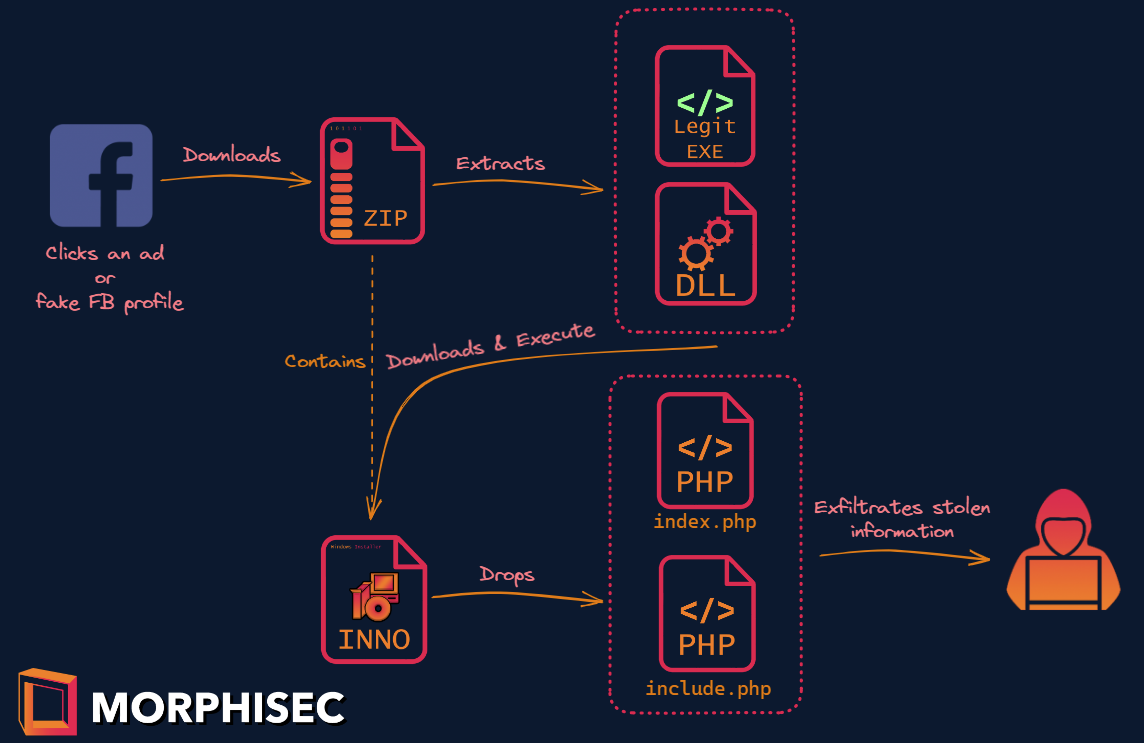
Exclusive: Morphisec Threat Labs identified Chae$ 4, an advanced and previously unknown variant of the Chaes malware. Read this post for an abstract of the findings.
Download the full Chae$ 4 technical analysis containing exclusive details of the...
Read More






















.png?width=571&height=160&name=iso27001-(2).png)